Daniel Genkin
@danielgenkin
Associate Professor at Georgia Tech. Security, systems, side channels, cryptography.
ID: 1029963330876841990
https://faculty.cc.gatech.edu/~genkin/ 16-08-2018 05:29:28
13 Tweet
273 Takipçi
172 Takip Edilen

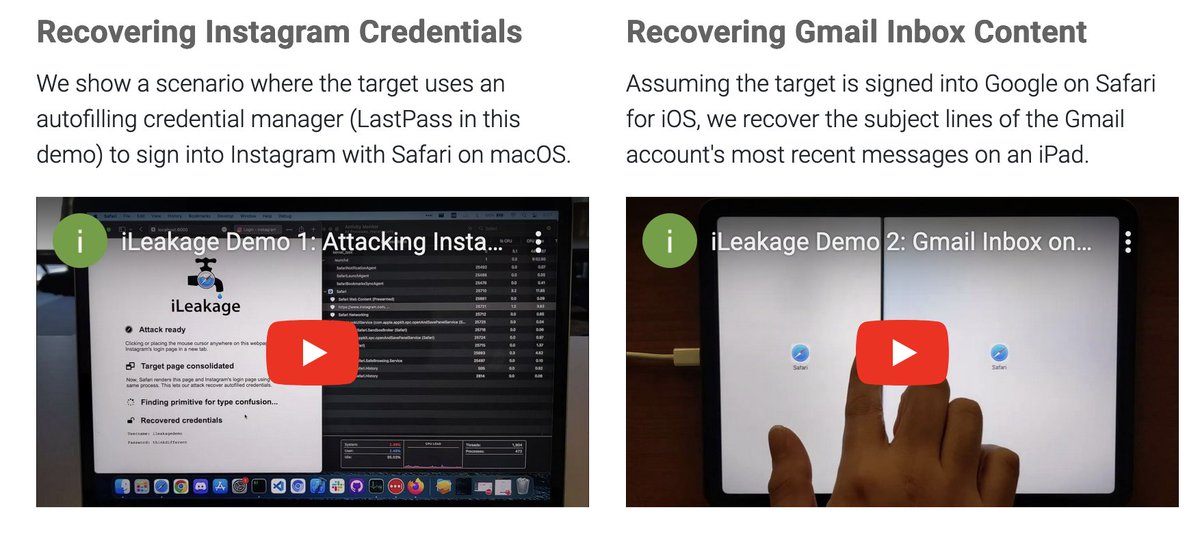
After more than a year of embargo we can now show you how speculative attacks can extract sensitive information from the Safari browser on Apple platforms. Check out our latest paper ileakage.com. Great work by Jason Kim, Stephan van Schaik and Yuval Yarom.






WOOT! Big news! Starting 2024 WOOT will be @USENIX WOOT Conference on Offensive Technologies! WOOT '24 will be on August 12-13 2024, colocated with USENIX Security WOOT '24 will be co-chaired by Alyssa Milburn (Intel) and Adam Doupé (Arizona State University <= corrected!) usenix.org/conference/woo…



I'm very thankful to the Sloan Foundation for recognizing my research. Could not have done it without my awesome students, great collaborators, and wonderful mentors. Checkout our research group that made this possible at architecture.fail

Ever wondered what happens when side-channel resistant code meets a fancy prefetcher? Checkout our paper breaking constant time crypto on Apple CPUs. gofetch.fail Joint work with Boru Chen, yingchen wang, Pradyumna Shome (pradyumna.bsky.social), Chris Fletcher, David Kohlbrenner, Riccardo Paccagnella


Excited to present "Pathfinder: High-Resolution Control-Flow Attacks Exploiting the Conditional Branch Predictor" at ASPLOS with Archit Agarwal, Max Christman, Christina Garman, Daniel Genkin, Andrew Kwong, Daniel Moghimi, Deian Stefan, Kazem Taram and Dean Tullsen. (1/4)🧵

Have an Apple device from the last few years? We have a new side channel attack for you. Checkout our work at predictors.fail Joint work with Jason Kim, Jalen Chuang and Yuval Yarom (Yuval Yarom). Could not have asked for a better team!