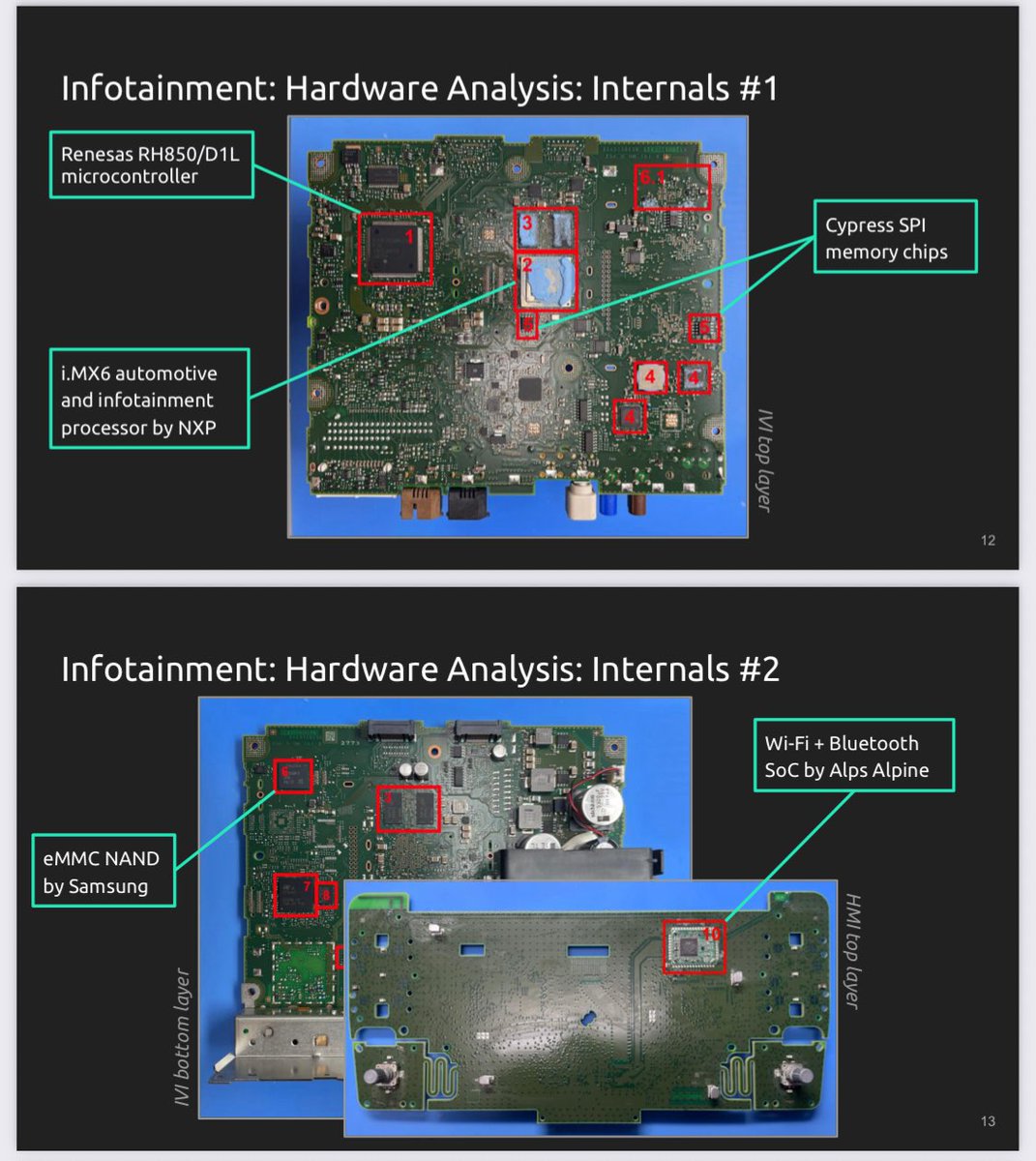
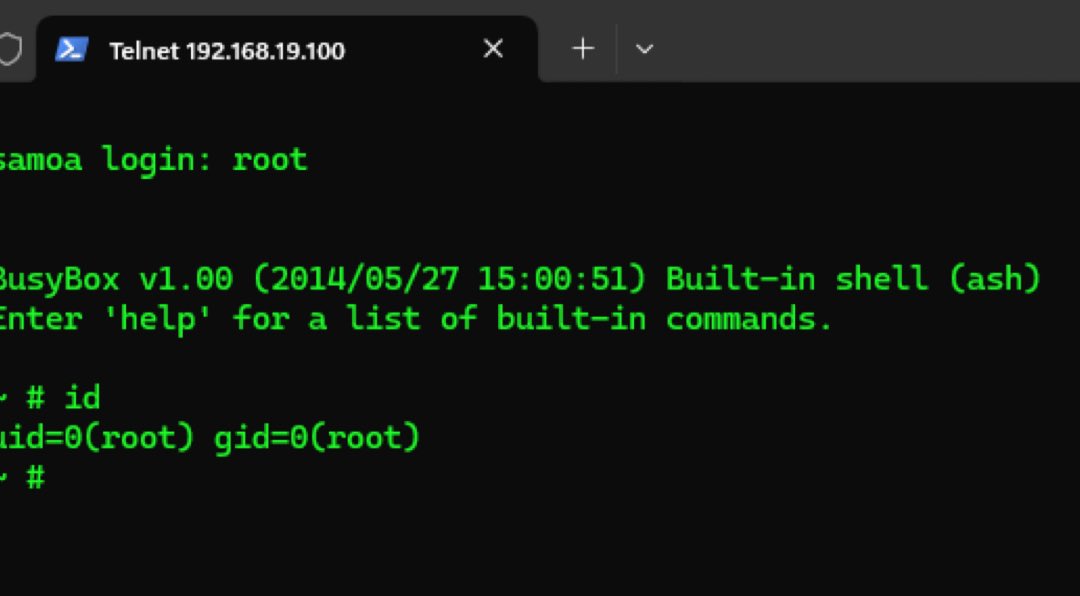
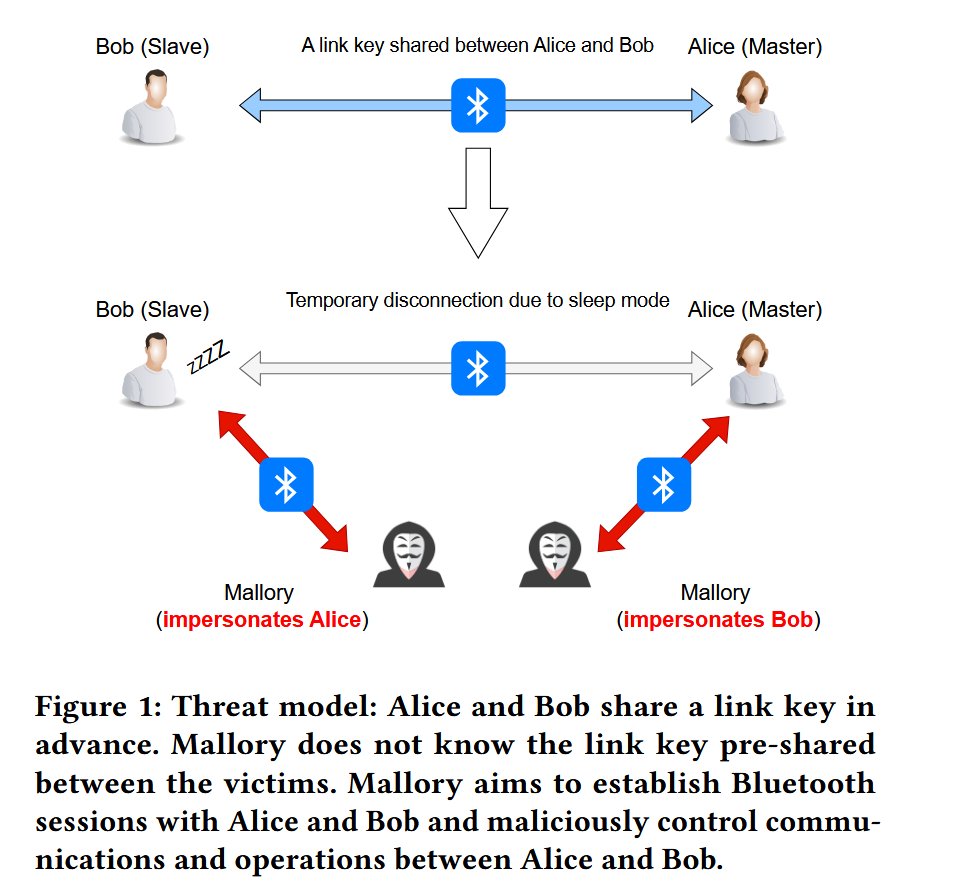
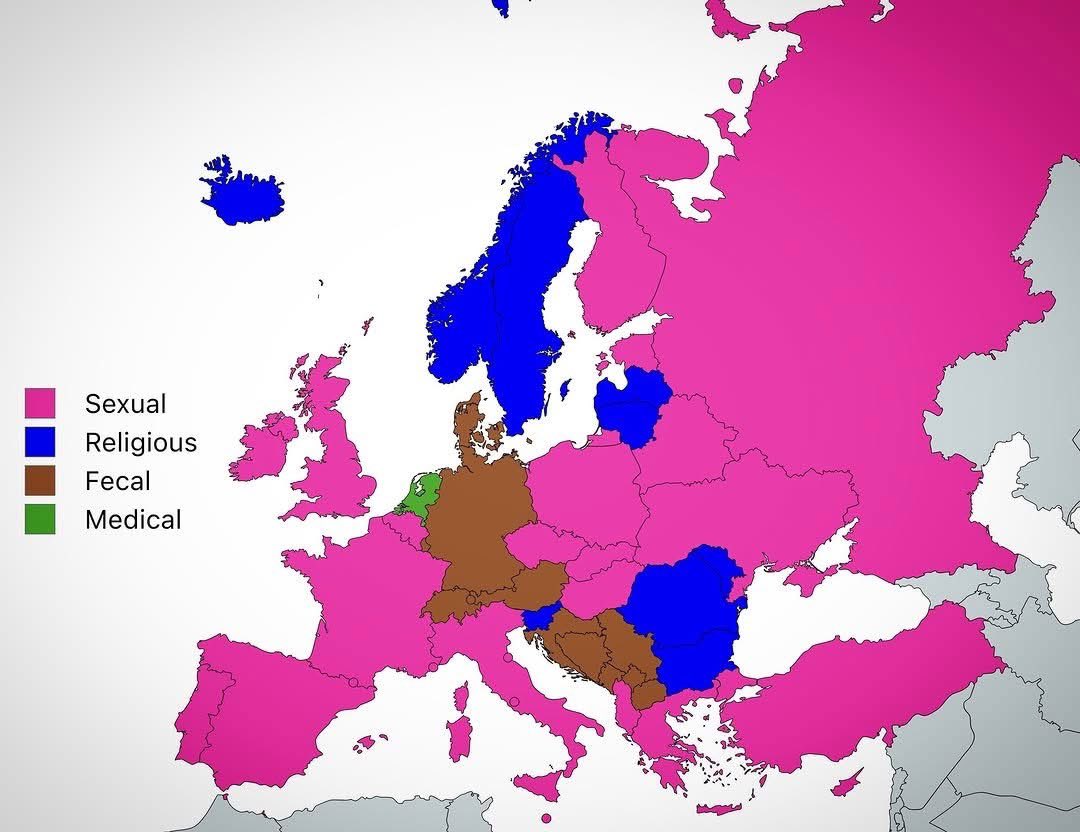
Luca Bongiorni
@cyberantani
Need a seasoned 🇮🇹#Hacker to setup a #CyberLab or #HackersDreamTeam for conducting Applied Security R&D or ProdSec activities❓😎👉Also on BSKY👈😎
ID: 495744568
http://cyberantani.bsky.social 18-02-2012 08:26:11
11,11K Tweet
6,6K Takipçi
2 Takip Edilen