crep1x
@crep1x
Lead cybercrime analyst, tracking adversaries activities & infrastructure, at @sekoia_io
ID:624192041
01-07-2012 23:52:17
574 Tweets
2,1K Followers
292 Following


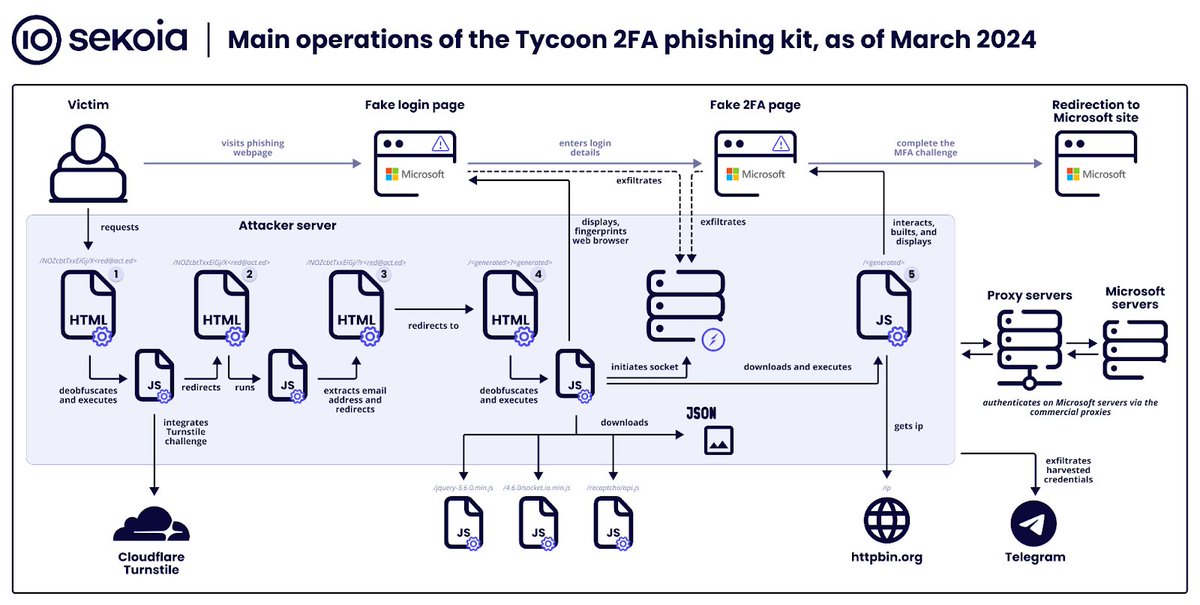
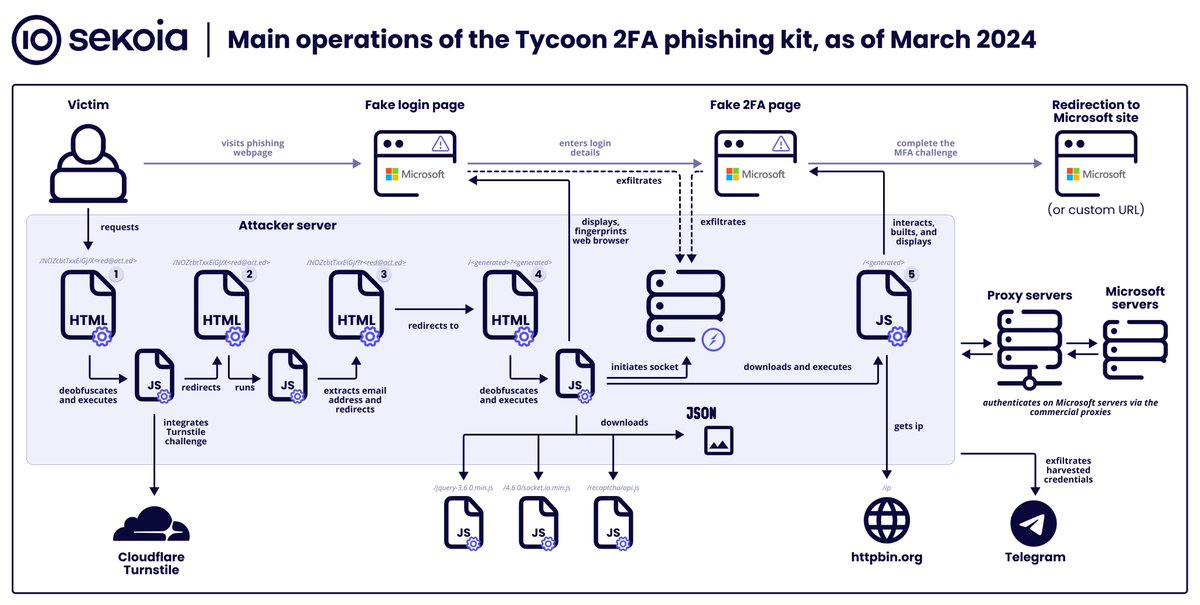
New MFA-bypassing phishing kit targets Microsoft 365, Gmail accounts - Bill Toulas
bleepingcomputer.com/news/security/…
bleepingcomputer.com/news/security/…




🤝For the last months, our World Watch team collaborated with Sekoia.io TDR team to investigate and demystify Residential Proxies #RESIP and highlight their systemic growth and the transparency issues surrounding their sourcing ⤵️
orangecyberdefense.com/global/blog/re…
#cti Orange Cyberdefense