CloudBreach
@cloud_breach
🌩️ Empowering You to Defend Against Cloud Breaches 🌩️
ID: 1478753923263614977
http://cloudbreach.io/ 05-01-2022 15:43:39
597 Tweet
3,3K Takipçi
66 Takip Edilen




🌐🔒 Cybersecurity Awareness Month is here 🔒🌐 A huge THANK YOU to our amazing sponsors of 2025 who enabled us to bring Cloud Village across conferences like DEF CON RSAC BSidesCharm BSidesSF and Out Of The Box Security Conference 💜 Your support empowers our talks, workshops, CTFs & labs and









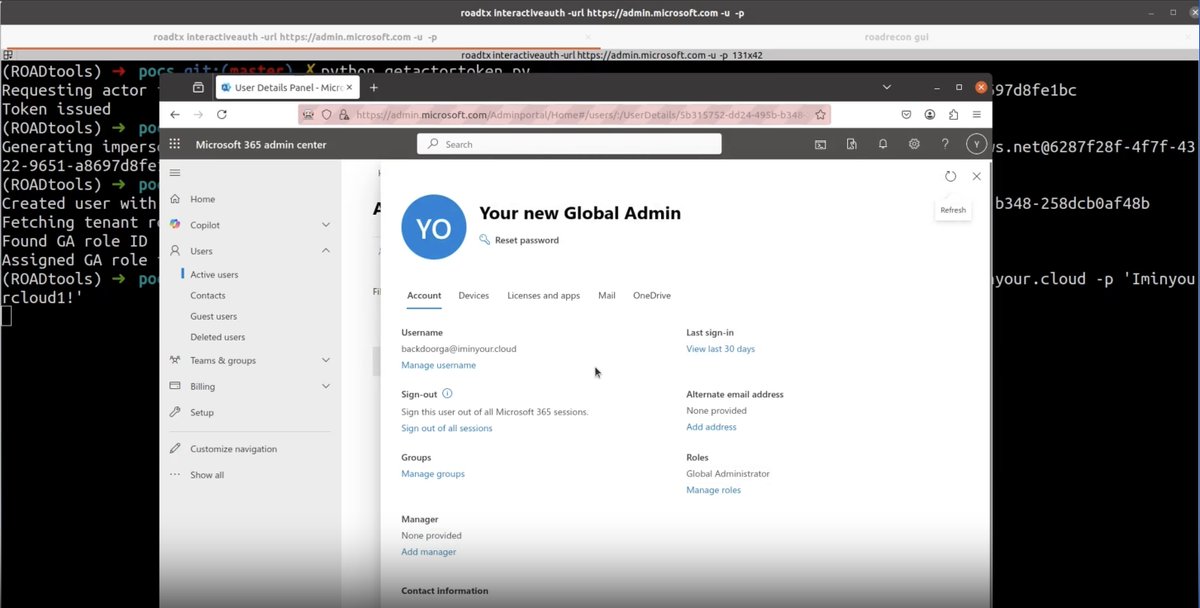
🛠️🧰 NoPrompt by NotSoSecure | Part of Claranet Cyber Security - #Azure CAP testing tool 🔎 Checks for password-only access to Microsoft Entra ID / Azure AD (MFA gaps) 🌐 Simulates OAuth2 & web logins across multiple device user-agents 🧩 Tests Microsoft Graph, AAD Graph, and Service Management APIs ⚖️




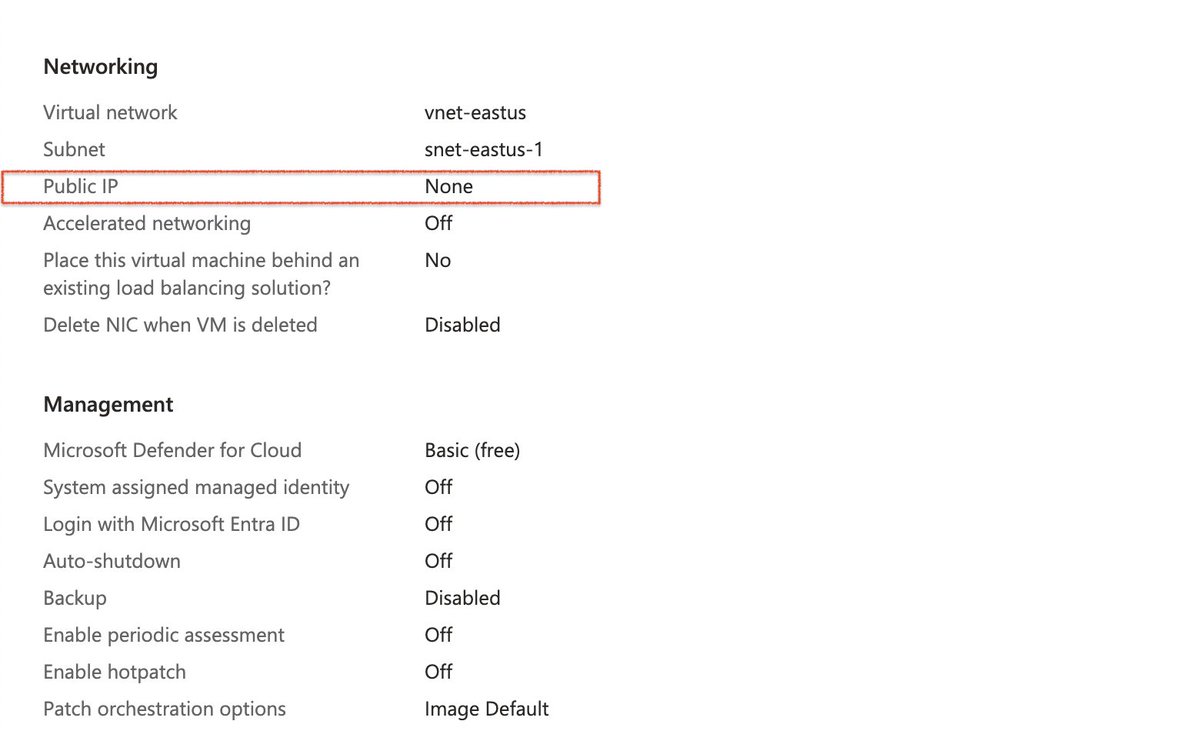
🔓💾 4TB SQL backup exposed online by EY 😱 Even the Big Four — proof that no org is too big for a simple cloud misconfig to burn them 👀 Key takeaways: 🔎 Discovered by NeoSecurity 🗄️ Full MSSQL .bak file publicly accessible 📁 Contained schema, customer, financial and