clearseclabs
@clearseclabs
Clear Security, Training, and Solutions
Check out website for latest course offerings.
ID: 1707102812851580928
https://www.clearseclabs.com 27-09-2023 18:40:31
110 Tweet
68 Takipçi
1 Takip Edilen










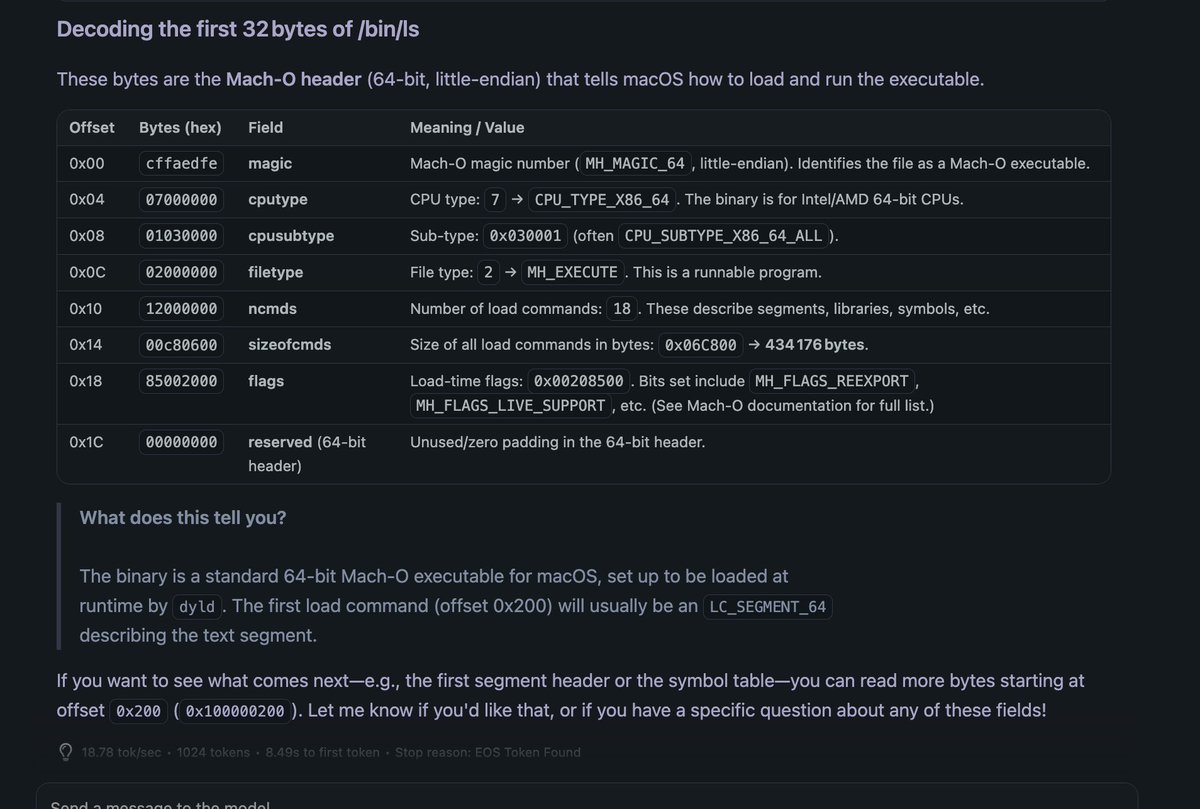
pyghidra-mcp: headless Model Context Protocol (MCP) server for Ghidra Blog post: clearbluejar.github.io/posts/pyghidra… Repository: github.com/clearbluejar/p… Credits clearbluejar #infosec


pyghidra-mcp from clearbluejar 🔥 youtube.com/watch?v=oWCiRQ…

pyghidra-mcp: headless Model Context Protocol (MCP) server for Ghidra by clearbluejar Blog post: clearbluejar.github.io/posts/pyghidra… Repository: github.com/clearbluejar/p… #infosec





John (clearbluejar) already uncovered what Apple fixed in CVE-2025-43400 on iOS/macOS 26.0.1 🍎🐛🔬🧠 And at #OBTS v8 he’ll show exactly how, with case studies, in his talk: “Reverse Engineering Apple Security Updates” Patch first, then make sure not to miss his #OBTS talk!


At #OBTS John McIntosh (clearbluejar) from clearseclabs demo’d his pipeline that uses AI, ipsw and ghidriff to auto-extract and diff Apple firmware — rapidly reveals real code changes behind Apple security fixes and to get actionable root-cause intel. Super clever stuff!