Christian Studer
@chrisred_68

The awesome FluxFingers Capture The Flag (CTF) competition is held prior to the conference, enabling participants to fully enjoy both the conference and its talks. For more details about the CTF: 2023.hack.lu/ctf/ #conference #hacklu #ctf #fluxfingers



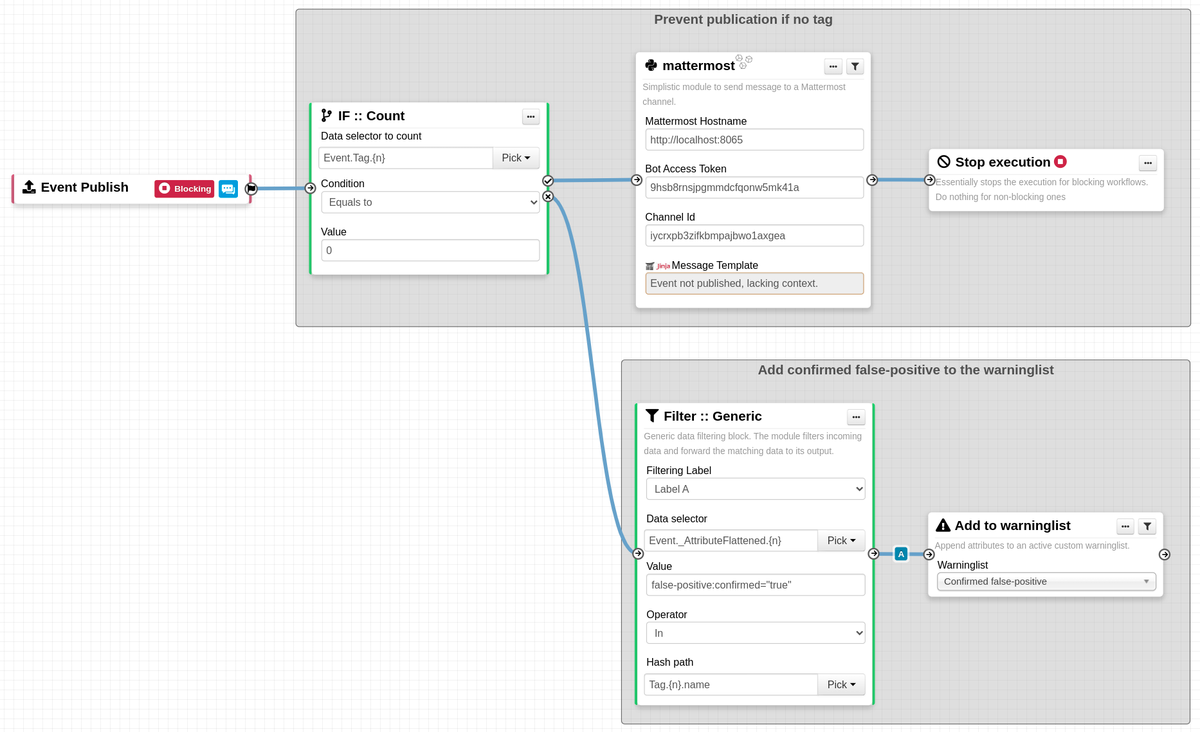
There's a new MISP (@[email protected]) playbook that shows how to create users and organisations, get user logs and create large number of users at once (fe. for trainings). All with PyMISP. github.com/MISP/misp-play…) , inspired by misp_control from Sascha Rommelfangen github.com/rommelfs/misp_…
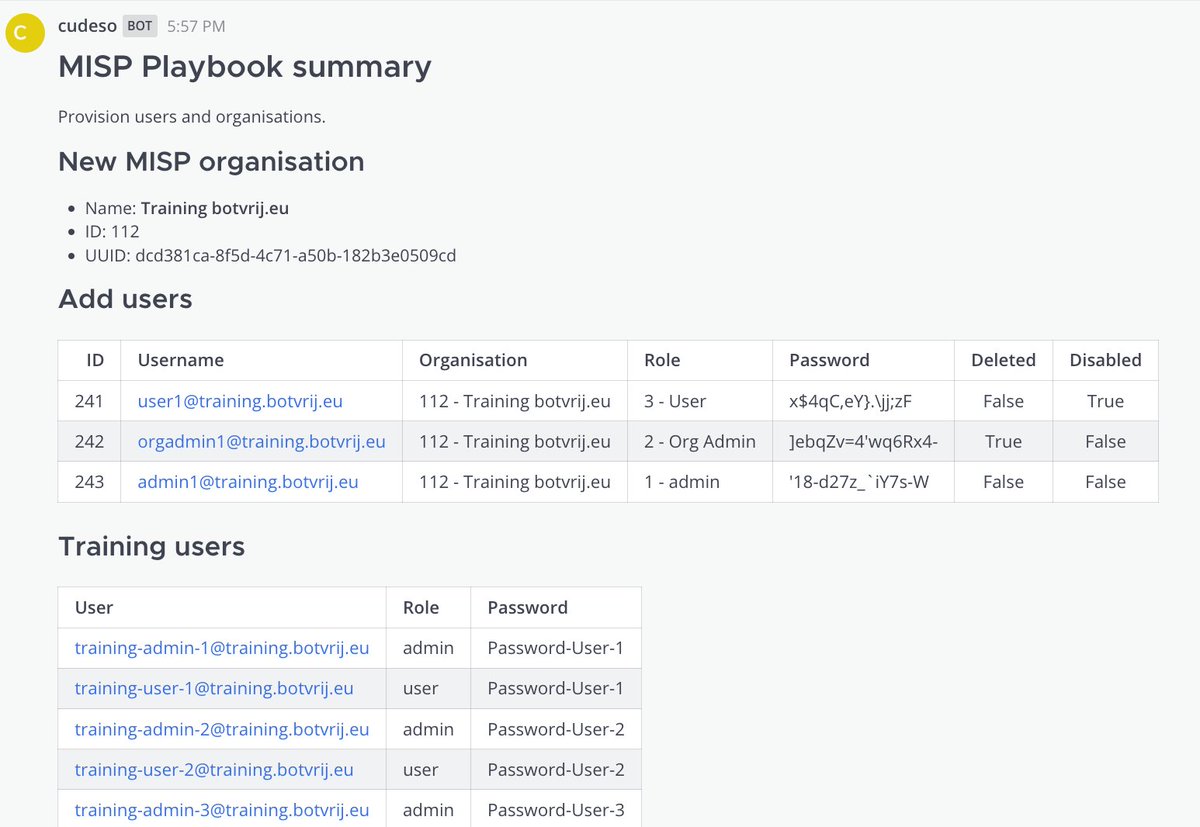

Use the "MISP playbook on Kali" documentation to deploy MISP (@[email protected]) playbooks on a Kali VM, for example during an incident investigation. github.com/MISP/misp-play…
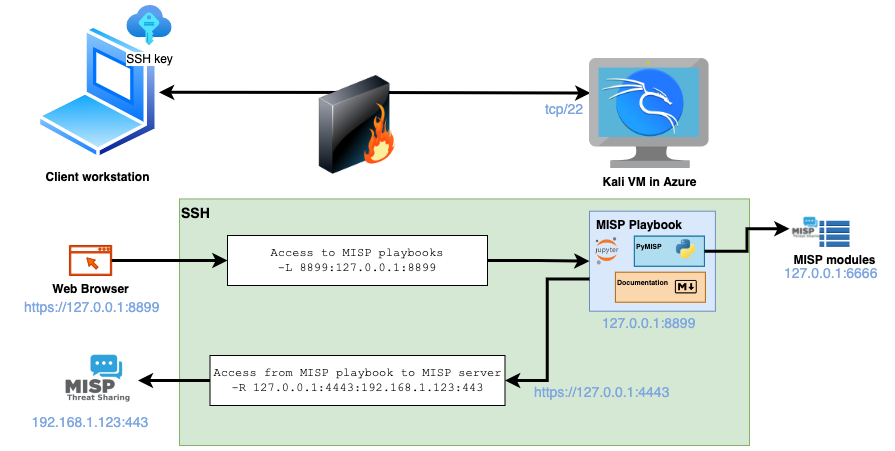


I shared the MISP (@[email protected]) playbook for malware triage that I regularly use for a first assessment on new samples. It uses MISP, VirusTotal , MalwareBazaar, Hashlookup and pefile, uploads to MWDB and alerts to Mattermost. #csirt #ir #dfir github.com/MISP/misp-play…


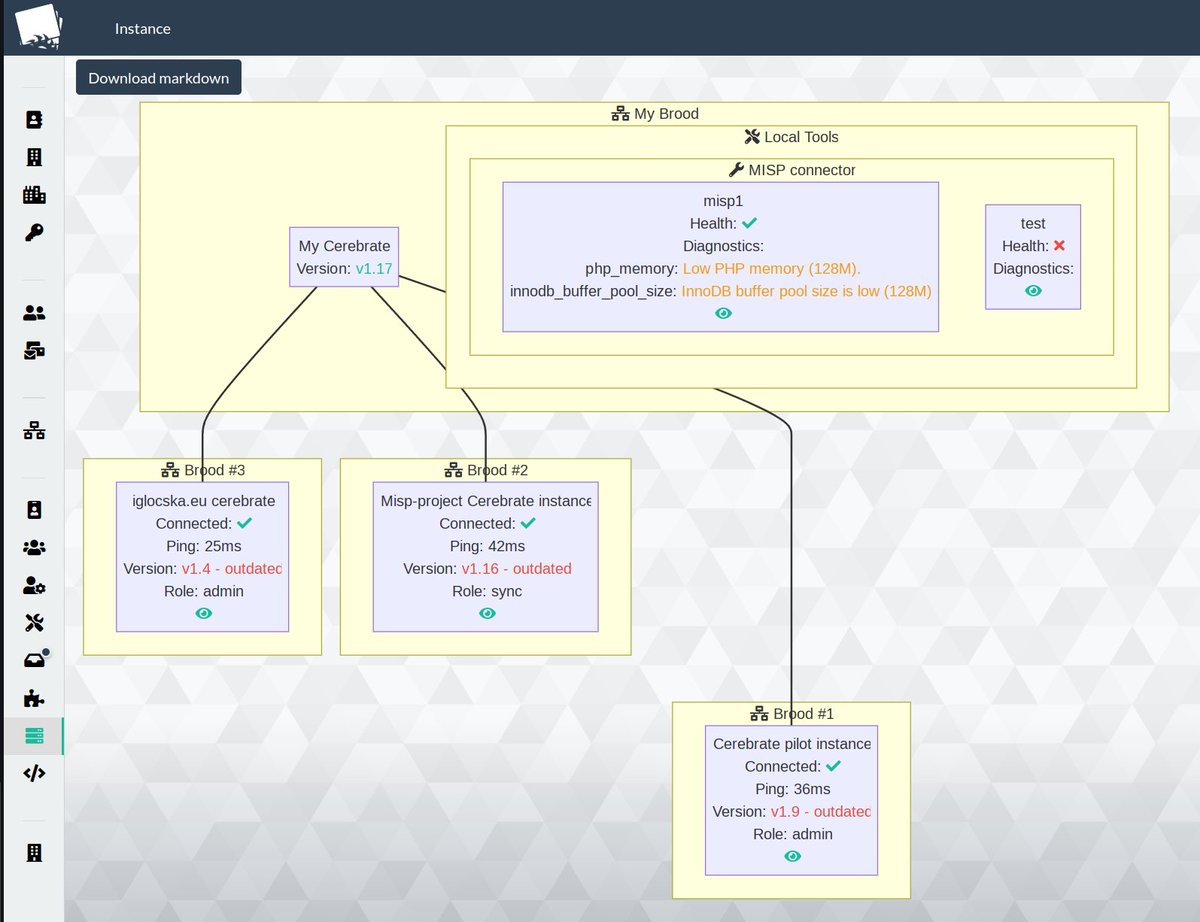
The companion to MISP - Cerebrate version 1.17 has been released with new community management and orchestration features. #isac #threatintelligence #misp #opensource cerebrate-project.org/2023/11/05/Cer… cerebrate_project @[email protected]

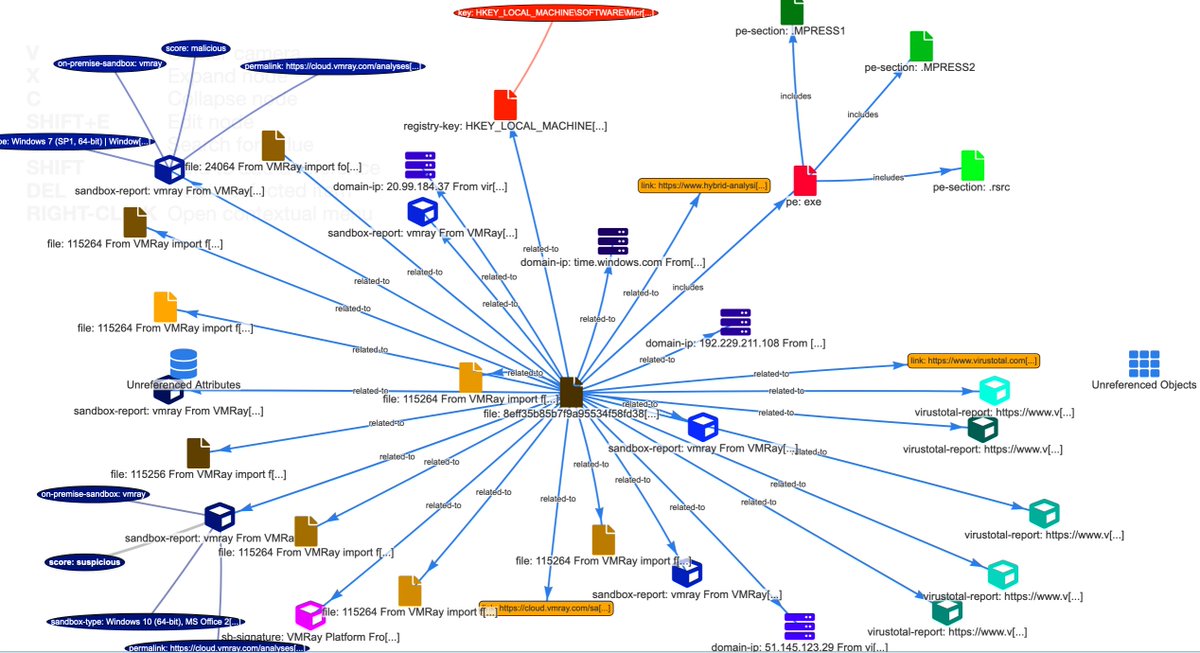
If you liked the previous MISP (@[email protected]) playbook for static malware analysis then you're certainly going to like this one. This playbook extends the results with dynamic malware analysis by the sandboxes from VMRay , Hybrid Analysis and VirusTotal github.com/MISP/misp-play…



Do you know that CIRCL - @[email protected] create many free #OSINT tools dedicated to the community? One of my favorites is the #AIL (Analysis of Information Leaks) framework. You want to know more about it? Retrieve Alexandre Dulaunoy @[email protected]'s talk recorded at leHACK #OsintVillage. youtu.be/PwxtAWtnoF4?si…

If you haven't used the MISP (@[email protected]) playbooks before then have a look at the InfoSec Jupyterthon presentation I did last week. youtube.com/watch?v=2lqbH1… Great work by all participants in showing how Project Jupyter notebooks can support #infosec

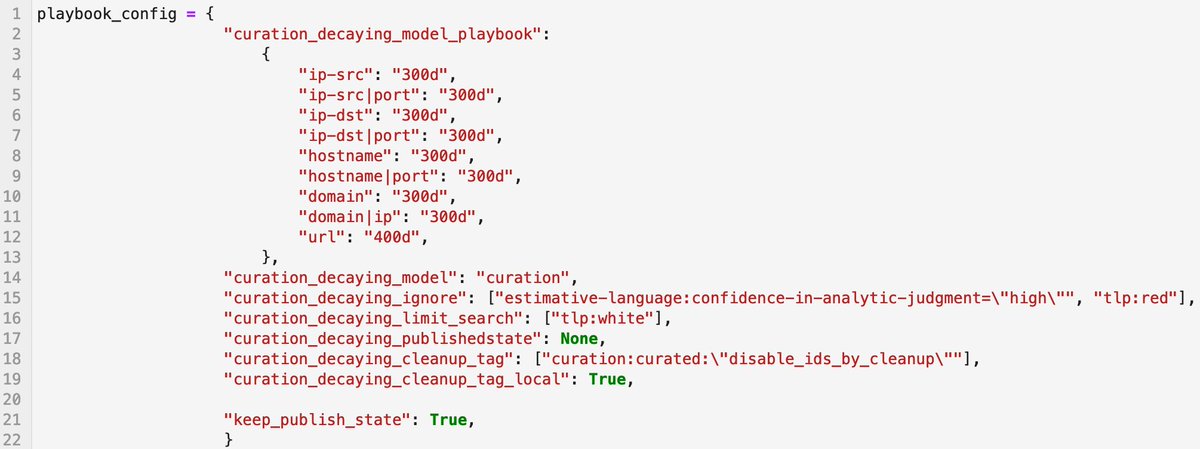
A new MISP (@[email protected]) playbook to help with curation of decayed indicators. Use the custom model of the playbook or one of the MISP build-in models. Decayed indicators are disabled and tagged. #cti github.com/MISP/misp-play…



The MISP galaxy evolved into a complete set of knowledge base freely accessible to many projects including MISP. At the EU ATT&CK community workshop, we presented the recommendations for models creator: Slides: raw.githubusercontent.com/MISP/misp-trai… #threatintelligence Christophe Vandeplas Alexandre Dulaunoy @[email protected]



Kick off the week with a new MISP (@[email protected]) playbook! Query Elasticsearch Elastic for threat intelligence from custom MISP searches, plot the results in a graph, report sightings in MISP, and send a summary to Mattermost. #cti #automation #playbooks github.com/MISP/misp-play…