Gleb Cherbov
@cherboff
ID: 419613012
23-11-2011 15:29:59
148 Tweet
333 Takipçi
344 Takip Edilen

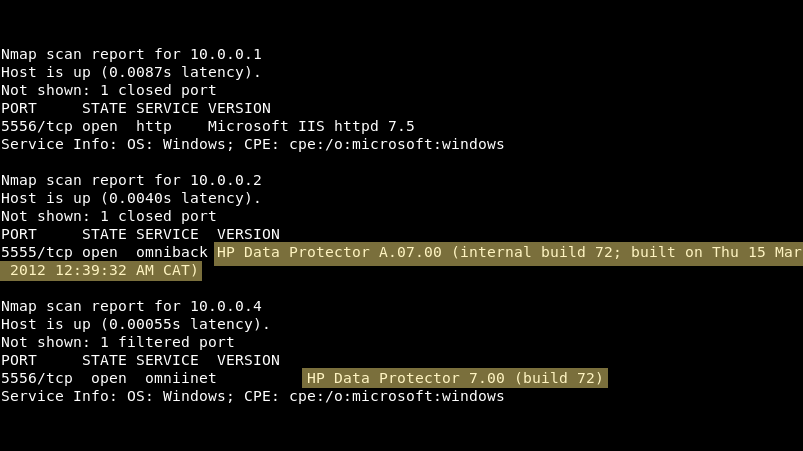
Need SYSTEM? Local Privilege Escalation (#LPE) on all supported versions of Windows by abusing WSUS. Details and PoC released: gosecure.net/blog/2020/09/0…. Blog by Maxime Nadeau.



I'm proud to announce the release of #BloodHound 4.0: The Azure Update! Blog: posts.specterops.io/introducing-bl… BloodHound 4.0 Release Poster: redbubble.com/i/metal-print/… Get BloodHound: bit.ly/GetBloodHound Docs: bloodhound.readthedocs.io/en/latest/ Join the BloodHound Slack: bit.ly/BloodHoundSlack






It's great to see the OWASP® Foundation #Amass Project alongside these excellent #security tools and integrated with @_hexway Hive! #infosec #pentest #osint #redteam




Luke Stephens (hakluke) Informative weaknesses mentioned in report is not making it less stronger. Just do it in a proper way! That's why we have an optional "weakness" flag for every finding reported. So it is pretty simple to separate them to different report sections with no info trash in main parts.