Pietro Borrello
@borrello_pietro
Security Researcher | PhD @SapienzaRoma | Pwner at @TheRomanXpl0it and @mhackeroni | infosec.exchange/@pietroborrello | pietroborrello.bsky.social
ID: 1026713285834563584
https://pietroborrello.com/ 07-08-2018 06:14:57
541 Tweet
2,2K Followers
609 Following

The Hack-A-Sat finals team videos are BACK! 😎 Get to know the teams competing in the #HackASat4 finals next month. First up, 2nd place in quals earlier this year, team mhackeroni! 🇮🇹This Italian team has competed in all 4 Hack-A-Sat competitions & is ready for DEF CON!

No Hat is a 2023 sponsor of mhackeroni, one of the top Italian Ethical Hacking teams! In 10 years, mhackeroni has consistently made it to the podium in major global CTF events, reaching 2nd place in the US Department of Defense Hack-A-Sat final stage and top places in DEF CON

I am happy to announce that Collide+Power, our new and generic software-based power side-channel technique, has been accepted at USENIX Security 2023 #usesec23. collidepower.com



With mhackeroni we won the first CTF pwning a satellite in space 👀 An insanely cool competition organized by Hack-A-Sat at DEF CON, even with cpu side channels in orbit 🤯





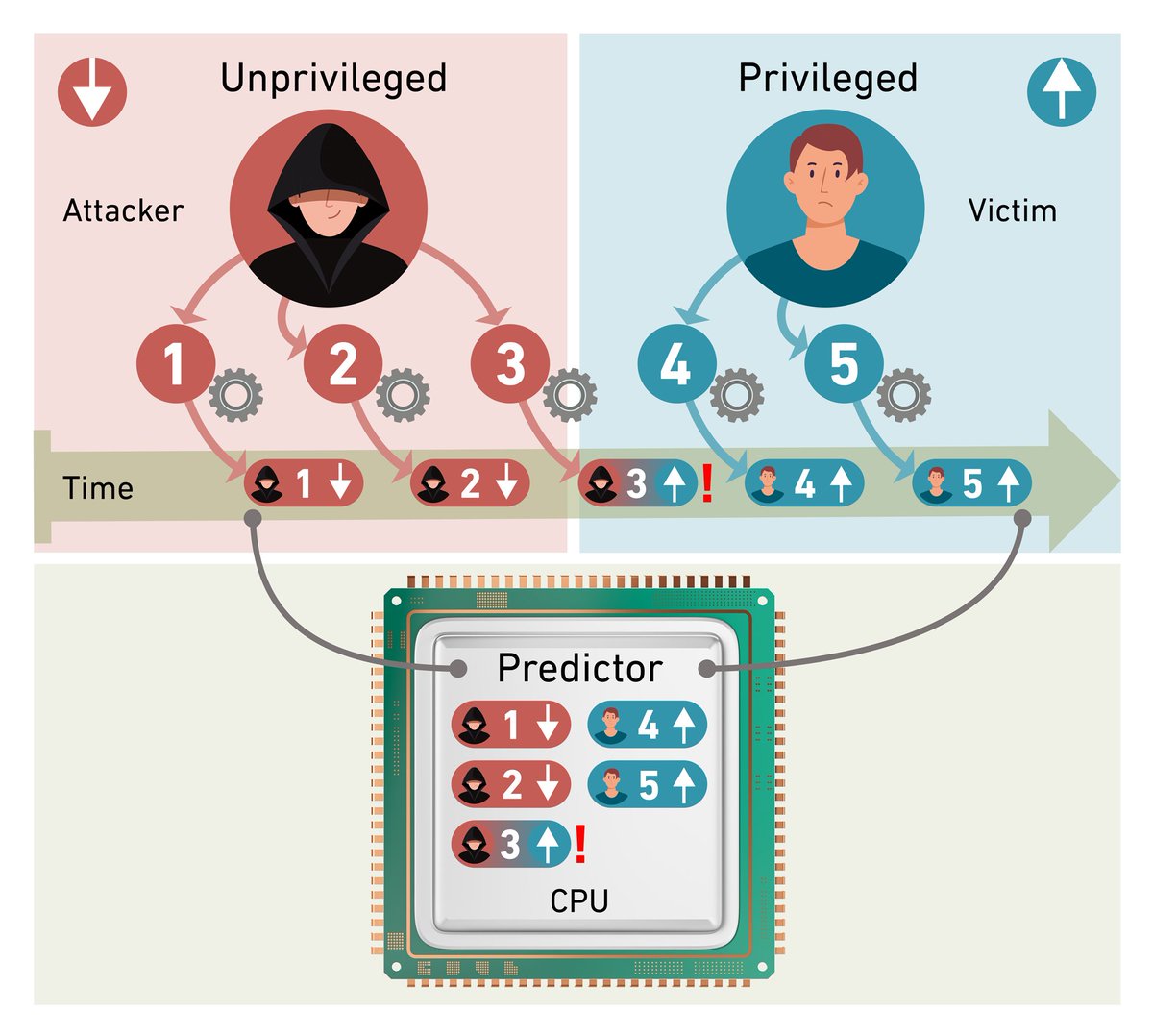
Disclosing #SLAM, aka how to combine Spectre and Intel LAM (& co.) to leak kernel memory on future CPUs (demo below). Thousands of exploitable "unmasked" (or pointer chasing) gadgets in the Linux kernel. Joint work by Mathé Hertogh Sander Wiebing Cristiano Giuffrida: vusec.net/projects/slam

New paper with Pietro Borrello Daniele Cono D'Elia Davide Balzarotti Leonardo Querzoni Cristiano Giuffrida! "Predictive Context-sensitive Fuzzing" introduces compile time context sensitivity to fuzzing w/ selective prioritization using dataflow diversity. Will appear at NDSS24, get it at download.vusec.net/papers/pcsfuzz…



Want to learn about security artifacts? 🤖🧪🚀 NDSS Symposium seeks enthusiastic Artifact Evaluation committee members (PhD/graduate students, postdocs, industry researchers) to review cutting-edge research materials. Apply by May 31st: tinyurl.com/ndss25aec RTs appreciated 🙏