biibek khanal
@biibekkhanal
ID: 1689233159488176128
09-08-2023 11:12:46
805 Tweet
8 Followers
263 Following








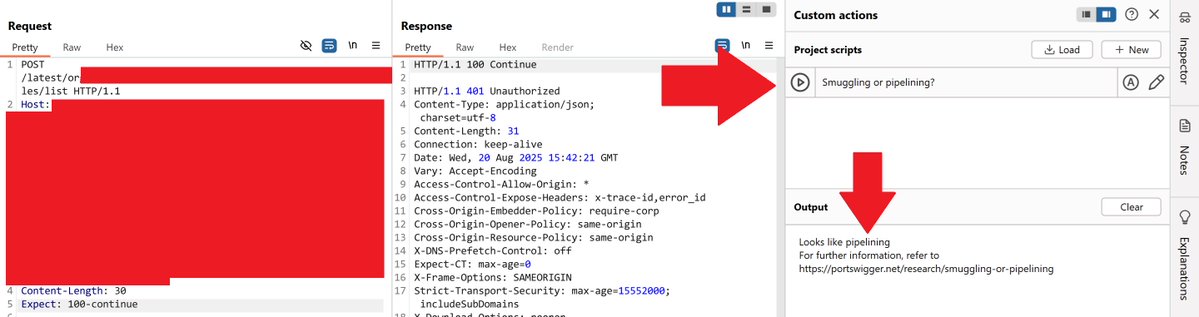
ok, so, when in doubt for http request smuggling or http pipelining, use the bambda by James Kettle github.com/PortSwigger/ba…



I am officially now a member of best AI jailbreaking group in the world, #BT6. Thanks for having me Pliny the Liberator 🐉󠅫󠄼󠄿󠅆󠄵󠄐󠅀󠄼󠄹󠄾󠅉󠅭 and crew! 🫶