Benjamin Sepanski
@bensepanski
CSO at Veridise. UTCS MSCS 2022. DOE CSGF 2020 Fellow. BU Math 2020.
ID: 607752143
https://bensepanski.github.io 14-06-2012 02:39:22
1,1K Tweet
171 Followers
120 Following



making a proof assistant assistant out of Jocelyn Qiaochu Chen's new toy




Please join us at zkDay on Feb 28th in Denver! It will be a fun day full of ZK-related talks, discussions, and activities :) We look forward to seeing you there! Polychain Capital Manta Network (🔱,🔱) Scroll Aleo Cysic Veridise =nil; Foundation Accountable Magic HyperOracle




Our CTO Jon Stephens speaking about three of our tools (Picus, zkVanguard, and zkOrca) for proving and finding bugs in ZK circuits. Thanks to IOSG Venturesc 🔜 KBW & Token2049 for a wonderful and informative event :)


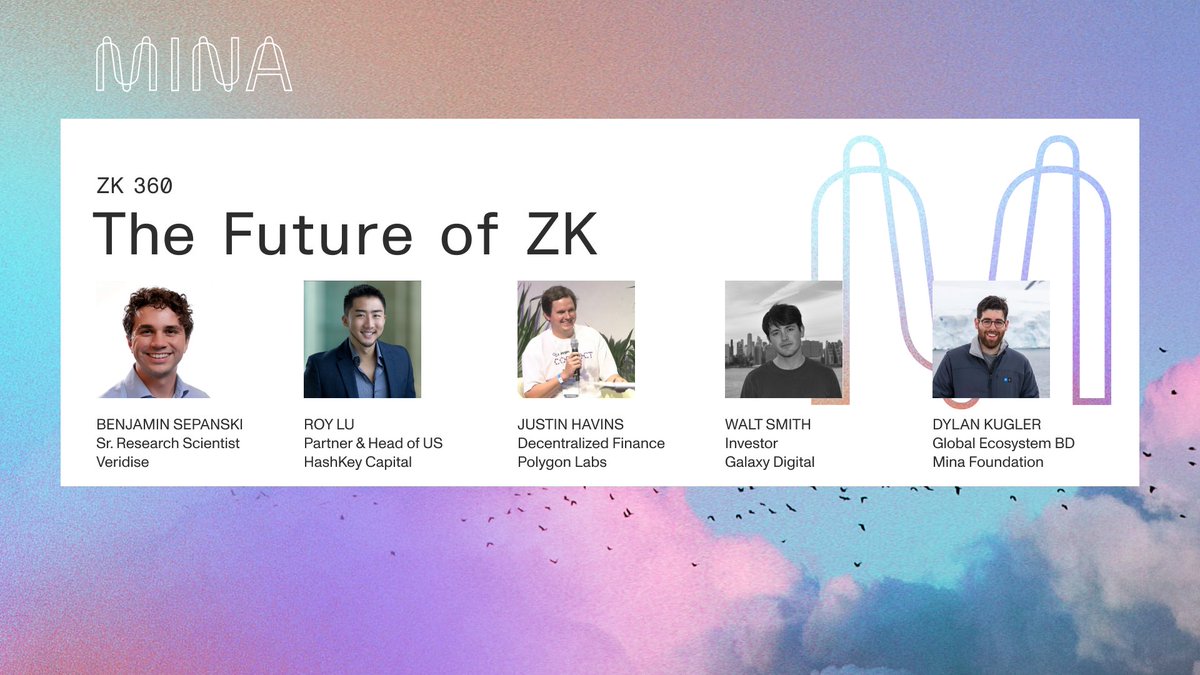
ZK 360 Panel – “Future of ZK” 💭 Discussing the rise of ZK, industries poised for adoption, and regulation with: Benjamin Sepanski from Veridise Roy Lu from HashKey Capital Crypto Texan | katana ⚔️ from @0xPolygonLabs walter from Galaxy Dylan Kugler from Mina Foundation (httpz) 🪶

Our team had a fantastic time at Consensus this year! Thanks to the Blockchain Research Symposium, Mina Protocol (httpz) 🪶 and EVMNext for organizing these events & facilitating great conversations!! Jacob Van Geffen Benjamin Sepanski Isil Dillig