Behnam
@bdasec_
Computer security person | full-time learner #Bitcoin
ID: 877476315837980674
https://ninjas.zip 21-06-2017 10:40:31
747 Tweet
843 Followers
4,4K Following


Just pwned Windows 11 with a kernel 0day in Pwn2Own Berlin! Thanks to my teammates Gerrard and Thach(Thach Nguyen Hoang 🇻🇳) for helping me run the exploit. Goodluck to their entries as well.

We have a bug collision. Although Sina Kheirkhah (SinSinology) of Summoning Team (SummoningTeam) successfully demonstrated his exploit of #NVIDIA Triton, the bug he used was known by the vendor (but not patched). He still earns $15K and 1.5 Master of Pwn points.


Most points in the AI category at the recent Trend Zero Day Initiative Pwn2Own! 🥳





[ZDI-25-298|CVE-2025-31233] Apple macOS MP4 File Parsing Memory Corruption Remote Code Execution Vulnerability (CVSS 8.8; Credit: Hossein Lotfi (Hossein Lotfi) of Trend Micro Zero Day Initiative) zerodayinitiative.com/advisories/ZDI…

[ZDI-25-305|CVE-2025-31219] Apple XNU kernel vm_map Race Condition Local Privilege Escalation Vulnerability (CVSS 8.8; Credit: Michael DePlante (Michael DePlante) and Lucas Leong (Lucas Leong) of Trend Micro's Zero Day Initiative) zerodayinitiative.com/advisories/ZDI…




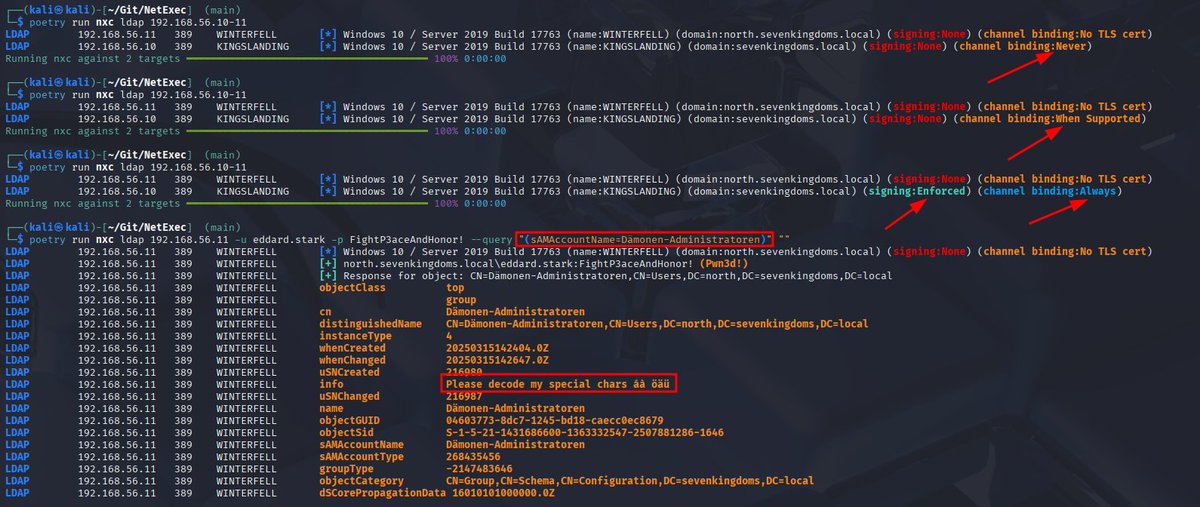
NetExec now has native checks for LDAP signing and channel binding capabilities of the target DC, thanks to the implementation of Thomas Seigneuret 🚀 I also fixed querying LDAP with non-ASCII characters, so you can finally query groups such as "Dämonen-Administratoren"🎉

The slides for offensivecon talk "Hunting for overlooked cookies in Windows 11 KTM and baking exploits for them" by Cedric Halbronn and I are here: docs.google.com/presentation/d…