b41s
@b41ss
🪼
ID: 926181809456582656
02-11-2017 20:18:45
655 Tweet
27 Followers
123 Following



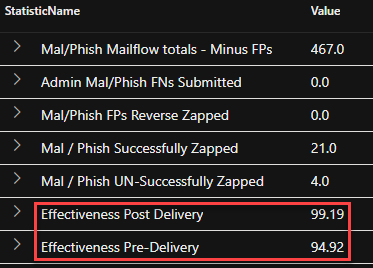
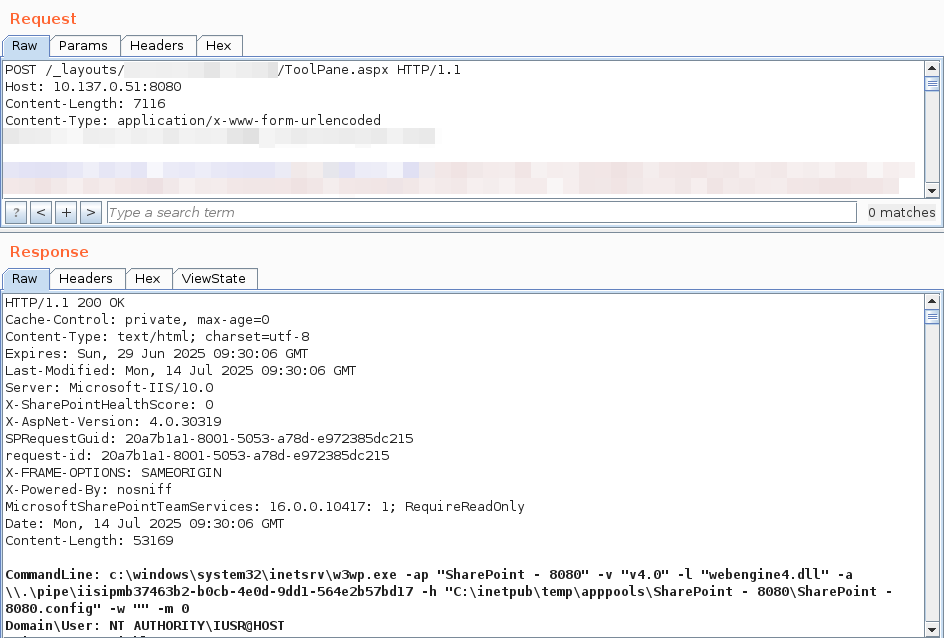
**NEW** BHIS | Blog If you had to guess, how does BHIS compromise your networks and domains? Let's go Family Feud style with this one! The Top Ten List of Why You Got Hacked This Year by: Jordan Drysdale & Kent Ickler Published: 12/12/2024 Learn more: blackhillsinfosec.com/top-ten-list-o…










If you have developers in your organization using Dev Tunnels in VS Code there are now group policy controls to allow you to manage the configuration. You can disable Dev Tunnels, disable anonymous tunnels or lock down access to specific Entra tenants- techcommunity.microsoft.com/blog/azuredevc…