Mathias Karlsson
@avlidienbrunn
Web security fiddler. Bug bounty bastard. Sometimes I cut shapes.
ID: 440767696
19-12-2011 11:46:03
1,1K Tweet
16,16K Followers
602 Following






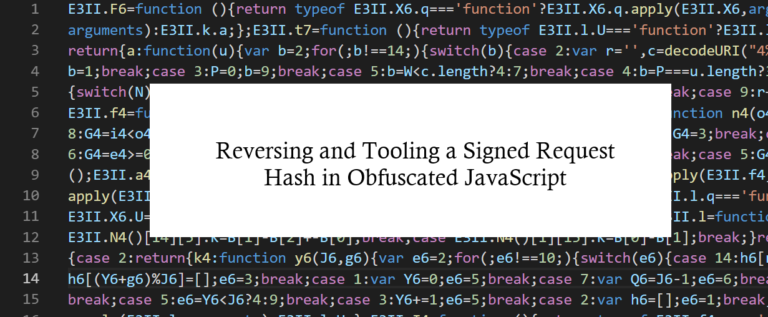
Reversing and Tooling a Signed Request Hash in Obfuscated JavaScript buer.haus/2024/01/16/rev… Thanks to HackingHub for putting together a lab to learn more about it: app.hackinghub.io/surl



My talk for Insomni'hack is now available on youtube! Hope you'll enjoy it! :D youtu.be/Sm4G6cAHjWM



I recently developed and posted about a technique called "First sequence sync", expanding James Kettle's single packet attack. This technique allowed me to send 10,000 requests in 166ms, which breaks the packet size limitation of the single packet attack. flatt.tech/research/posts…

#𝗞𝗮𝗹𝗺𝗮𝗿𝗖𝗧𝗙 𝟮𝟬𝟮𝟱 𝗶𝘀 𝗷𝘂𝘀𝘁 𝗮𝗿𝗼𝘂𝗻𝗱 𝘁𝗵𝗲 𝗰𝗼𝗿𝗻𝗲𝗿 - 𝗰𝗼𝗺𝗲 𝗰𝗼𝗺𝗽𝗲𝘁𝗲 𝘄𝗶𝘁𝗵 𝘁𝗵𝗲 𝗯𝗲𝘀𝘁 𝗰𝗼𝗺𝗽𝗲𝘁𝗶𝘁𝗶𝘃𝗲 𝗵𝗮𝗰𝗸𝗲𝗿𝘀 𝗳𝗿𝗼𝗺 𝗮𝗿𝗼𝘂𝗻𝗱 𝘁𝗵𝗲 𝘄𝗼𝗿𝗹𝗱 𝗮𝗻𝗱 𝘄𝗶𝗻 𝗴𝗿𝗲𝗮𝘁 𝗽𝗿𝗶𝘇𝗲𝘀! (6x IDAPro from Hex-Rays SA) #CTF




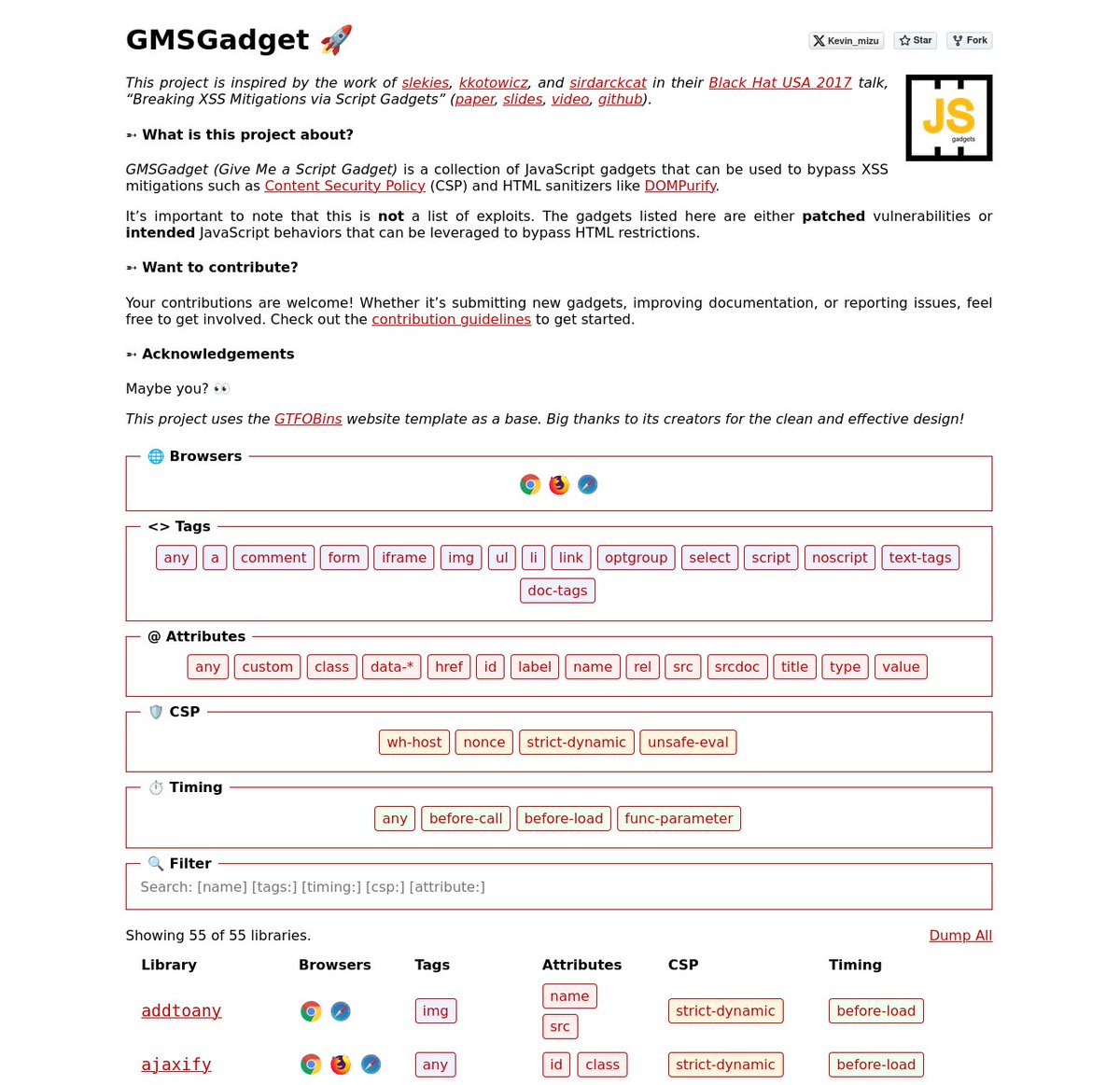
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4