Avital Shafran
@avitalshafran
PhD Student @CseHuji • Trustworthy and Secure ML
ID: 1200312158573285376
http://avital.shafran.co.il 29-11-2019 07:15:13
54 Tweet
160 Takipçi
158 Takip Edilen

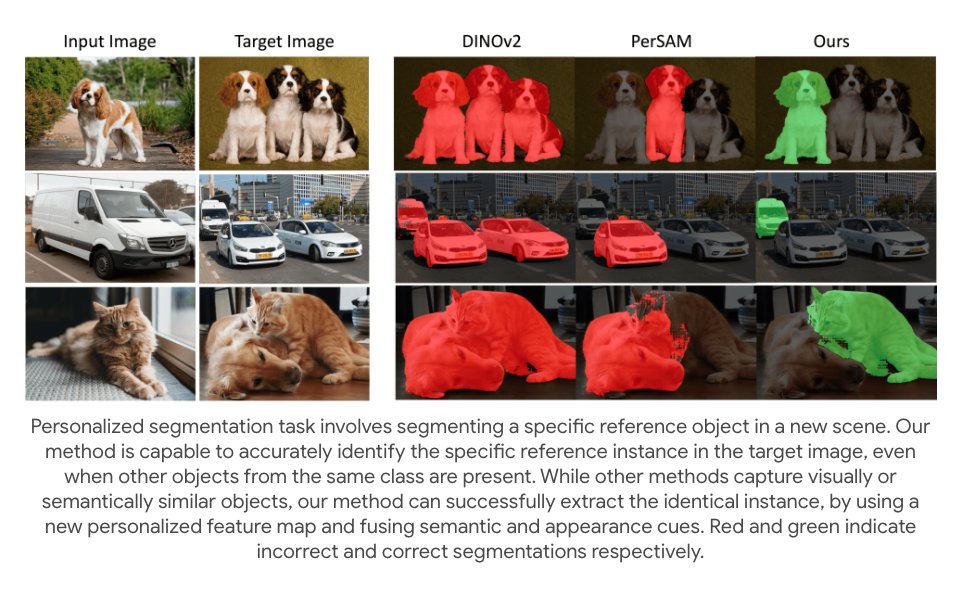
Thrilled to share that our paper, "Where's Waldo: Diffusion Features for Personalized Segmentation and Retrieval" has been accepted to NeurIPS 2024! 🎉 Paper: arxiv.org/abs/2405.18025 Project Page: dvirsamuel.github.io/pdm.github.io/ #NeurIPS2024 Gal Chechik Rami Ben-Ari Matan Levy



It was a pleasure to co-organize this workshop with the amazing Avital Shafran! Can’t wait to see what she accomplishes next! 👏