Averlon
@averlon_ai
Peerless cloud security
ID: 1765526485417476096
06-03-2024 23:55:17
10 Tweet
23 Takipçi
9 Takip Edilen


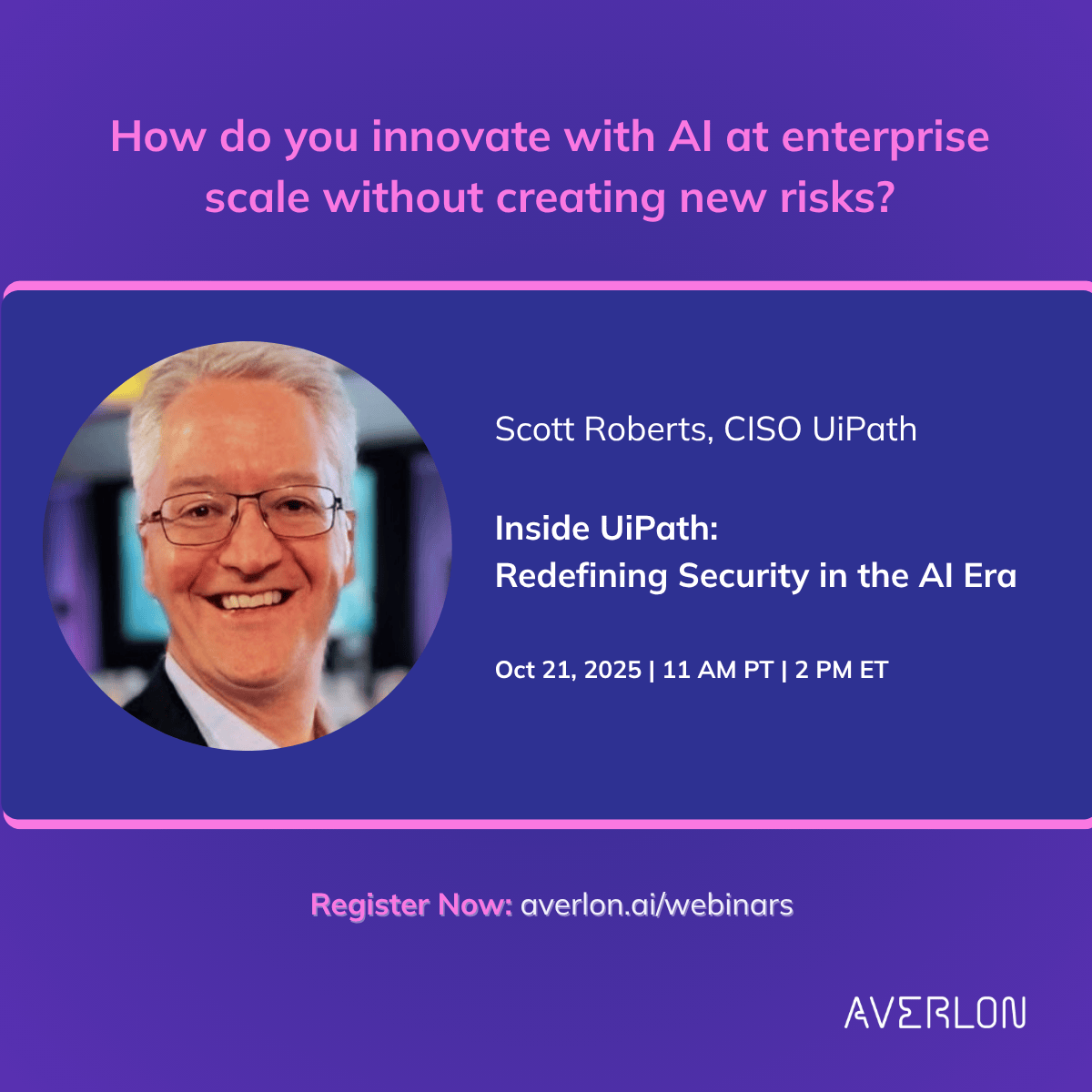
How do you build trust in a world shaped by AI, fraud, and cyber threats? This Wednesday, October 22, Averlon Co-founder & CEO Sunil Gottumukkala (Sunil) will join Erik Benson, General Partner at Voyager Capital, and Alex Algard (Alex Algard), Founder & CEO of Hiya, at the






📘 New research from Enterprise Strategy Group (Enterprise Strategy Group), part of OmdiaCyber, Automating Risk Reduction in the AI Era 400 security leaders share how AI is reshaping exposure management and driving faster remediation across hybrid and cloud environments. Kudos to Tyler



Security teams are not short on findings. They are short on time. The latest research from ESG (Enterprise Strategy Group) shows what the most effective teams have in common. 1. They prioritize with real context. 2. They remove manual steps that slow them down. 3. They use agentic AI to