
Andrew Case
@attrc
@Volatility Core developer, Dir. of Research @Volexity, @lsucyber, The Art Of Memory Forensics Co-Author
ID: 119293693
https://www.volexity.com 03-03-2010 06:24:28
20,20K Tweet
27,27K Followers
4,4K Following


thermoptic - A next-generation HTTP stealth proxy which perfectly cloaks requests as the Chrome browser across all layers of the stack. - by mandatory.bsky.social github.com/mandatoryprogr…

So excited that I’m going to present my latest research at DistrictCon in January! The last round of tickets are going on sale on this Sunday (Nov 16th nour zohbi EST). Looking forward to see you in DC!









The volatility #PluginContest closes on Dec 31, 2025! Make sure to submit your entry by the deadline! If you’re looking for inspiration, take a look at our roll call of past contest submissions: volatilityfoundation.org/volatility-plu… #memoryforensics








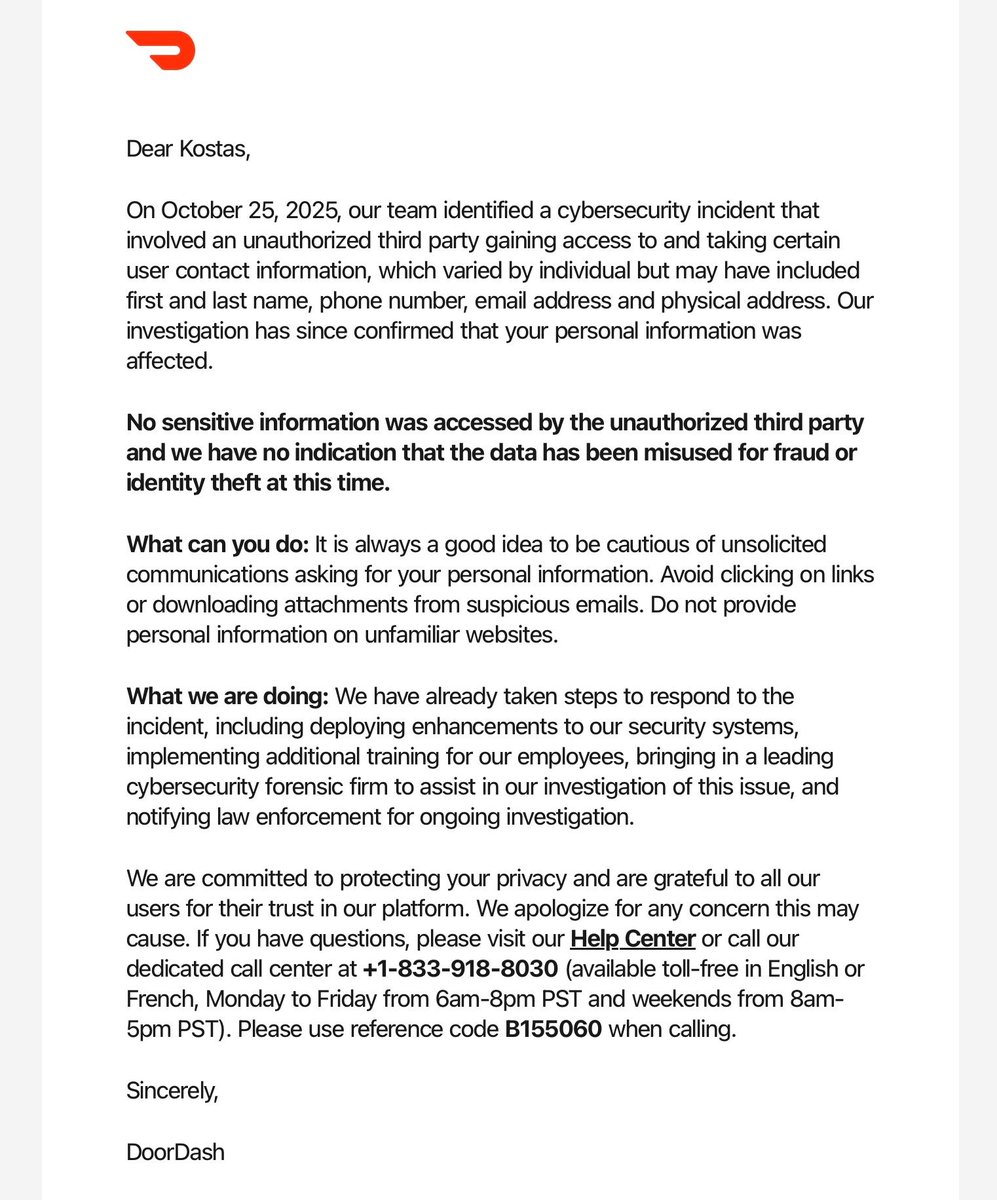
![Volexity (@volexity) on Twitter photo .<a href="/Volexity/">Volexity</a> #threatintel tracks a wide variety of threat actors abusing Device Code & OAuth authentication workflows to phish credentials. And these techniques continue to see success due to creative social engineering. [1/2] .<a href="/Volexity/">Volexity</a> #threatintel tracks a wide variety of threat actors abusing Device Code & OAuth authentication workflows to phish credentials. And these techniques continue to see success due to creative social engineering. [1/2]](https://pbs.twimg.com/media/G7WF68EWgAABT4d.jpg)



