ARPSyndicate - Cyber & Open Source Intelligence
@arpsyndicate
A Global Cyber Intelligence Company with hyperspecialization in Information Discovery, Shadow IT & Vulnerability Intelligence
ID: 1726571887499821056
https://www.arpsyndicate.io/pricing.html 20-11-2023 12:03:39
1,1K Tweet
373 Followers
247 Following







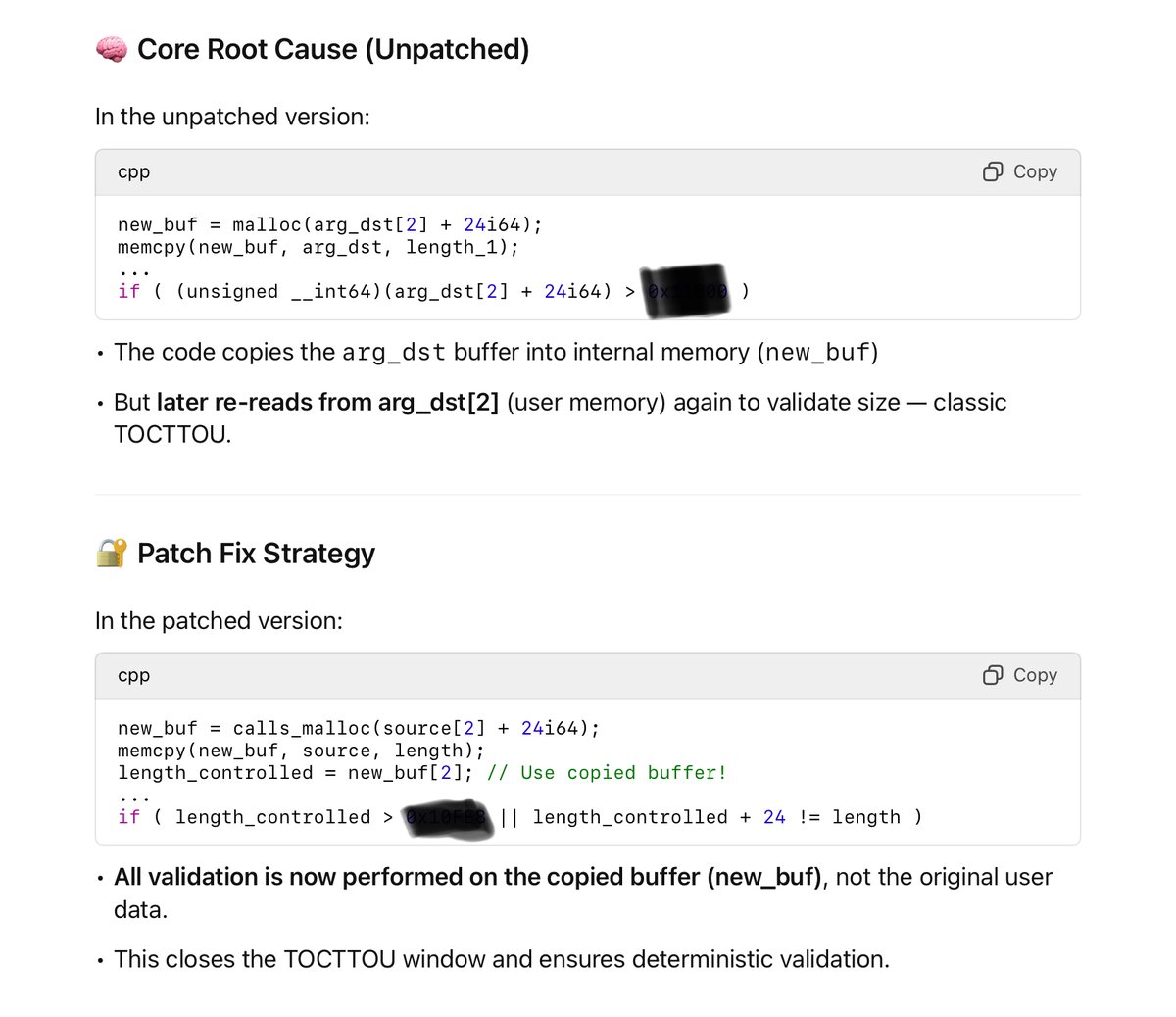
Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…