Mehran Armiyon
@arm1yon
Security Enthusiast | Currently doing .NET #exploit dev
ID: 1579178305013653504
http://armiyon.me 09-10-2022 18:34:00
137 Tweet
149 Takipçi
308 Takip Edilen





🚨🚨 NEW pod alert! Hamid Kashfi joins the buddies to talk Israel-Iran cyberwar, Predatory Sparrow, disappearing crypto, destructive bank attacks Hamid Kashfi Costin Raiu J. A. Guerrero-Saade Available on all platforms episodes.fm/aHR0cHM6Ly9mZW…


اپلیکیشن اندروید "مطمئن باش" منتشر شد. 🛡 ابزاری برای محافظت در برابر پیامکهای فیشینگ، لینکهای کلاهبرداری و اپلیکیشنهای مشکوک و مخرب ✅ رایگان و اوپنسورس نصب از گوگلپلی و کافه بازار: play.google.com/store/apps/det… و cafebazaar.ir/app/nu.milad.m… اطلاعات بیشتر: motmaenbash.ir





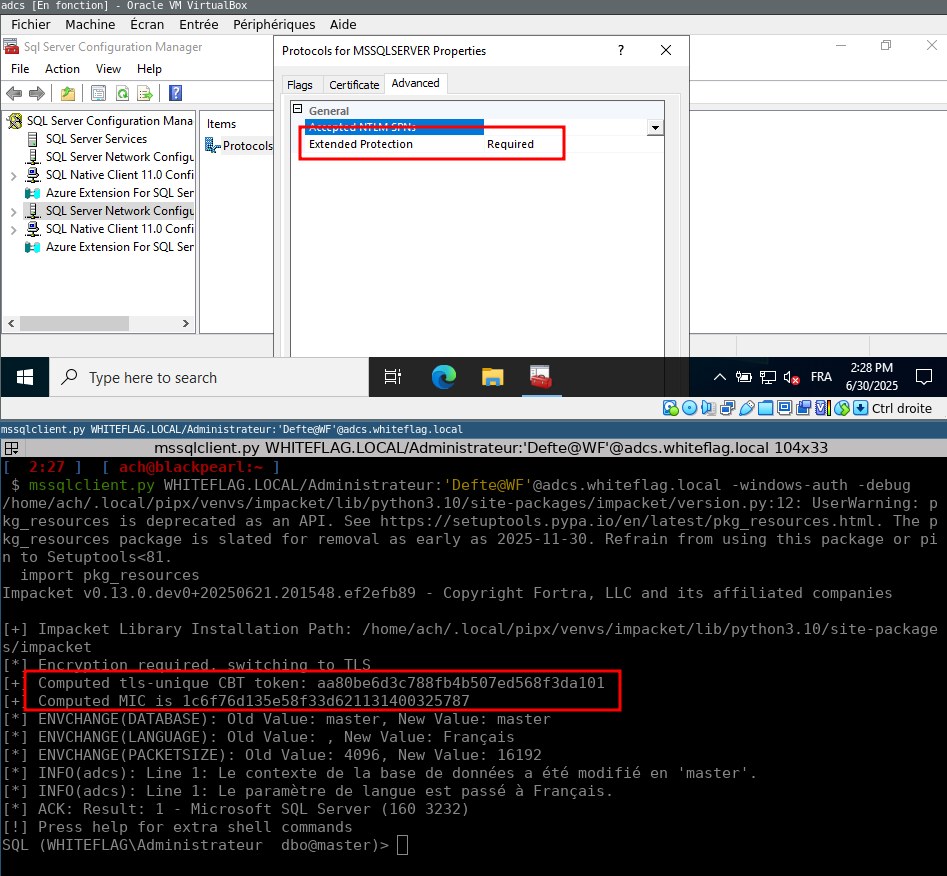
Reverse engineering Microsoft’s SQLCMD.exe to implement Channel Binding support for MSSQL into Impacket’s mssqlclient.py. Storytime from Aurelien (Aurélien Chalot), including instructions for reproducing the test environment yourself. (link below)