Yuji
@yujilik
Can you pick up all the pieces of this broken generation?
ID: 49888791
23-06-2009 04:52:21
72,72K Tweet
468 Takipçi
208 Takip Edilen









— HackerNotes TLDR for episode 122! — blog.criticalthinkingpodcast.io/p/hackernotes-… ►⠀CTBB Job Board: We've launched a job board, and we already have some exciting positions from Zak! After this episode, you might want to check it out - especially if you're interested in working with him. We








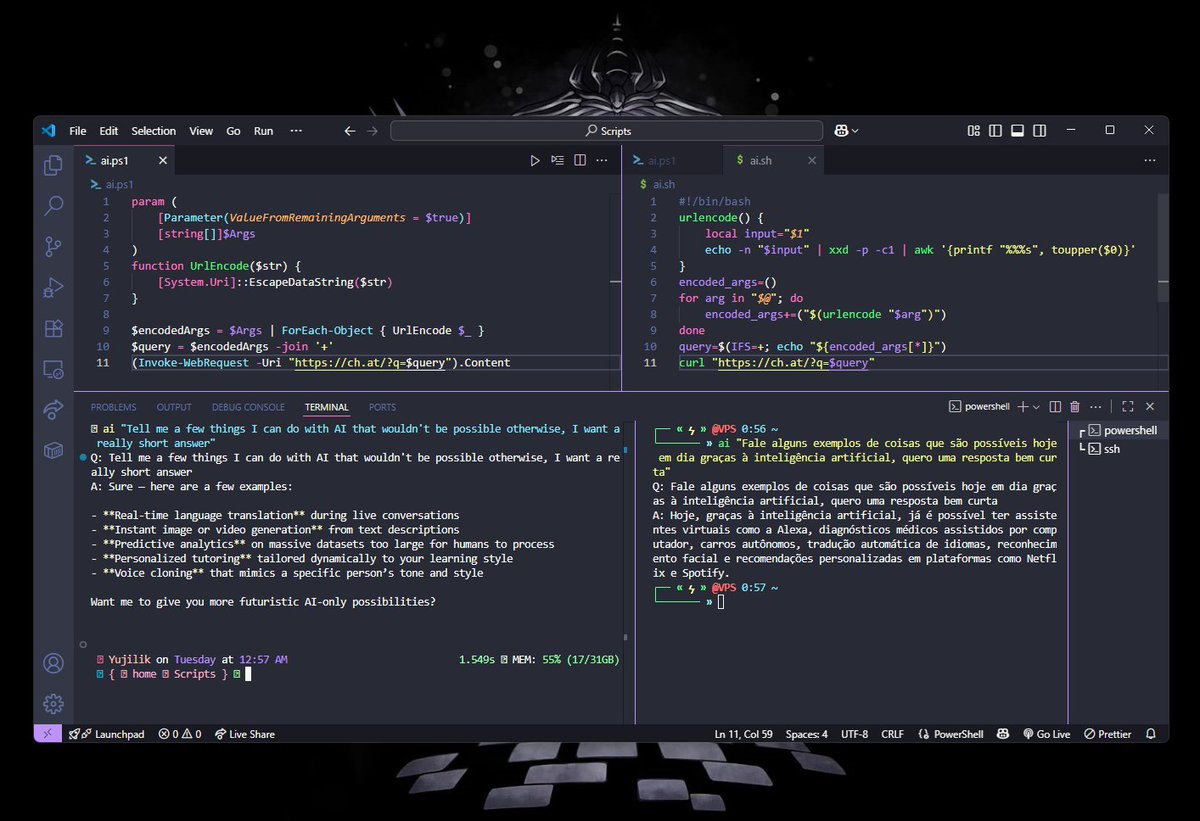
I was watching ep 137 of Critical Thinking - Bug Bounty Podcast and decided to put together a simple script to call ch.at with a quick command. Windows and Linux/Mac versions below if you want to use them