Vivek Verma
@vivek23647571
Vulnerability Researcher | Hall of fame : Google
ID: 1429079633622749184
https://www.youtube.com/@vivekverma5467 21-08-2021 13:55:26
249 Tweet
921 Takipçi
599 Takip Edilen

Congratulations to my brother vivek and Vikas Maurya for this huge and mind blowing 🤯 achievement 🙌 Wishing you guys all the best for future you guys are going to rock in future Best wishes 🤞 #BugBounty #bugbountytips #bugbountytip #BugHunter #bug #web2 #web3

🌟 Waking up to this made my day! 🎉 Huge thanks to Ben Sadeghipour for the follow. Grateful for the support and inspired to keep pushing the boundaries in bug hunting. 🙌 #BugBounty #CyberSecurity #Infosec

Vivek Verma Keep up the good work and congrats on the big bounty from google! 🫶🎉

Bishop Fox OWASP® Foundation HAHWUL 🎉 Celebrate Xion gifts $462K Google VRP (Google Bug Hunters) bounty to picoCTF Vivek Verma received $10K bounty from Google VRP (Google Bug Hunters) tal promoted to Staff ASE at bugcrowd @Samm0uda and team received $250K bounties from Meta (Philippe Harewood, Josip Franjković, and Dzmitry Lukyanenko)



Hey Amazon Help, I ordered a Product, but the package was EMPTY! The delivery guy left instantly & refused to return when I called within a minute. Now Amazon is denying a refund, blaming me instead of investigating the delivery agent. Is this how you treat loyal customers?






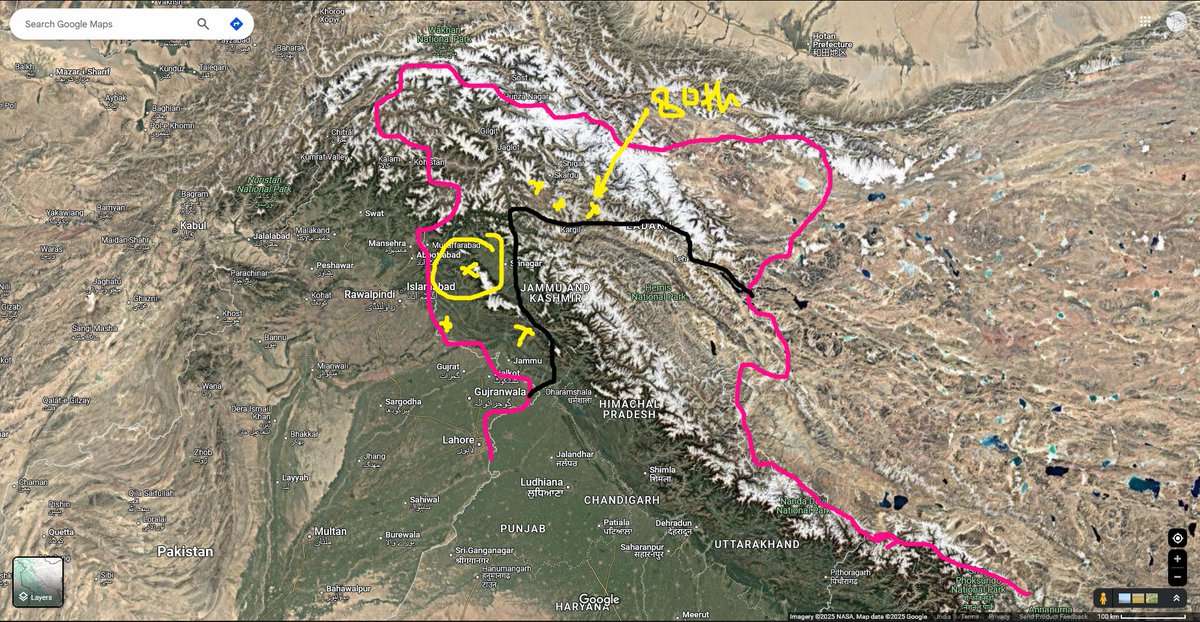
Indian Air Force ADG PI - INDIAN ARMY SpokespersonNavy a thread of Pakistani strategic military locations near PoK region. it is time. #PahalgamTerroristAttack #PulwamaAttack #IndianArmy




With only 48 hours remaining in a bug bounty event, I used Hacktron AI CLI to perform large-scale analysis of several JDBC drivers. Netting $85,000 in total rewards. This write-up shows how AI-assisted vulnerability research is speeding up the work of researchers and leading to