Virus Bulletin
@virusbtn
Security information portal, testing and certification body.
Organisers of the annual Virus Bulletin conference. @[email protected]
ID:118059149
https://www.virusbulletin.com/ 27-02-2010 13:27:37
25,1K تغريدات
58,8K متابعون
1,4K التالية

We are pleased to announce and welcome onboard the first five partners of #VB2024 : Malwation, Cisco Talos Intelligence Group, Fortinet, Cyber Threat Alliance & QI-ANXIN. Find out how to join them and make your company visible among security peers: virusbulletin.com/conference/vb2…

















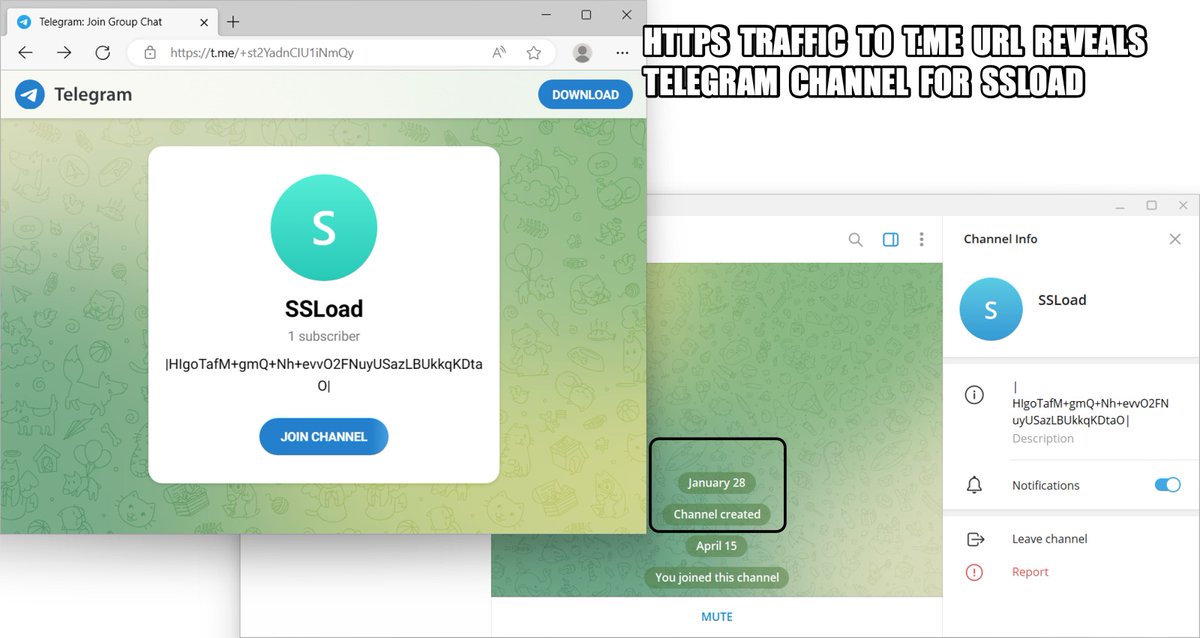
2024-04-15 (Monday): #ContactForms campaign pushing #SSLoad malware as early as Thursday, 2024-04-11. List of indicators available at bit.ly/49Cz1kL
#Wirshark #Unit42ThreatIntel #TimelyThreatIntel #InfectionTraffic