⚛️ Marcin Siedlarz
@siedlmar
Technical attribution of cyber threats | Frontline Intrusion Intelligence 🦅 @Mandiant
ID: 1882712942
https://keybase.io/siedlmar 19-09-2013 10:38:34
3,3K Tweet
1,1K Takipçi
1,1K Takip Edilen




Is there a ghost in your router? Our new blog outlines how #UNC3886 continues to deploy custom malware ecosystems for long-term access, this time targeting Juniper Networks’ Junos OS routers. 👻👻 Google Cloud cloud.google.com/blog/topics/th…








🦘 RooCon25 Call for Papers is open! 🦘 This is your chance to share your latest insights and help us make RooCon25 the most successful edition to date! We’re waiting for submissions until 22nd of August. Find the CFP submission link and the guidelines at rsvp.withgoogle.com/events/roocon2…




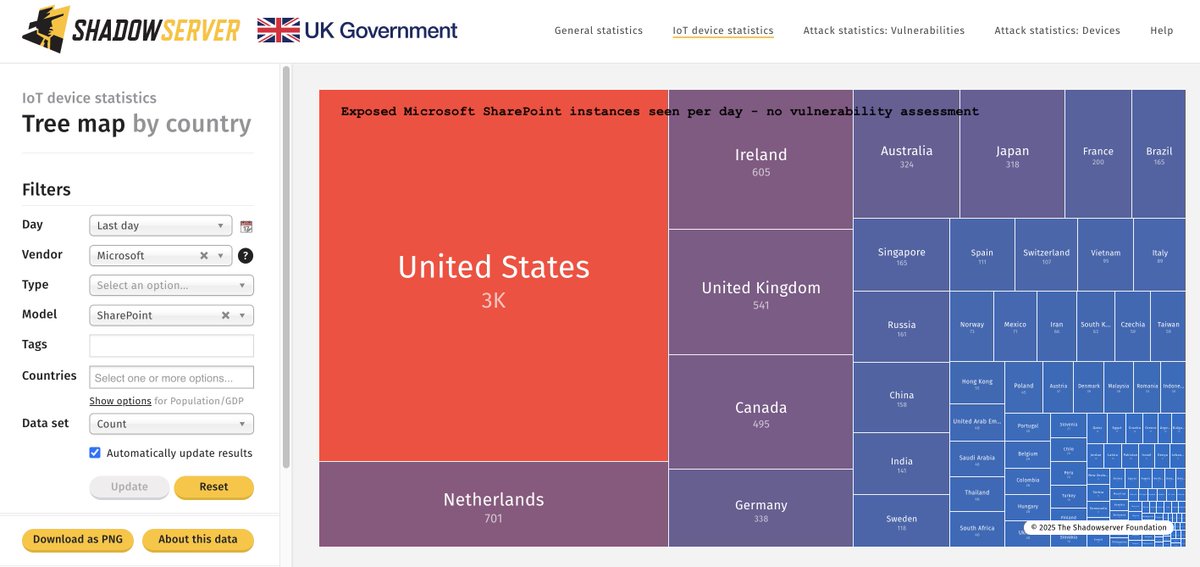
Alert: SharePoint CVE-2025-53770 incidents! In collaboration with Eye Security & watchTowr we are notifying compromised parties. Read: research.eye.security/sharepoint-und… ~9300 Sharepoint IPs seen exposed daily (just population, no vulnerability assessment): dashboard.shadowserver.org/statistics/iot…