Shelly Kramer
@shellykramer
ARInsights' ARchitect Analyst Power 100 tech analyst | principal analyst @KramerandCo. Research #AI #Security #ESG #Collaboration #CX #DX #Cloud
ID: 18460854
http://kramerand.co 29-12-2008 21:44:27
231,231K Tweet
93,93K Takipçi
64,64K Takip Edilen

My technewsworld. article on how Infineon and the Connectivity Standards Alliance are prioritizing #security as a critical element of the #Matter smart home standard Xthings Group @Amazon Google Apple bit.ly/4dk3JCY?utm_so…


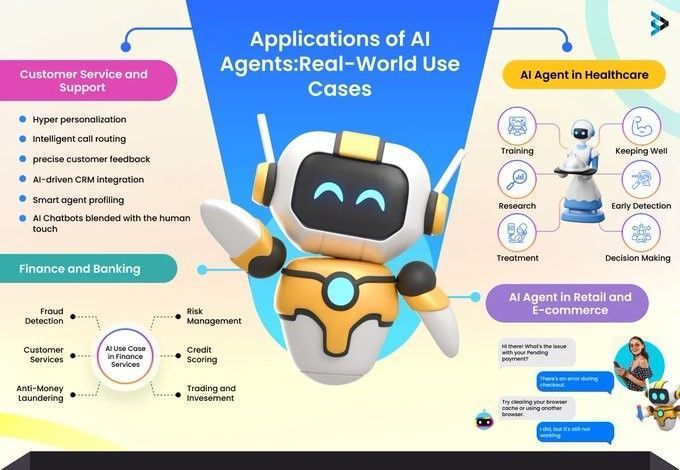
Applications of #AI Agents by Dr. Khulood Almani | د.خلود المانع #Healthcare #Chatbots #ArtificialIntelligence #MI #MachineLearning #Tech #Technology cc: Shailendra Kumar Yann LeCun @yuhelenyu