DIMOOON 🇺🇦
@reewardius
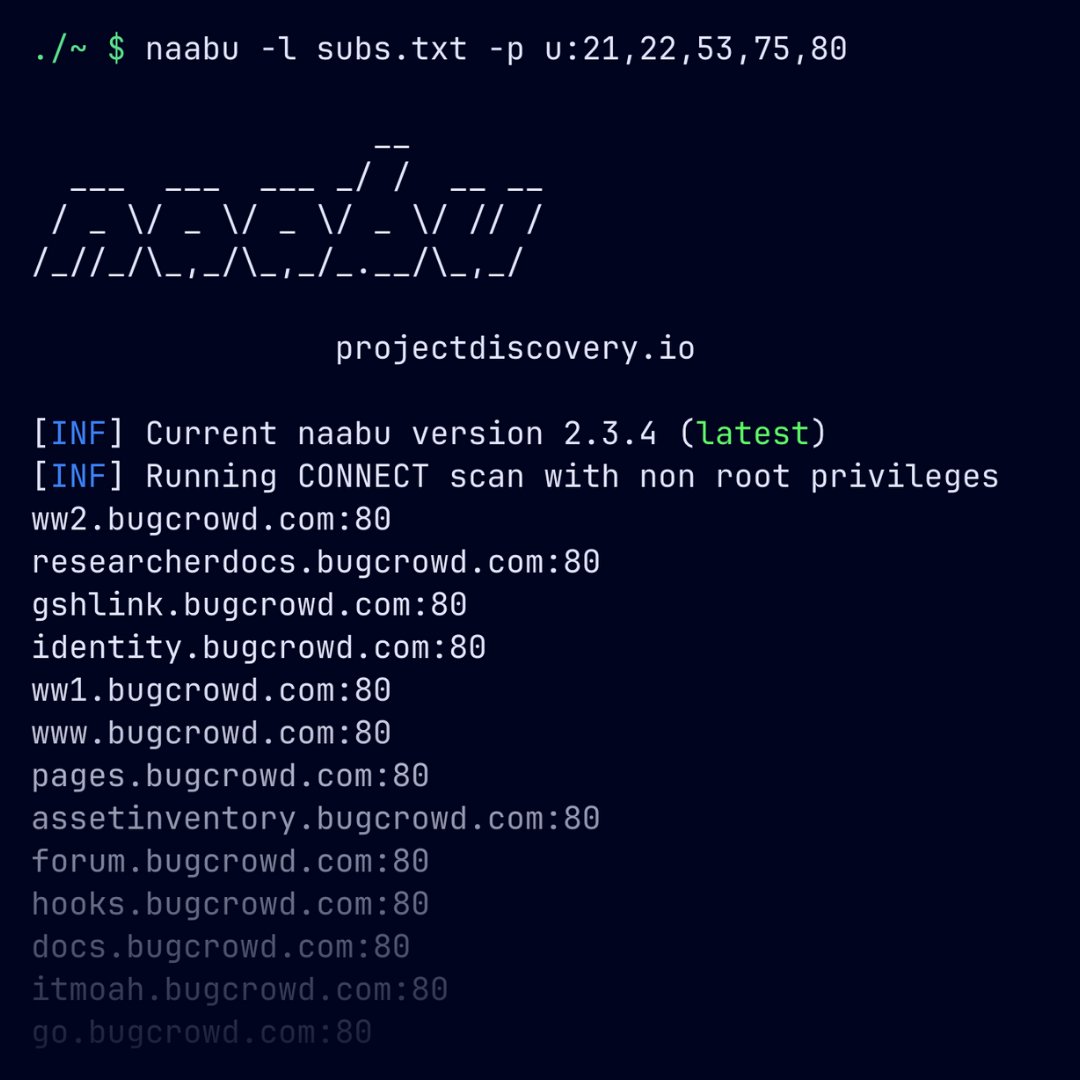
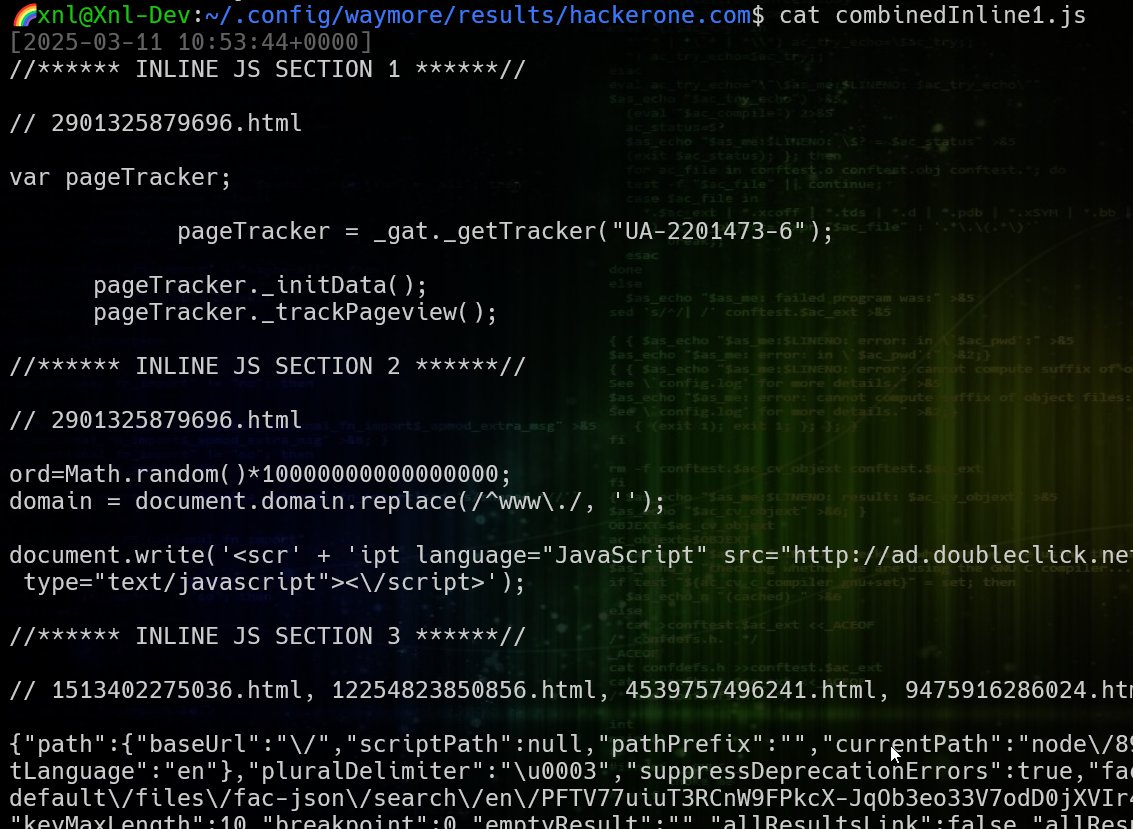
./acunetix -u kremlin.ru -t ~/shutdown_payloads/
ID: 1377943862698770435
02-04-2021 11:20:12
3,3K Tweet
727 Takipçi
1,1K Takip Edilen







Emad Shanab - أبو عبد الله If you only care about getting archived URLs and not responses, then use "-mode U" with waymore. It will be a lot quicker






Md.Karimul Islam Shezan Yes. But with some custom tool. infosecwriteups.com/waf-bypass-mas…





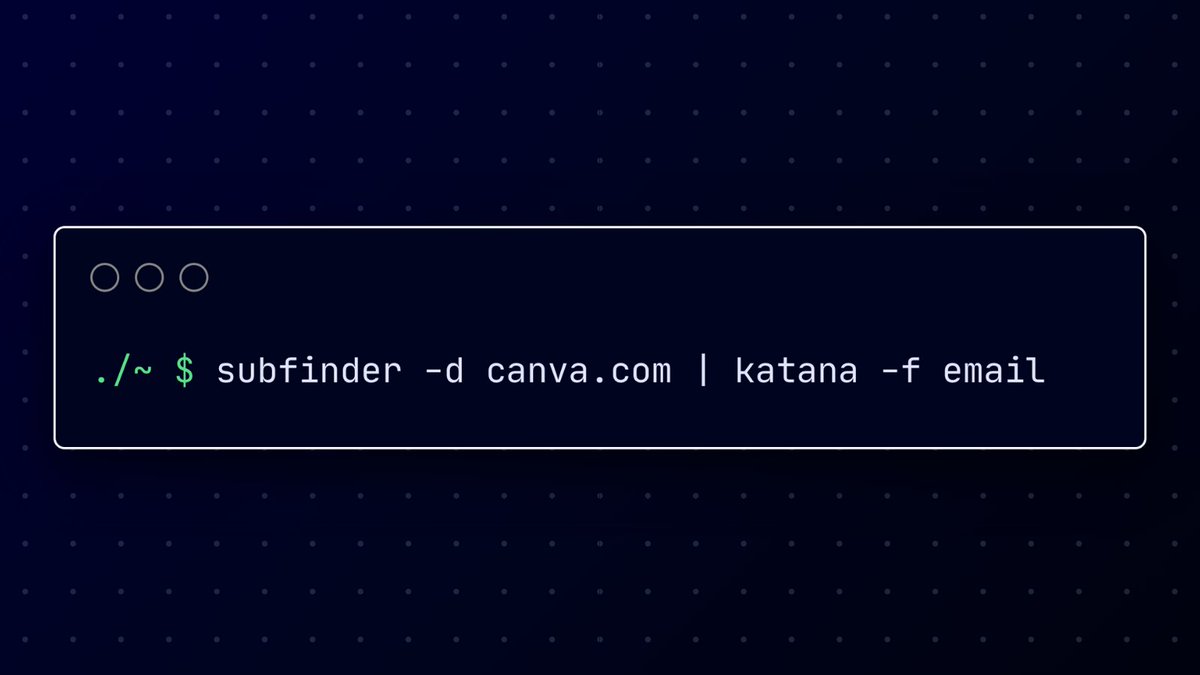
My tool new recon, thanks ProjectDiscovery , Luke Stephens (hakluke) , Robert Graham github.com/KingOfBugbount… #bugbounty #recon #bugbountytips


![Hussein Daher (@hussein98d) on Twitter photo Vulnerability of the day:
host[.]xyz/.DS_Store --> strings --> zip file containing older JS files --> authentication token leak
#bugbounty Vulnerability of the day:
host[.]xyz/.DS_Store --> strings --> zip file containing older JS files --> authentication token leak
#bugbounty](https://pbs.twimg.com/media/Fhcvp6rX0AMgbB_.jpg)
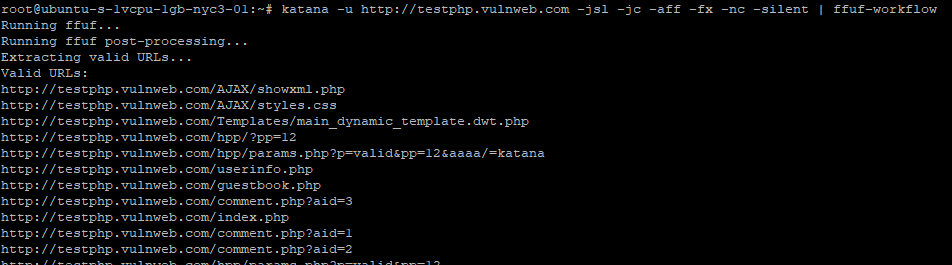
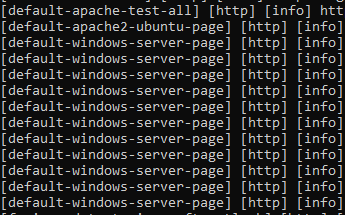


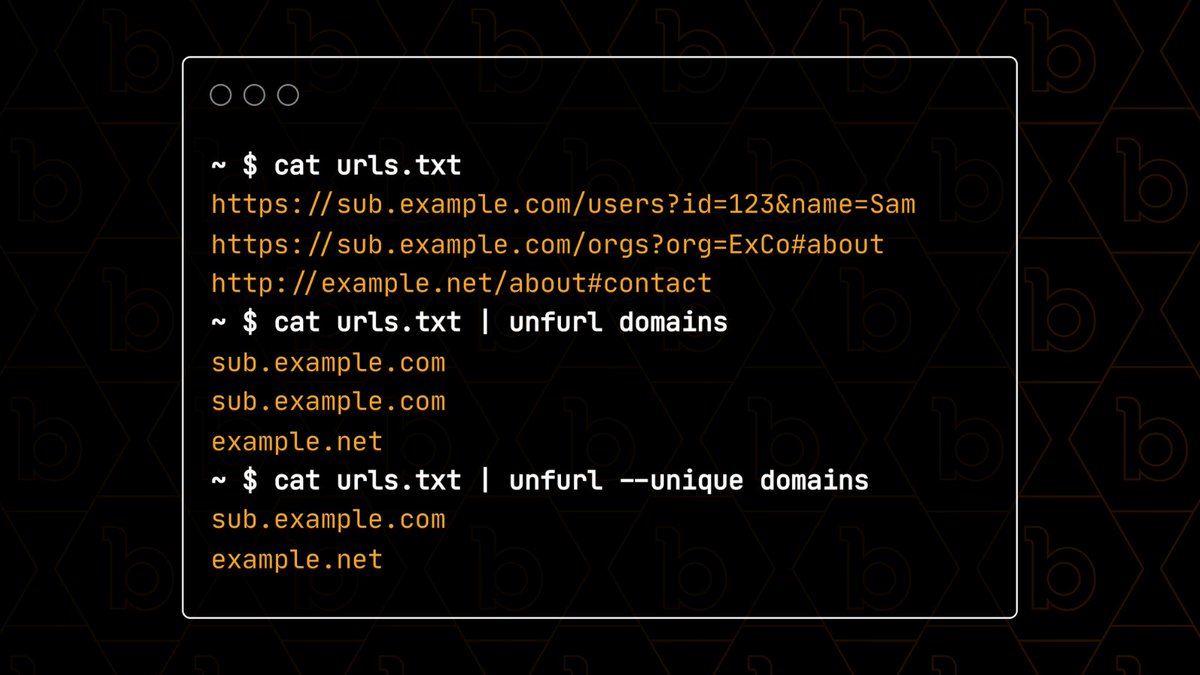
![N$ (@nav1n0x) on Twitter photo Make sure to test mobile endpoints, not just mobile apps—test m.target.com. Mobile front-ends often run on separate infra, different WAF policies with different code base for huge sites like gaming/chat etc, hiding unique vuln surfaces...#BugBounty #SQLi #SQLMap [1/n] Make sure to test mobile endpoints, not just mobile apps—test m.target.com. Mobile front-ends often run on separate infra, different WAF policies with different code base for huge sites like gaming/chat etc, hiding unique vuln surfaces...#BugBounty #SQLi #SQLMap [1/n]](https://pbs.twimg.com/media/Gqj9VM2WYAADafJ.png)