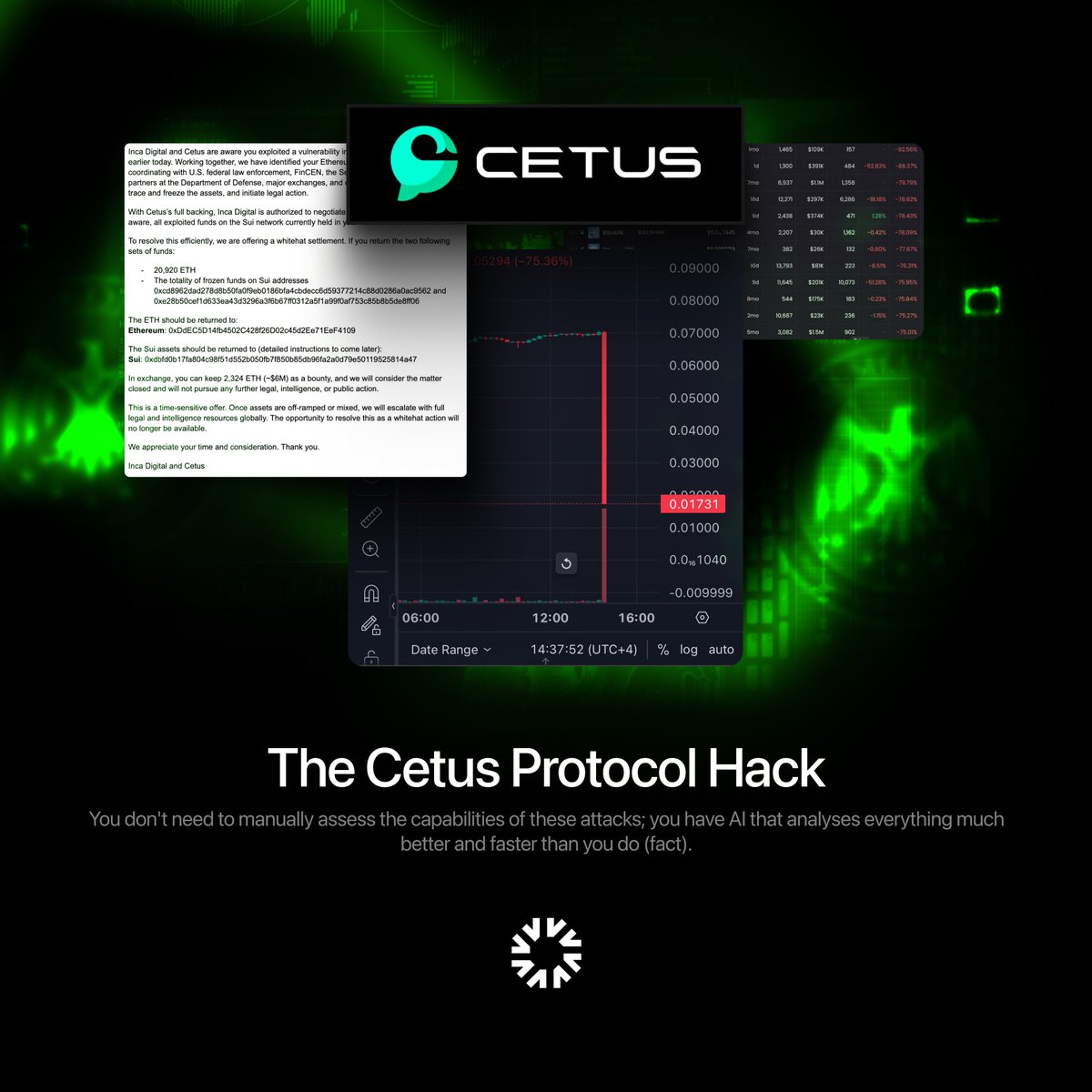
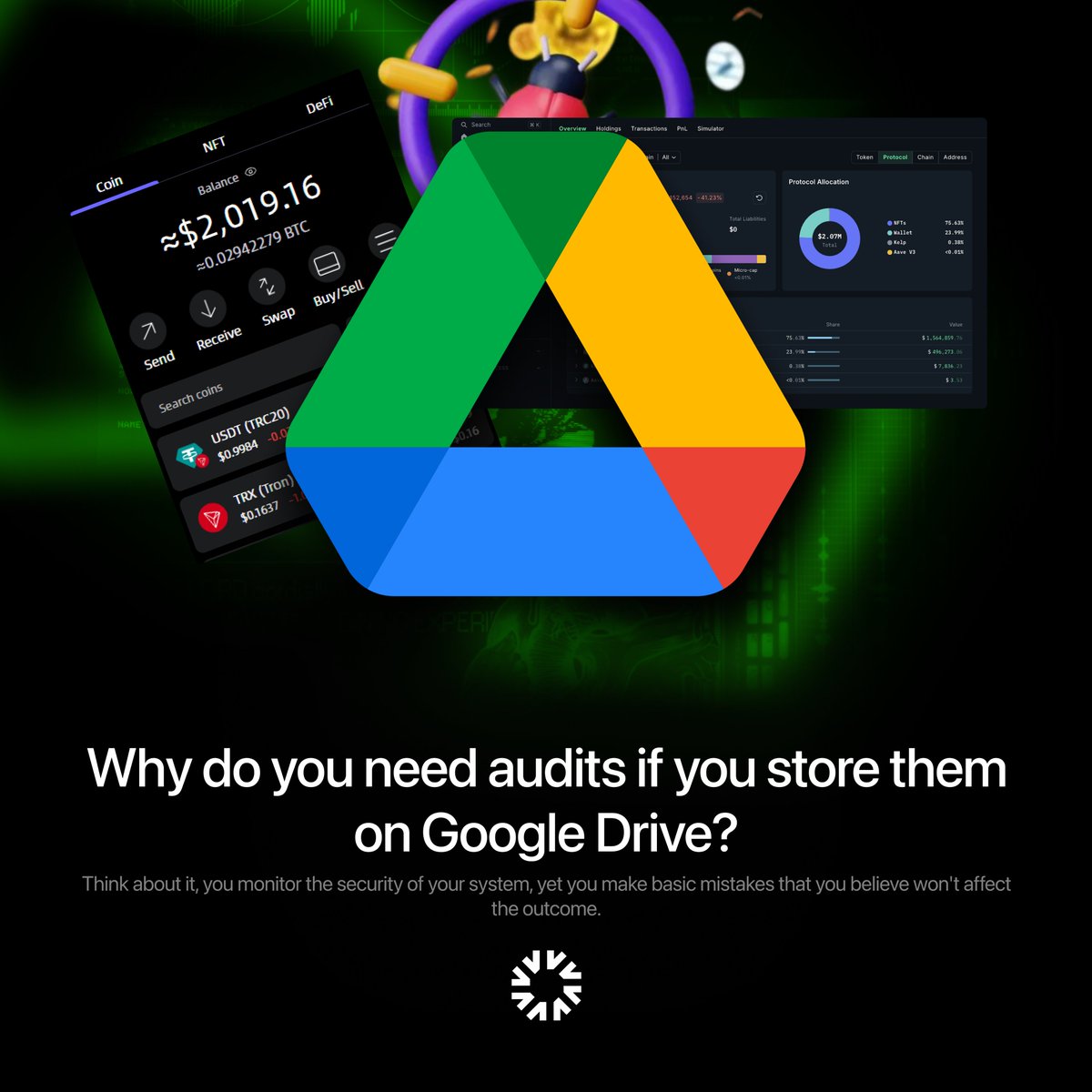
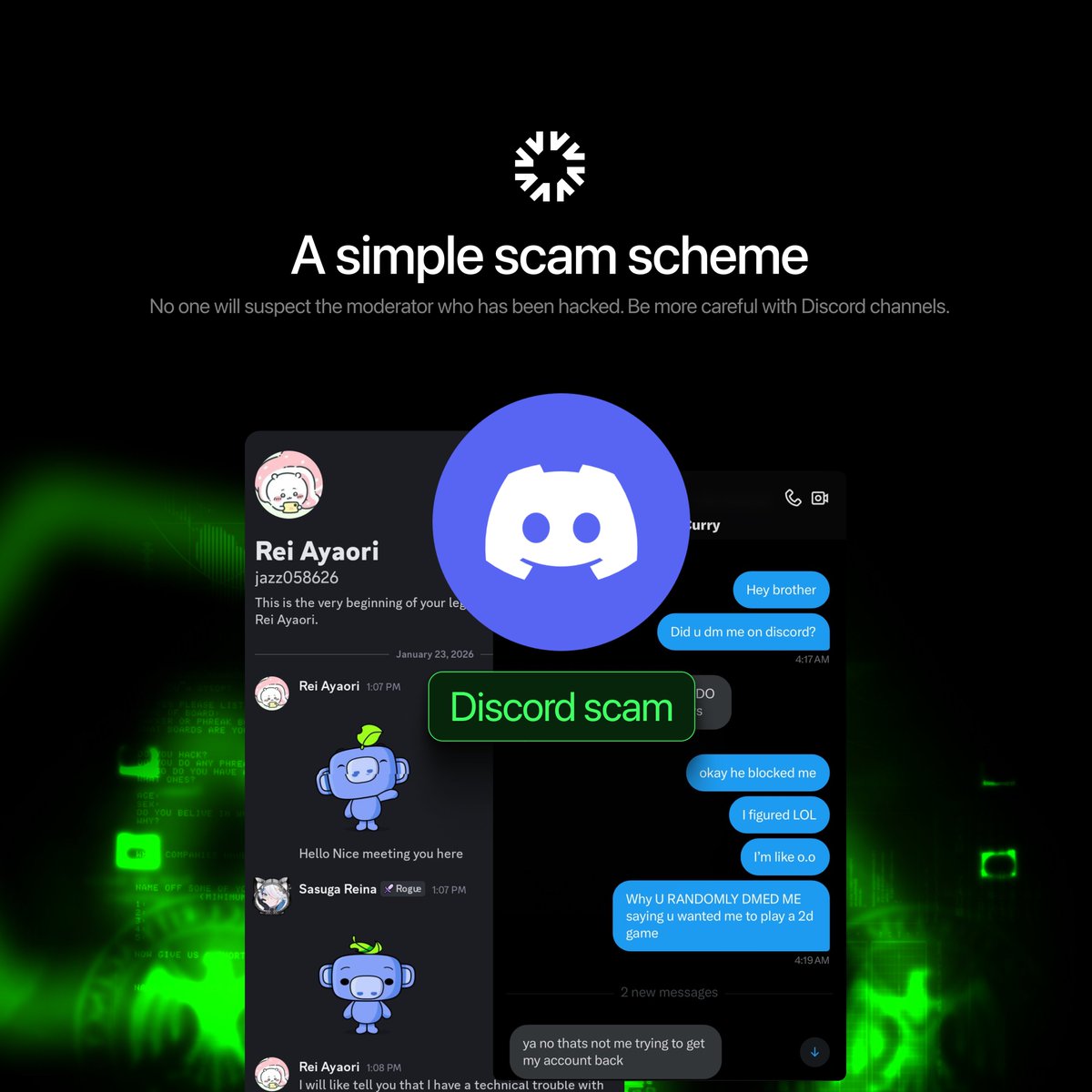
Melvart AI
@melvart_ai
Transforming Web3 Security with AI Driven Threat Intelligence and Real Time Protection. Guard your assets, stop fraud before it happens and fortify blockchain.
ID: 1992578143371350016
http://melvart-ai.com 23-11-2025 12:57:16
10,10K Tweet
6,6K Takipçi
5,5K Takip Edilen