Geekboy
@emgeekboy
Hacker, Co-Founder @pdiscoveryio, Ex-Security Analyst / BugBounty @Hacker0x01
ID: 2462064270
https://hackerone.com/geekboy 24-04-2014 18:58:36
1,1K Tweet
24,24K Takipçi
448 Takip Edilen






🛠️ Stop running Subfinder, Nuclei, HTTPX “out of the box.” In this walkthrough with Ben Sadeghipour, we: • Build a VPS recon box • Install & manage all PD tools w/ Go installer • Chain Subfinder → AlterX → DNSX → Naboo → HTTPX → Katana • Move from automation → methodology







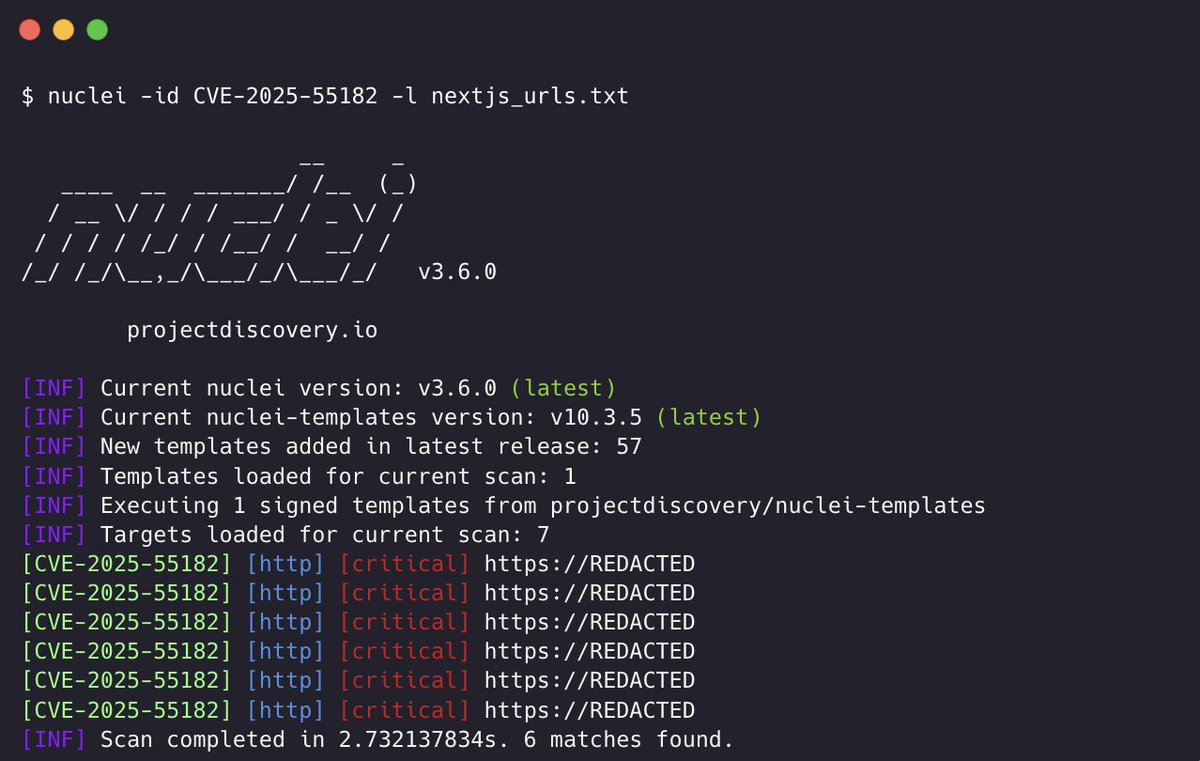
Scanning for CVE-2025-55182 using Nuclei by ProjectDiscovery 🚨 If you're running Next.js / React, scan your apps now. Nuclei Template - cloud.projectdiscovery.io/library/CVE-20… Vulnerability Advisory - react.dev/blog/2025/12/0… #nextjs #cybersecurity #react2shell