Hubert Schillmeier
@bertolino678
ID: 2792877965
29-09-2014 21:10:45
391 Tweet
11 Takipçi
30 Takip Edilen


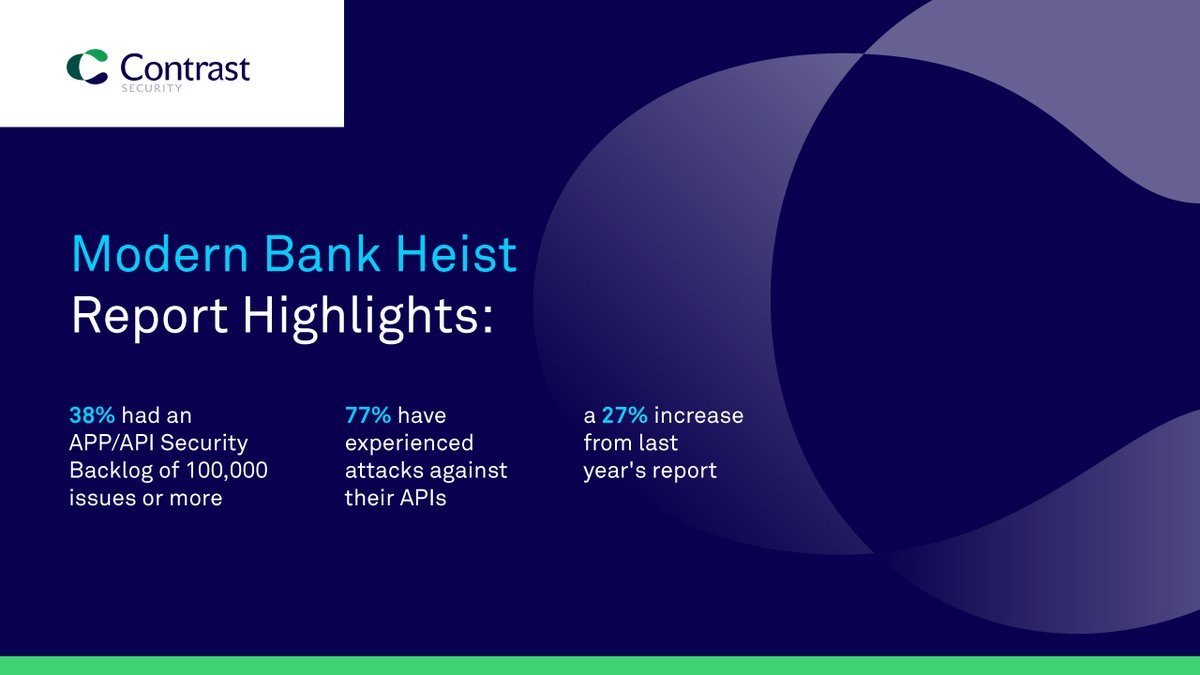
Last year, Bank of America customers data was exposed in a service vendor #cyberattack revealing their names, Social Security numbers, credit cards, & account numbers. Hear insights from Tom Kellermann & other experts in @ITSecurityGuru's article: itsecurityguru.org/2024/02/14/cyb…


In Texas on March 26th? Join our CTO & Co-Founder, Jeff Williams and OWASP® Foundation at NI in Austin! He'll be diving deep into Runtime Security, the automated approach that adds robust trust boundaries to your applications, without any code changes. RSVP for free: eventbrite.com/e/owasp-austin…




Our Co-Founder and CTO, Jeff Williams, chatted with The Application Security Podcast on how Runtime Security is the modern approach to #DevOps! Seamless testing, faster feedback loops & more, listen now: open.spotify.com/episode/5vPVpa…




Another month, another CISO Insights roundup from David Lindner ! This month he covers #API attacks rising to 1/3 of web attacks, the first AI regulation act, and more! Don’t miss the March insights: contrastsecurity.com/ciso-weekly-in…





Source code theft is a growing threat in cybersecurity. Criminals are exploiting stolen code for targeted attacks to expose #vulnerabilities. Read thoughts on this rising threat from our Co-Founder and CTO Jeff Williams: cacm.acm.org/news/the-risks…


Curious how Day Two DevOps practices can enhance your #SDLC? Hear from our very own, Larry Maccherone as he joins the Techstrong TV panel to discuss observability, testing, and SRE. Don’t miss these insights from industry experts: youtube.com/watch?v=tKkkzx…