Nick Chalard
@autow00t
Infosec journeyman, Progressive Trance/House fanatic, always looking for the devil in the details.
ID: 796908637
01-09-2012 21:25:40
24 Tweet
71 Takipçi
544 Takip Edilen



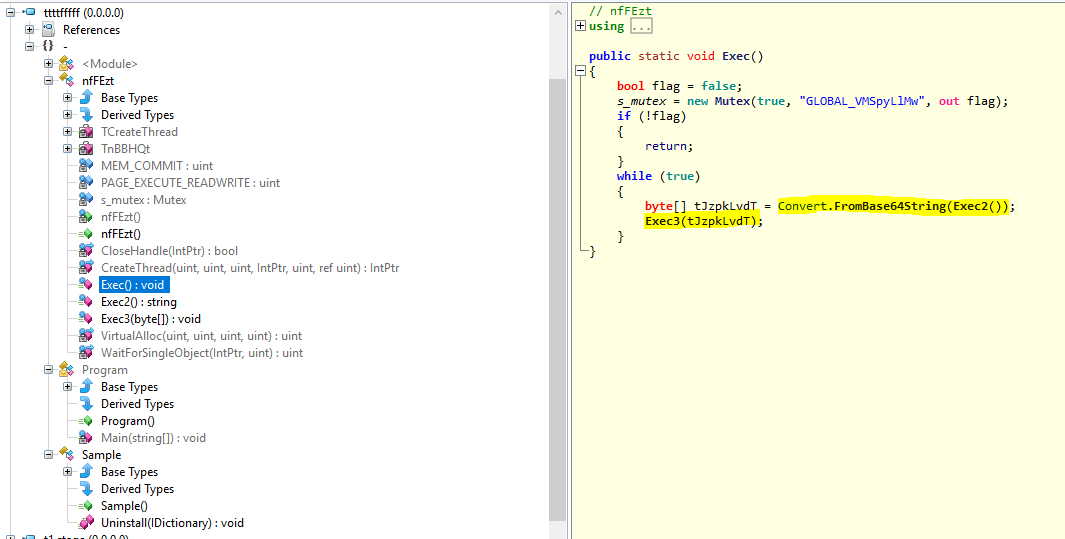
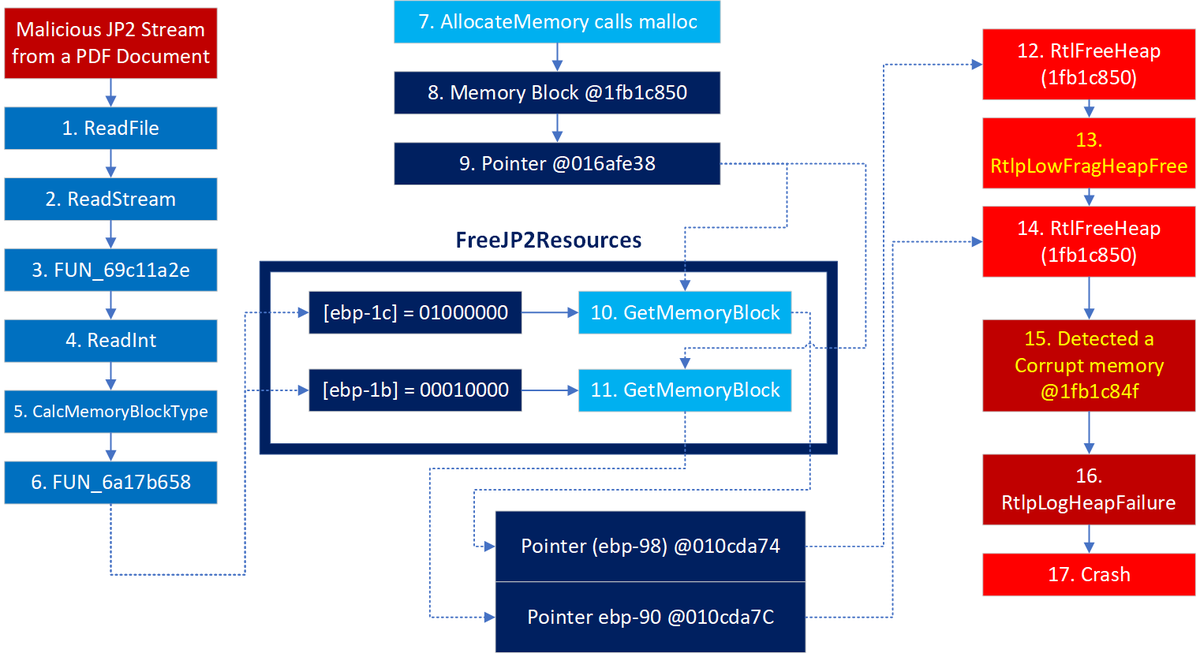
Wonder how registration-free #COM interop works and how #redteamer|s can use it to load #NET assemblies (using #ActCtx COM server in #PowerShell and #Jscript)? Read our new short blog post by Malwrologist inquest.net/blog/2019/5/30…


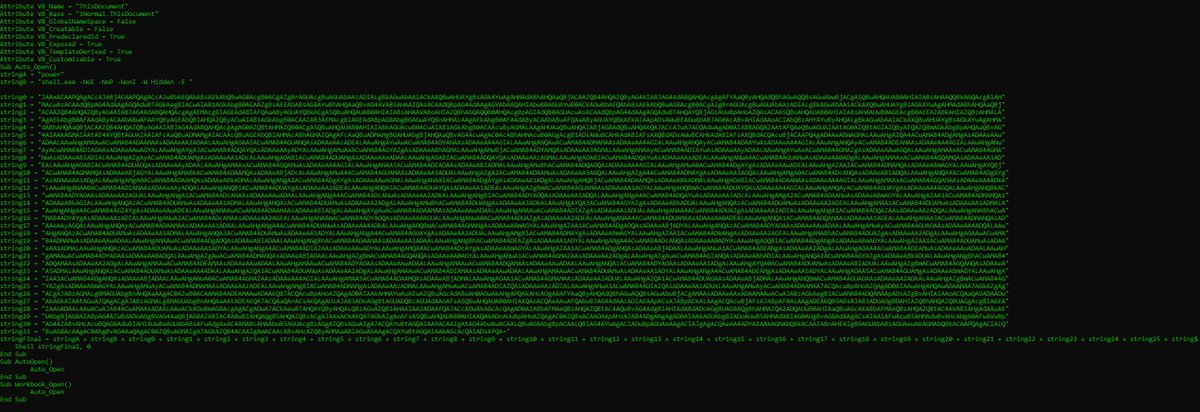
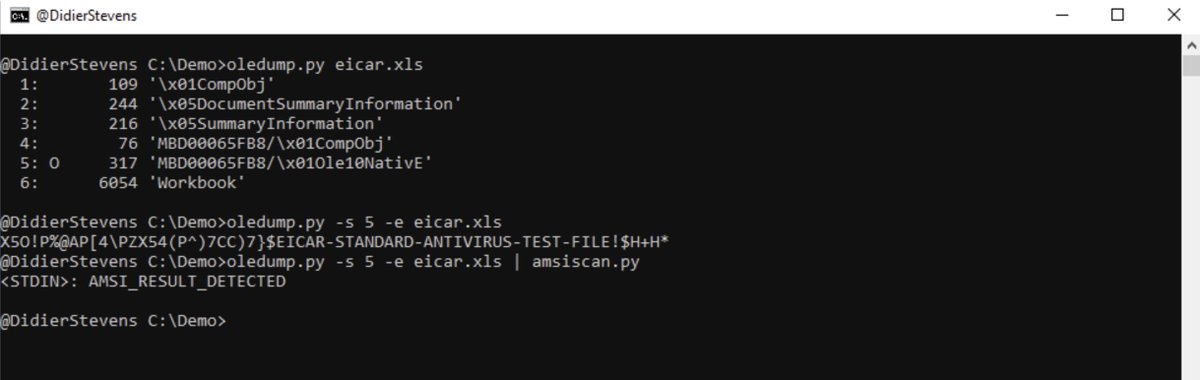
Check out Didier Stevens new tool amsiscan.py. amsiscan.py is a Python script that uses Windows 10’s AmsiScanBuffer function to scan input for malware. It reads one or more files or stdin. blog.didierstevens.com/2019/06/13/new…


Our new blog is out! Ransomware in Your Stocking, William MacArthur describes the increasing danger of ransomware going into the future. There are sample hashes and a map that shows the nationally widespread hits on state and federal utilities. inquest.net/blog/2019/12/2… #cybersecurity





Once again, Microsoft will be keeping the Defenders busy. Now to watch the wave of iterations, collect samples, and improve detection.... DDE --> Equation Editor --> CVE-2021-40444 Find useful info here: inquest.net/blog/2021/09/1… #CVE202140444 #0day Nick Chalard Dmitry Melikov


Probably the easiest CVE number to memorize, also scary enough to be hard to forget. Disable that ActiveX in Internet Explorer, also stop using Internet Explorer. 😆 Thanks for the support on this one William MacArthur Pedram Amini Josiah Smith Dmitry Melikov

We are sharing this visual for tracking threat actors/groups related to the current #ukraine conflict. The content was collected from various sources within the #infosec community. Special thanks to all involved. William MacArthur Nick Chalard J. A. Guerrero-Saade


An update our previous graphic we shared on the cyber-front of the #ukraine conflict. This content was collected from various sources and collaborations within the #infosec community. Special thanks to all involved. William MacArthur Nick Chalard J. A. Guerrero-Saade Jon Gorenflo 🇺🇦🌻


As a follow up to the previous graphic outlining threats affecting #Ukraine, here is a high level blog on observed threats. Big thanks to the #infosec community for making this possible, #SlavaUkraini William MacArthur Nick Chalard J. A. Guerrero-Saade Jon Gorenflo 🇺🇦🌻 inquest.net/blog/2022/04/0…




I follow @highcontrastrec for the #remixcompetition pack of Ronald van Gelderen track ‘This Way’ #TranceFamily popupstore.highcontrastrecords.com