R4Y
@_0xr4y
Smart contract security researcher
ID: 1842073192375963648
04-10-2024 05:24:21
36 Tweet
55 Takipçi
654 Takip Edilen

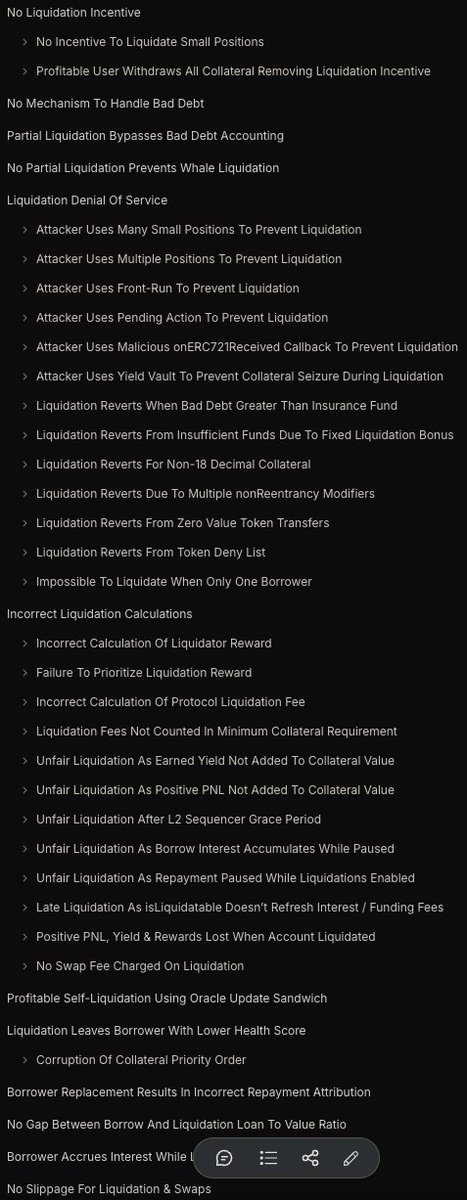
How to study every attack vector in web3 security? Easy step-by-step plan: 1. Go to Cyfrin Solodit 🟪 -> Report Tag and choose an attack vector you want to learn (there are 200+ different tags). 2. Search and read a bunch of articles on the topic (ChatGPT could be quite helpful

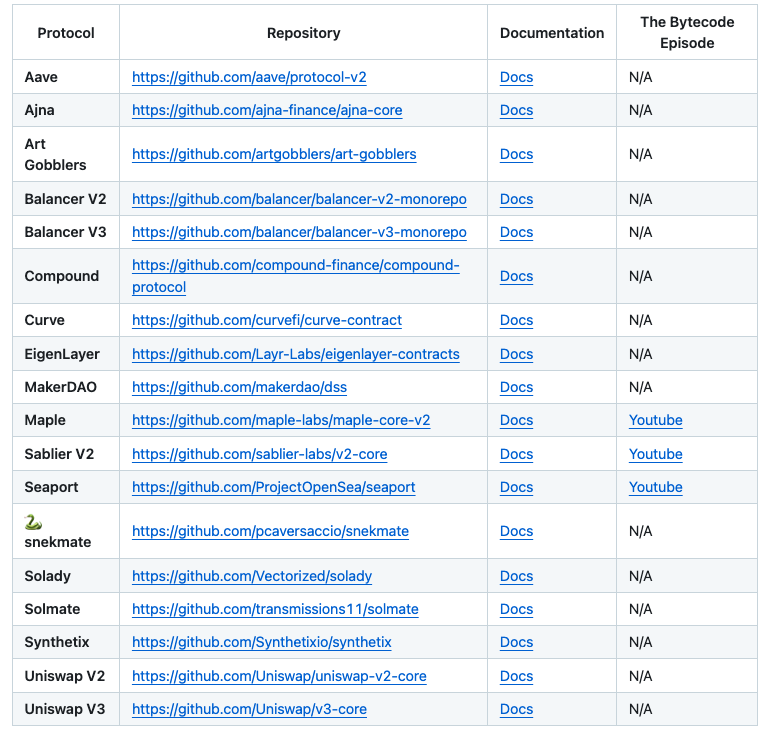
💣 The MOTHER of ALL ALPHA is here. I officially present to you: THE ART OF AUDITING web3-sec.gitbook.io/art-of-auditing The first community-driven resource that consolidates thousands of hours of expertise from the sharpest minds in the industry. I have spent the past 3 months scraping

Back when I was in Web2 hacking, there was a book - "Web Hacking 101" . Which explained all the vulnerabilities in summary, then with real examples. I found that version for Web3 Security/ Smart Contract Auditing as well - zokyo-auditing-tutorials.gitbook.io/zokyo-tutorial… Great work zokyo, thanks <3













🔥To all struggling to understand vulnerabilities in the Estelle Siener smart contract ecosystem: We wrote an article explaining issues, beyond logical vulnerabilities, that can lead to your contract being exploited. arjunasec.xyz/blogs/Soroban%…