0xNinja
@0x_ninja
ID: 1004037132296638465
https://0xninja.fr 05-06-2018 16:28:01
417 Tweet
709 Takipçi
468 Takip Edilen


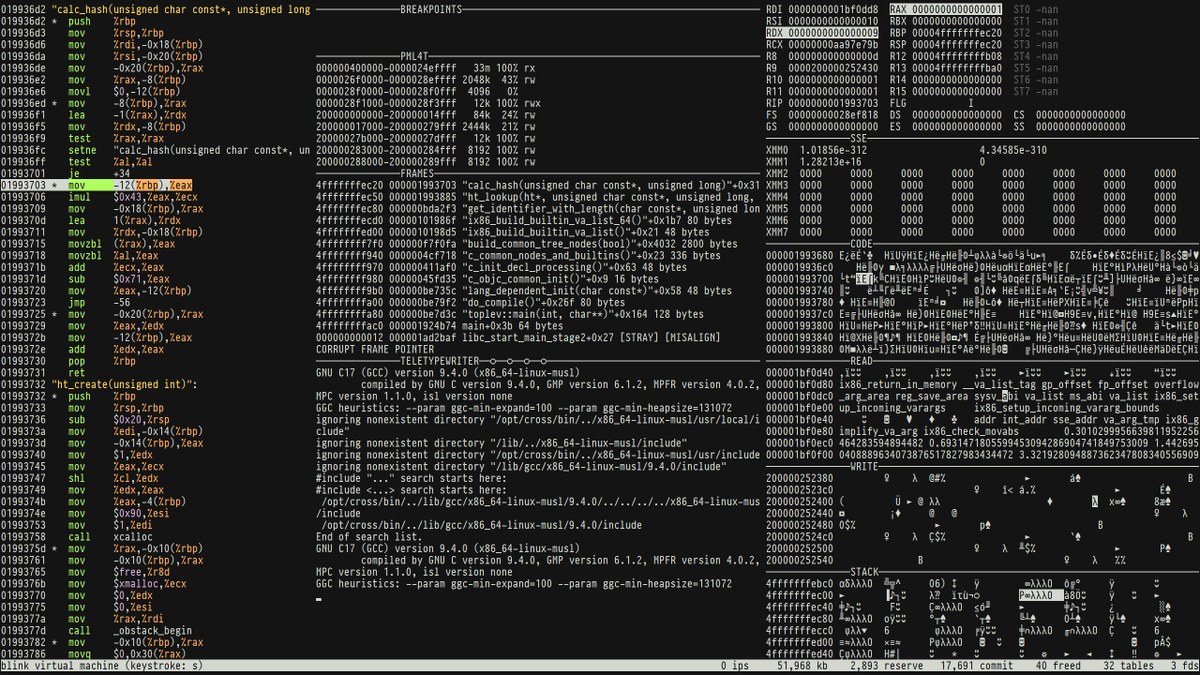
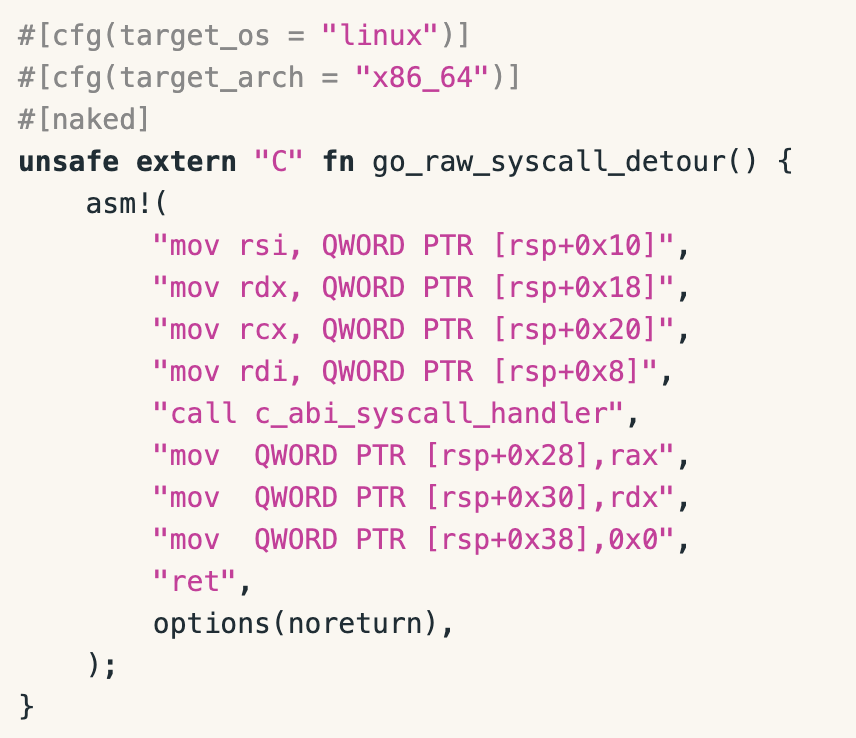
Very interesting blog post by Aviram Hassan 🐻 and @Mehulwastaken on how to hook #Go from #Rust. metalbear.co/blog/hooking-g… #rustlang #golang #programming #hooking #learning #infosec #infotech









Cette année j'ai eu la chance de participer à l'organisation du BreizhCTF 2025. Retrouvez mes corrections sur mon blog zeecka.fr/blog/breizh_20…