
Antelox
@antelox
A Civil Engineer married with Mrs IDA Pro. Sons are WinDbg and OllyDbg. We live in a VM. We eat bread and malware, APT on Sunday
ID: 613281860
http://quequero.org 20-06-2012 09:10:30
5,5K Tweet
5,5K Takipçi
1,1K Takip Edilen









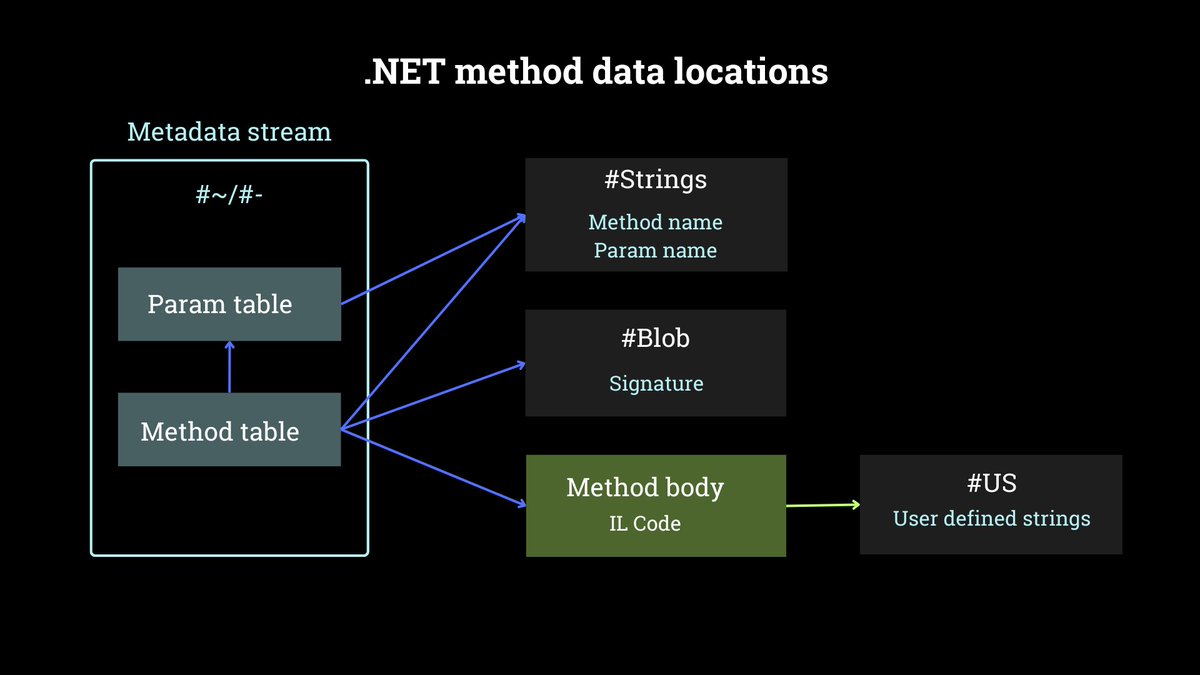
How to use knowledge about .NET structures and streams for writing better .NET Yara signatures. E.g. IL code patterns, method signature definitions, GUIDs, compressed length. #100DaysOfYara #GDATATechblog G DATA Global #GDATA gdatasoftware.com/blog/2025/04/3…





Interested in learning how to build a lab VM for malware analysis and reversing? You can download a 40+ page chapter on this topic, taken from my book Evasive Malware. Get the PDF from my blog, here: 🤓 evasivemalware.com/EvasiveMalware… CC No Starch Press

















![Zscaler ThreatLabz (@threatlabz) on Twitter photo ThreatLabz has observed Bumblebee distributing DonutLoader embedded with StealC v2.
Bumblebee config: github.com/ThreatLabz/ioc…
StealC config:
C2: http://nispgael[.]biz/7321a45c92764723.php
Botnet ID: winmtr
RC4 key: 140877183e614f06
Expiration date: 10/08/2025 ThreatLabz has observed Bumblebee distributing DonutLoader embedded with StealC v2.
Bumblebee config: github.com/ThreatLabz/ioc…
StealC config:
C2: http://nispgael[.]biz/7321a45c92764723.php
Botnet ID: winmtr
RC4 key: 140877183e614f06
Expiration date: 10/08/2025](https://pbs.twimg.com/media/GwElngtW4AAW466.jpg)

