
Anil Yendluri
@anilcyen
Information Technology, Cybersecurity & GRC Consultant
ID:296073853
10-05-2011 04:41:54
3,7K Tweets
687 Followers
4,8K Following

Kaiser Permanente notifies 13.4M patients of potential data exposure. Online tracking technologies may have transmitted personal information to third-party vendors #Google #Microsoft #Bing & #X . #Cybersecurity #Identity #DataSecurity #Privacy Chuck Brooks
scmagazine.com/news/kaiser-pe…

Top Cybercrime Statistics 2024
Highest cost of a data breach was $5.09 million in the US in 2023
Phishing attacks common cause of data security incidents in 2023 at 41%
Spear-phishing is used by 96% of threat actors to gather intelligence
#Cybersecurity Chuck Brooks Aaron L.


In the rapidly evolving landscape of #cybersecurity , #ArtificialIntelligence emerges as a key player influencing both offensive and defensive cyber operations. Let’s delve into the trends that will define the cybersecurity landscape in 2024. Chuck Brooks Aaron L.
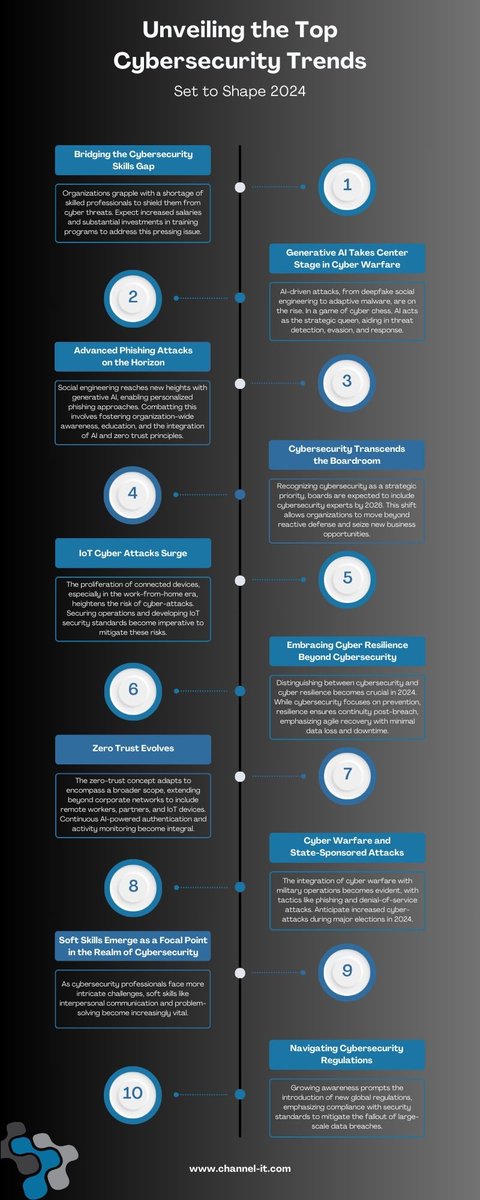

4 Key Cybersecurity Trends to Watch in 2024
1. The Duality of Generative Al
2. Zero Trust Implementation
3. Cloud Security
4. Cybersecurity Complexity
#Cybersecurity #Security #Trends #ArtificialIntelligence #ZeroTrust #CloudSecurity Chuck Brooks Aaron L. Dan Williams


What are the top attack vectors in 2024? How are emerging technologies fueling cyber-attacks?
#Cybersecurity #Security #Attack #ArtificialIntelligence #Deepfake #SupplyChain #Cloud #InternetOfThings #Phishing #Malware #Ransomware #Password #DoS Chuck Brooks Aaron L.


How to prevent a cyber attack
14 ways to protect your business from a cyber attack
#Cybersecurity #Security #Attack #Business #Threat #Spam #Passwords #Employee #Awareness #Encryption #Endpoint #Firewall #DarkWeb #Email Chuck Brooks Aaron L. Dan Williams iCorps Technologies


IOT, DDOS, and other attacks - Cybersecurity Infographics with facts & figures (2024)
#Cybersecurity #Security #Facts #Figures #ArtificialIntelligence #Infographic #Attacks #iot #ddos Chuck Brooks Aaron L. Dan Williams Bob Carver ✭ Verizon Cisco Symantec by Broadcom CSOonline

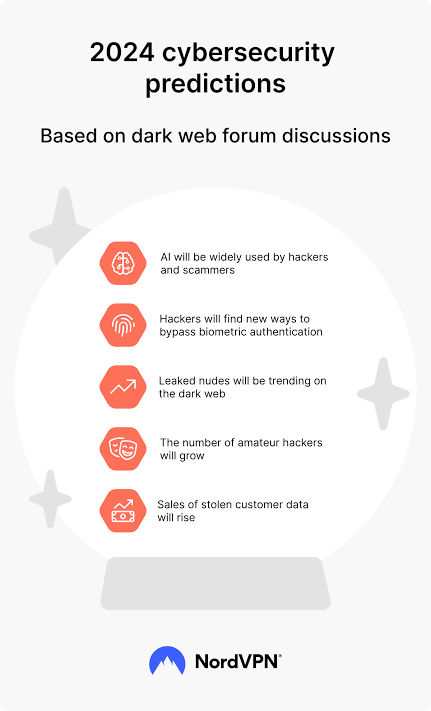
2024 #cybersecurity predictions based on #darkweb #forum discussions
#AI used by #hackers and #scammers
Hackers will find new ways to bypass #biometric #authentication
Leaked nudes will be trending
Amateur hackers will grow
Sales of stolen customer data
Chuck Brooks Aaron L.

Microsoft Corp. is under the gun because nation-state hackers keep finding ways to exploit its products. Yet the unwanted attention serves to highlight just how dominant the world’s most valuable company is in #cybersecurity .
bloomberg.com/news/newslette…
Chuck Brooks Aaron L.


Cybersecurity investigators worry ransomware attacks may worsen as young, Western hackers work with Russians
cbsnews.com/news/cybersecu…
#Cybersecurity #Security #Attack #Ransomware #Russia #UnitedStates #UnitedKingdom #Canada Chuck Brooks Aaron L. Dan Williams Bob Carver ✭

U.S. Federal Agencies Ordered to Hunt for Signs of Microsoft Breach and Mitigate Risks
thehackernews.com/2024/04/us-fed…
CISA emergency directive ED 24-02 #Cybersecurity #Security #Breach #Threat #Risk #Microsoft #Infrastructure #UnitedStates Chuck Brooks Aaron L. Cybersecurity and Infrastructure Security Agency Microsoft

Financial Sectors Lost $20 Billion Over the Past 20 Years
cybersecuritynews.com/financial-sect…
In a startling revelation, #cyberattacks have surged to more than double their pre- #pandemic levels, casting a long shadow over global #financial #stability .
#Cybersecurity #Security Chuck Brooks

The global AI in Cybersecurity market, expected to expand from USD 22 billion in 2023 to around USD 163.0 billion by 2033, demonstrates a promising growth trajectory with a CAGR of 22.3%.
scoop.market.us/ai-in-cybersec…
#Cybersecurity #ArtificialIntelligence Chuck Brooks Aaron L.

This year, Crowdfense is expanding its scope to encompass additional major research fields like Enterprise Software, WiFi/Baseband, and Messengers and is proposing a larger 30 million USD acquisition program.
cybersecuritynews.com/crowdfense-30-…
#Cybersecurity Chuck Brooks Aaron L.

In 2024, organizations need to take proactive measures to fortify their infrastructure and protect sensitive data, as decisions made today will shape the cybersecurity landscape of tomorrow.
forbes.com/sites/forbeste…
#Cybersecurity #Security Chuck Brooks Aaron L. Forbes

#British #police have opened an #investigation into explicit messages sent to a #lawmaker as part of an alleged #sexting #scam #targeting #legislators , in the latest #cybersecurity scare to hit #parliament .
cbsnews.com/news/uk-sextin…
#Security #London Chuck Brooks Aaron L.

Operational TI forms a link between tactical and strategic aspects, providing context and actionable insights on different attacks’ motives and tactics, techniques, and procedures.
forbes.com/sites/forbeste…
#Cybersecurity #Security #Intelligence Chuck Brooks Aaron L. Forbes


The European Union Agency for Cybersecurity (ENISA) has published a comprehensive list of the top ten emerging cybersecurity threats anticipated to impact the digital landscape by 2030.
cybersecuritynews.com/emerging-cyber…
#Cybersecurity #Security #Emerging #Threats Chuck Brooks Aaron L.
