Anthony Weems
@amlweems
Cloud Vulnerability Research • The opinions stated here are my own, not those of my company.
ID: 14378227
http://amlw.dev 13-04-2008 21:43:53
178 Tweet
3,3K Takipçi
267 Takip Edilen

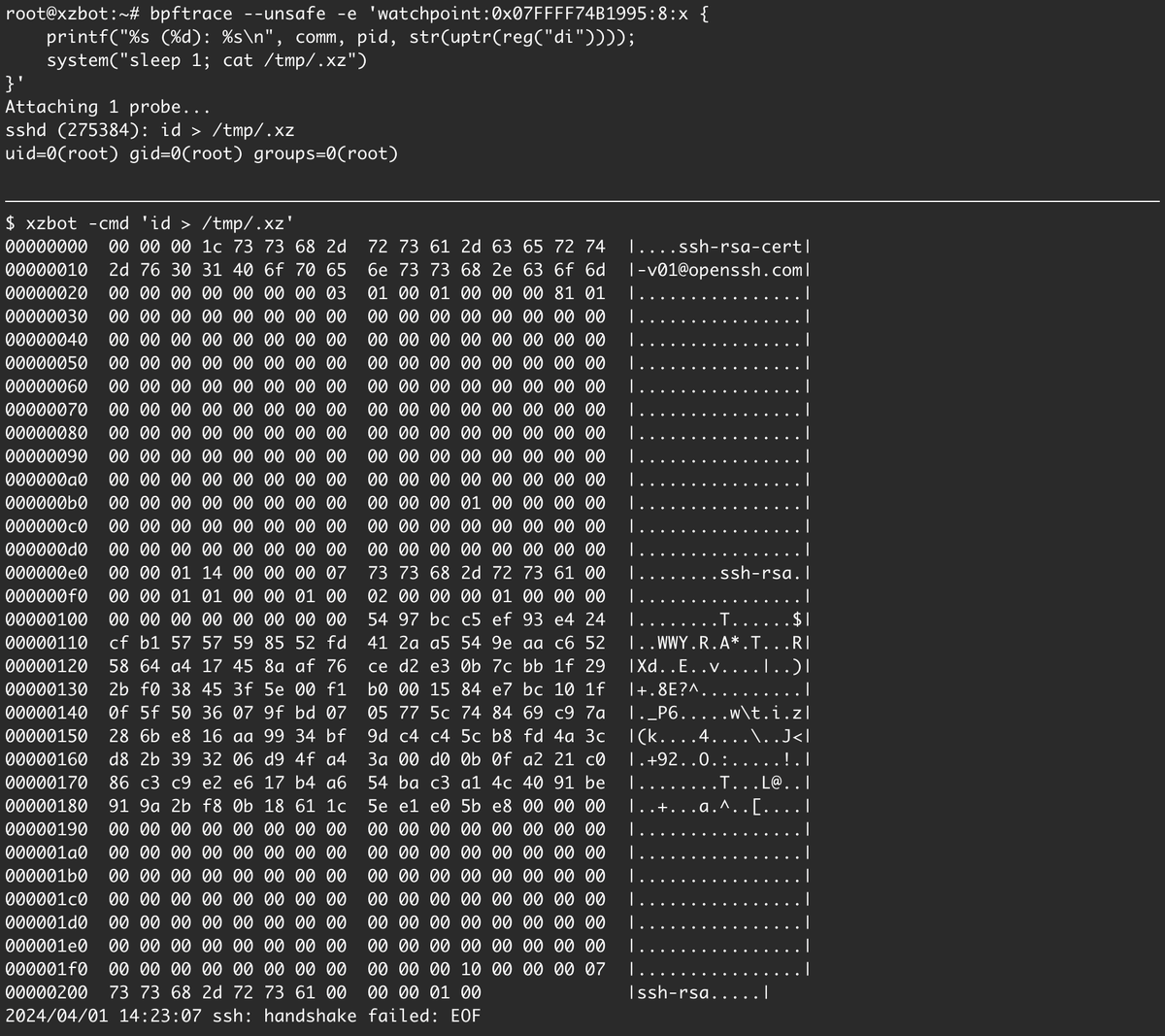
My team Praetorian just published our work in reverse engineering the Proxylogon patches for CVE-2021-26857, CVE-2021-26855, and CVE-2021-27065. I learned a lot more about Exchange than I thought I'd ever need, but had a blast. praetorian.com/blog/reproduci…


Just finished Portswigger's new Burp Suite Certification. I've always been a huge fan of the Web Security Academy and this is an excellent capstone on the labs. Thanks PortSwigger for all the educational content! #burpsuitecertified

I'm really excited for this video! I got a chance to collab with LiveOverflow 🔴 and share the process for discovering the localhost bypass for CVE-2021-45046 with code review and differential fuzzing. :)




github.com/google/securit… Our research on the deep mines of the JPX standard is now public. I had the pleasure and the privilege to work with Simon Scannell , Anthony Weems and Ezequiel Pereira on this one. Pretty interesting client side info leak vector :)


Very excited to present this with Anthony Weems! See you in Berlin! (Ezequiel Pereira and 那个火饺🦆(JJ)) were also working on that project and will also be there :)

The Mines of Kakadûm: Blindly Exploiting Load-Balanced Services by Simon Scannell and Anthony Weems is now live!


Excited to share this blog post about server-side memory corruption that my team exploited in production. Shout-out to Simon Scannell, Ezequiel Pereira, and 那个饺子🦆(JJ) - this was a very fun project. :-) bughunters.google.com/blog/622075742…