Aliakbar Zahravi
@aliakbarzahravi
Malware Reverse Engineer and Team Lead at @TrendMicro - Tweets are my own
ID: 771198948207833089
01-09-2016 04:12:12
51 Tweet
278 Followers
13 Following


🚨 We are excited to release our latest blog on Void Arachne campaign and in-depth analysis of Winos 4.0 C&C framework. trendmicro.com/en_us/research… #RAT #Deepfake #infosec #cybersecurity #backdoor #cyberthreats #AI #CyberAttack #malware Shoutout: Peter Girnus




Happy Patch Tuesday! Both #Microsoft and #Adobe have relatively small releases, but Microsoft is patch 6 bugs currently under active attack. The Dustin Childs has the full breakdown of this month's release at zerodayinitiative.com/blog/2025/3/11…

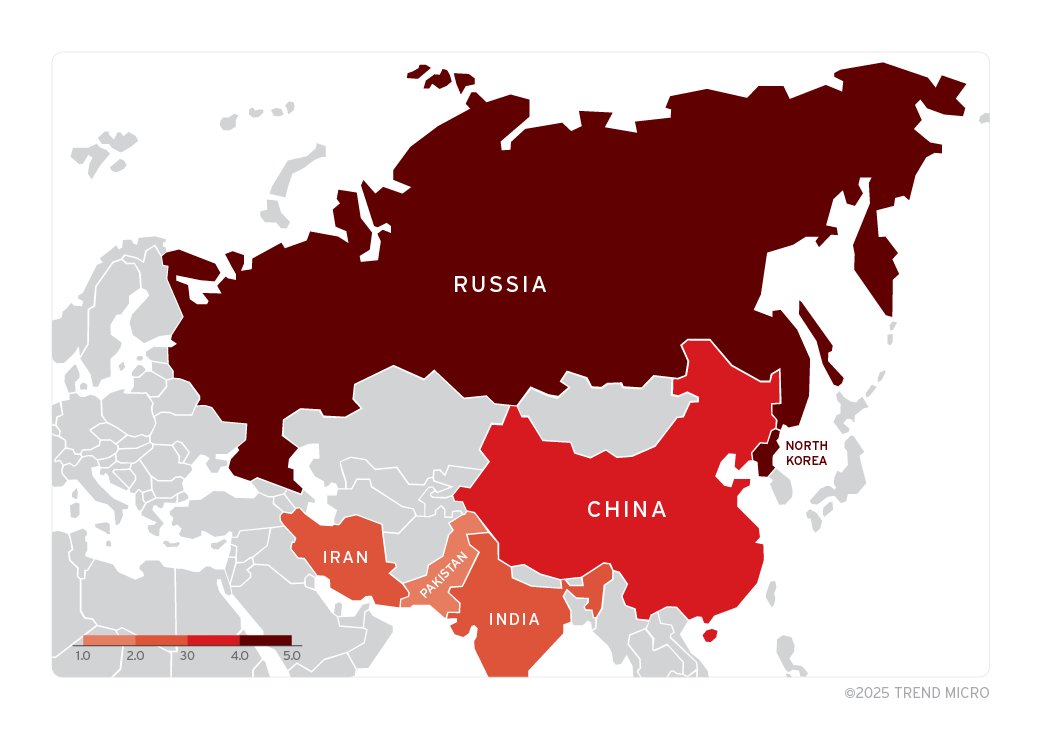
While various state-sponsored APT groups, the Trend Zero Day Initiative Threat Hunting team discovered nearly 1,000 malicious .lnk files exploiting ZDI-CAN-25373. State-sponsored APT groups from North Korea, Iran, Russia, and China have been using ZDI-CAN-25373 for cyber espionage and data theft