AccessDenied403
@adcdiii
Share my learning journey in the field of Blockchain, Crypto and Web3.
Security Engineer @taurus_hq
ID: 1540271775250096129
https://rya-sge.github.io/access-denied/ 24-06-2022 09:53:28
945 Tweet
191 Takipçi
3,3K Takip Edilen


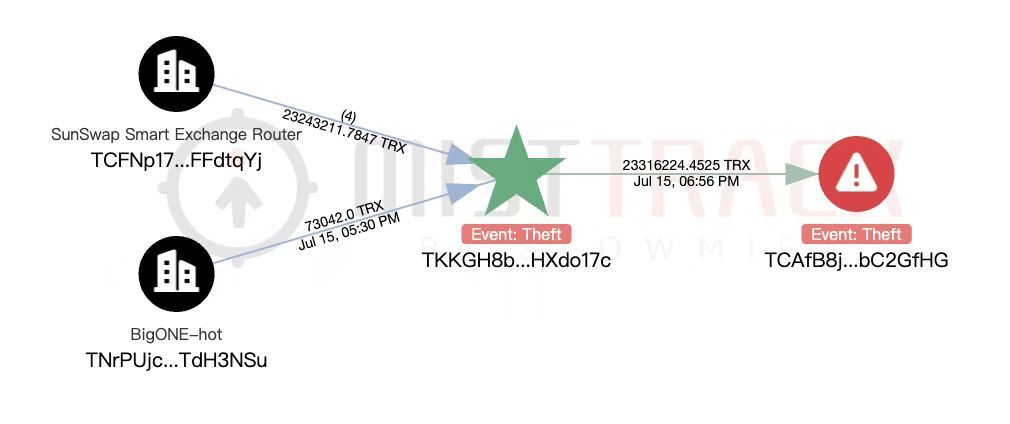
Hi everyone, At CoinDCX : India Ka Crypto Coach, we have always believed in being transparent with our community, hence I am sharing this with you directly. Today, one of our internal operational accounts - used only for liquidity provisioning on a partner exchange - was compromised due to a






BlockThreat - Week 31, 2025 💙 Sponsored by Coinspect Security 🧟 $3.5B stolen from LuBian miner in 2020! 🧑⚖️ Samourai Wallet defendants plead guilty. 💸 User lost 401 ETH to the old Multichain exploit ☹️ SuperRare typo. $730K stolen.







best security token: CMTAT v3 github.com/CMTA/CMTAT/rel… insane level of documentation github.com/CMTA/CMTAT/blo… by AccessDenied403