
adam shostack
@adamshostack
Done with Twitter. Don't expect responses.
Threat Modeling: Designing for Security. Working to reduce bad security outcomes.
ID: 18783289
https://shostack.org 08-01-2009 22:56:09
19,19K Tweet
10,10K Followers
525 Following







Back in the day, I did some cool #security #UX work with adam shostack and Rob Reeder at Microsoft. Now Beyond Identity is recruiting for a security-savvy UX designer. Any of my #infosec peeps interested? linkedin.com/posts/allan-zi…






Synology created a patch to address the zero-click vulnerability that researchers at Midnight Blue found, but adam shostack spotted this explanation about the patch:
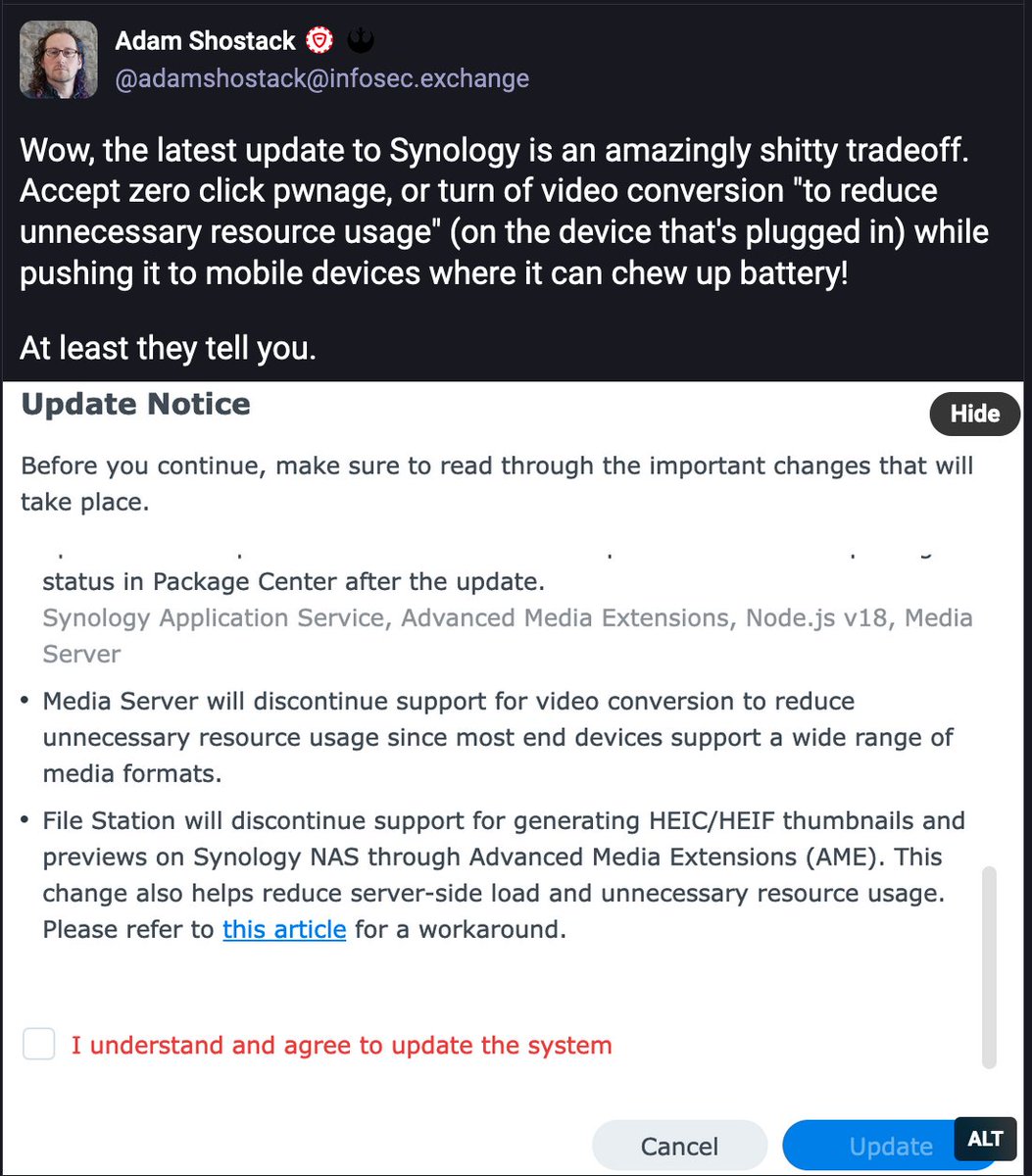

adam shostack Kim Zetter Midnight Blue When I saw those release notes I assumed Synology were trying to reduce codec license fees. Whatever the reason, as you say, security patches should not come at the cost of features.






