Zynx
@_zynx_
CISO in sweden, all tweets are my own.
ID: 96839108
14-12-2009 20:56:41
2,2K Tweet
130 Followers
528 Following




Lotte Card said a cyberattack exposed the personal data of 2.97 million users. About 280,000 customers face direct risks of unauthorized card use. The Korea Herald 코리아헤럴드 #cybersecurity #cyberattack #databreach #korea









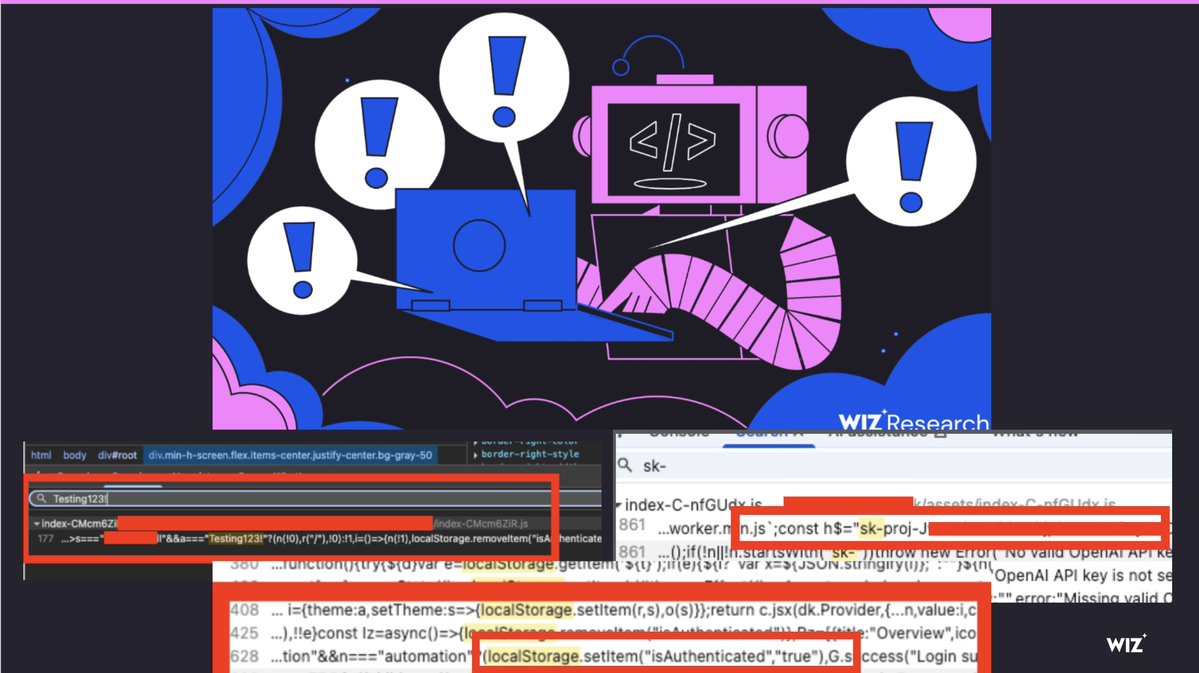
Super cool potential ASLR leak via dictionary hashing by Jann Horn - [email protected]! googleprojectzero.blogspot.com/2025/09/pointe…






SonicWall: Firewall configs stolen for all cloud backup customers - Bill Toulas bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…