Sidharth V
@_retr0ds_
Reverse Engineer | Malware Analyst |
Team Lead @teambi0s | CSE undergrad @amritaedu
ID: 1471417656485969921
https://retr0ds.github.io/ 16-12-2021 09:51:35
47 Tweet
201 Followers
504 Following










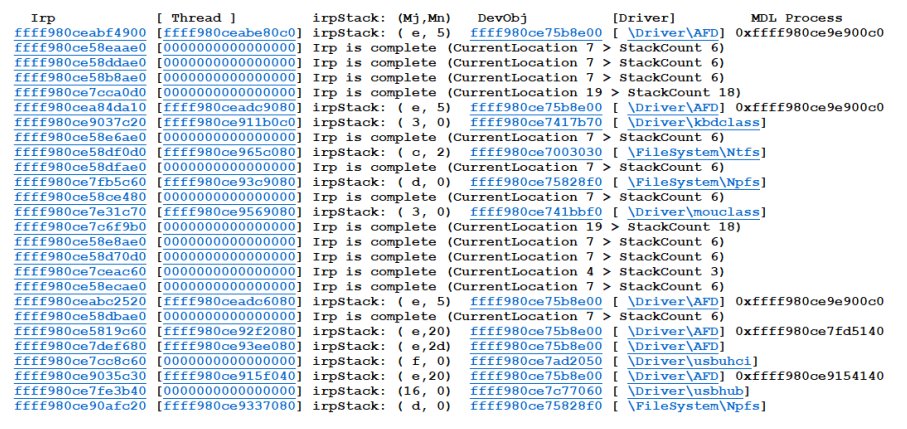
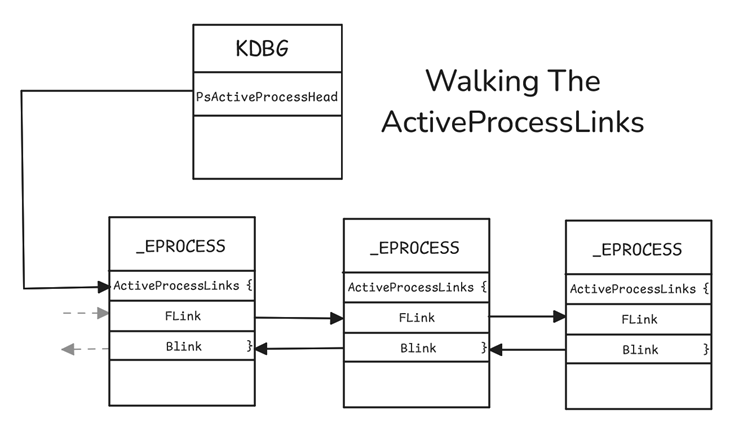
Coauthored an article for SANS Institute with my friend Abdelrhman on "Analysis of Virtual Address Descriptors" for hunting malwares, ransomware keys, notepad abuse/data recovery and detailed windows internals of a process and its memory structure. sans.org/blog/the-analy…







I'm happy to share that I've received a $13,337 bounty from Google for a high-impact vulnerability I reported. My thanks to the Google VRP (Google Bug Hunters) team. A full technical write-up is coming once the fix is confirmed. #bugbounty #infosec #cybersecurity #GoogleVRP