Remsio
@_remsio_
PHP security lover
🥷
ID: 1089145300915236864
26-01-2019 12:57:29
474 Tweet
811 Takipçi
275 Takip Edilen

I hope everyone got some rest after DownUnderCTF this weekend. My colleague hashkitten wrote up a blog post on a novel technique for SQL Injection in PDO's prepared statements, required to exploit the “legendary” challenge, which only got one solve: slcyber.io/assetnote-secu…


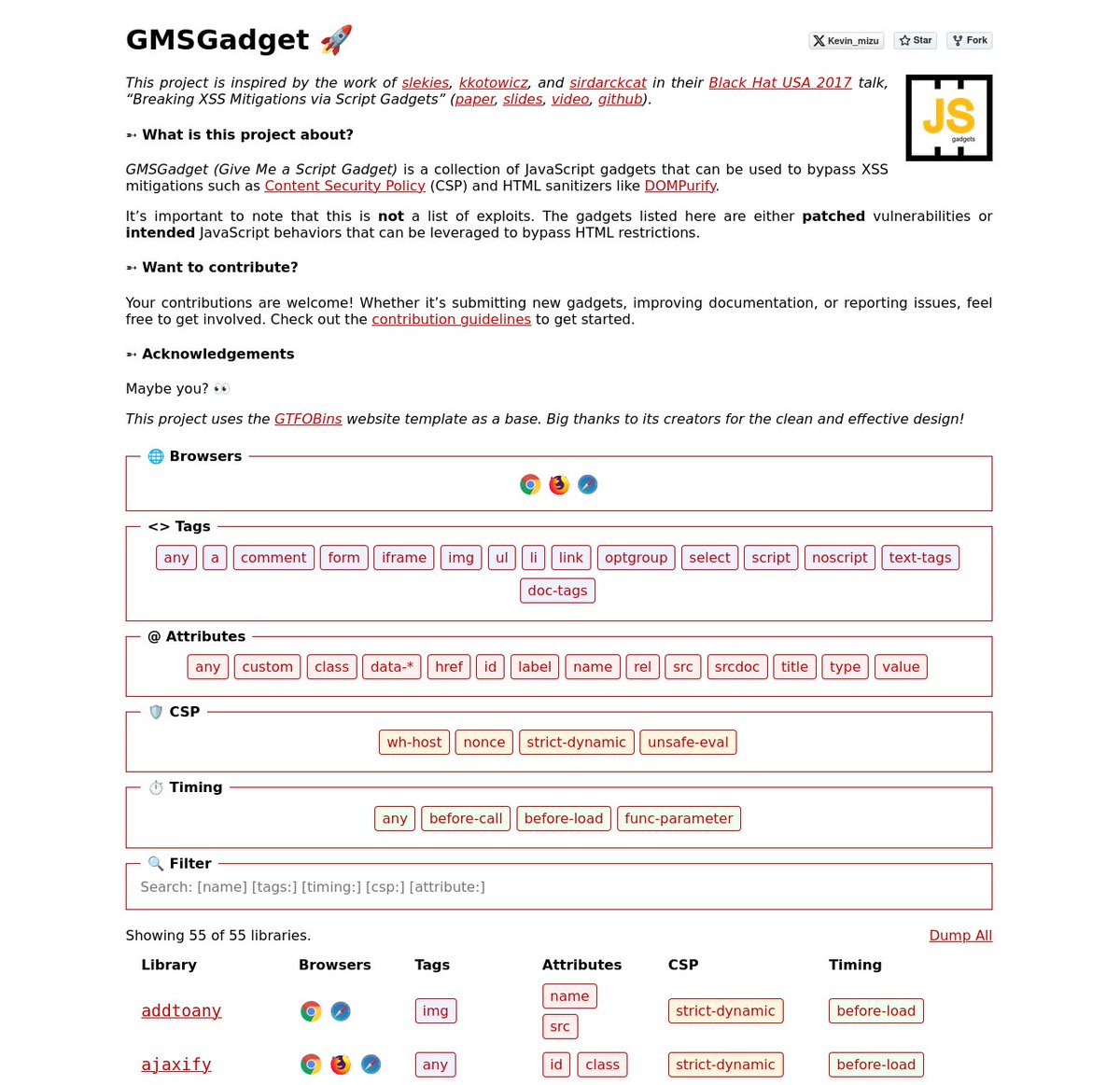
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4













Afterwards, the great Quentin Roland took the stage, also at #OrangeCon, to present the authentication relay techniques he discovered earlier this year. As always, he illustrated his talk with a demo, showing that these techniques can be applied to real-world AD environments. 🔥



🚨 Our two ninjas, Mallo and Thibaut Queney, found two vulnerabilities on Snipe-IT that can be chained by an authenticated attacker to achieve remote command execution on the server. Read the security advisory for more details: synacktiv.com/advisories/sec…