Q5Ca
@_q5ca
Chief Remote Work Officer at @u0Kplusplus
ID: 932190929020006401
https://duongq5ca.substack.com/ 19-11-2017 10:16:51
217 Tweet
782 Takipçi
349 Takip Edilen










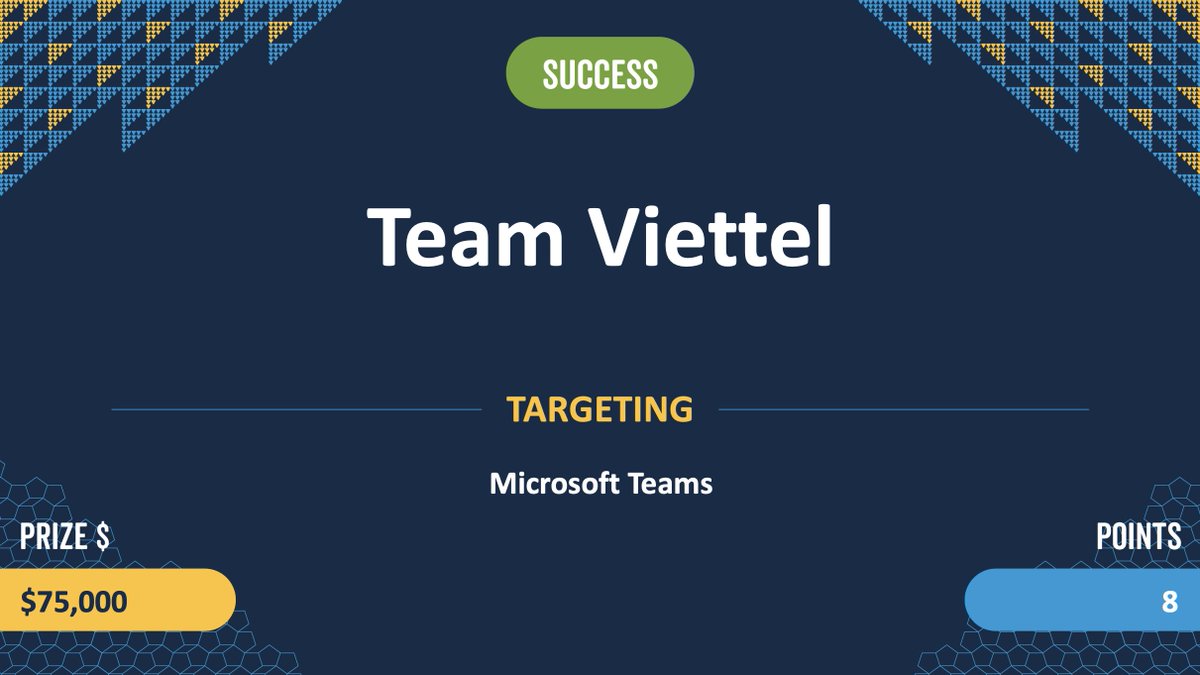
Success! Nguyen Xuan Hoang, Pham Khanh, and Q5Ca from Team Viettel (VCSLab) used a 2-bug chain in their attempt against Microsoft Teams. They earn $75,000 and 8 Master of Pwn points.