
caon
@_caon__





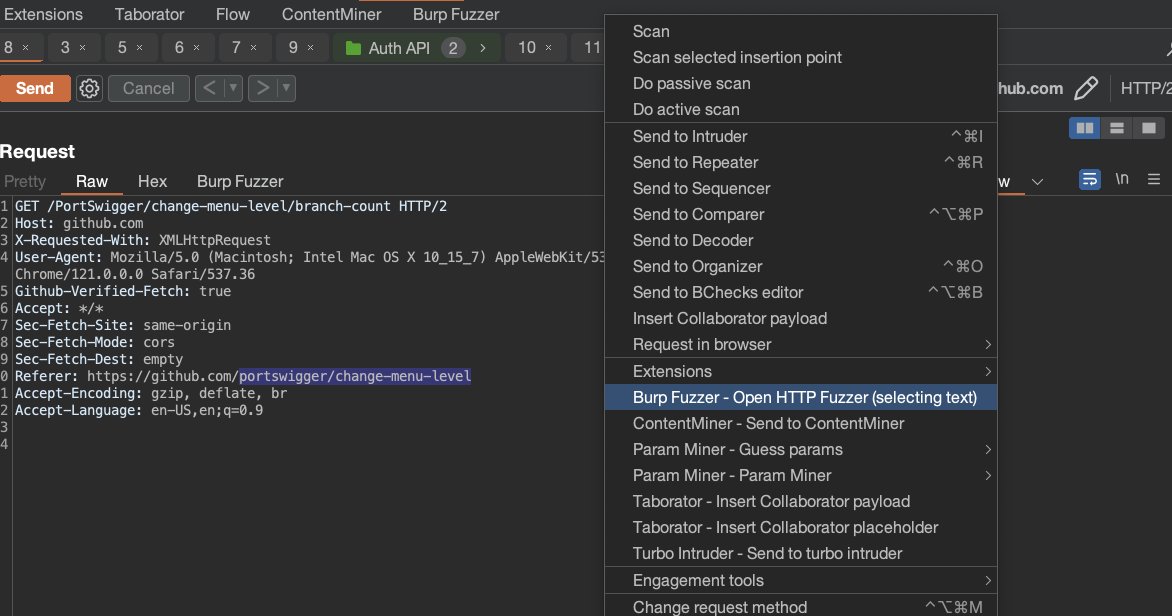
My friend Black Turtle just suggested a time-saving extension in Burp Suite that enables you to perform Burp Extension actions without having to go through a lot of boring clicks😂 github.com/portswigger/ch… #bugbountytips #bugbounty #infosec #cybersecurity







Where there’s bug bounty, there’s #Bugcrowd. 😉✨ We’re honored to have supported the Bug Bounty Village Brazil at H2HC in #Brazil, big thanks to bsysop! Seeing the hacker community come together with such passion was nothing short of amazing (as always). 🥲 Huge thanks to the organizers,



Hi HACKERS, here are my suggestions for the Top Ten (New) Web Hacking Techniques of 2024 PortSwigger PortSwigger Research : • “Another Vision of SSRF” (ph0r3nsic 🕷️) • “Unveiling TE.0 HTTP Request Smuggling” (bsysop) • “Supply Chain Attacks: A New Era” (Caue) If you haven’t




RFC 2047 "encoded-word" is crazy! It lets you smuggle encoded payloads into email addresses and the craziest thing is that some parsers decode it before validation 👇 Shout out to Gareth Heyes \u2028 for this 🔥


![m4ll0k (@m4ll0k) on Twitter photo How to access to company without being part of it with google oauth, with your gmail account.. [it only works if the company has a misconfiguration!] #bugbountytips #bugbounty How to access to company without being part of it with google oauth, with your gmail account.. [it only works if the company has a misconfiguration!] #bugbountytips #bugbounty](https://pbs.twimg.com/media/ElDQS4oWAAAZQO-.jpg)




