Bk
@_bka_
Infosec enthusiast, Pentester, Network Security, PCAP or didn't happen, Monkey Island addict, bka-sec.bsky.social,
@[email protected]
ID: 758423909242896385
https://blog.kanbach.org/ 27-07-2016 22:08:45
216 Tweet
195 Takipçi
134 Takip Edilen


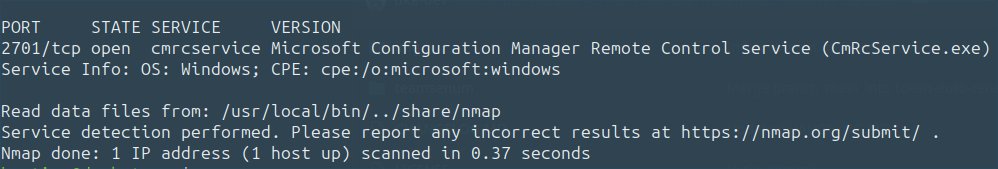
Published my latest Active Directory spotlight on SCCM. /CC: Chris Thompson , Charlie Bromberg « Shutdown » securesystems.de/blog/active-di…




Highly recommend this blog post of nuit - @[email protected] in which he demonstrates how flawed the Kekz headphones are, by reversing the hardware and firmware of this product. #infosec #reverseengineering