Nils Bars
@__nils_
PhD student @ruhrunibochum
ID: 225864969
12-12-2010 17:12:50
22 Tweet
152 Takipçi
123 Takip Edilen


is-eqv.bsky.social and I just published the source code of our hypervisor-based snapshot fuzzer for complex network targets (+ vulns in firefox): github.com/RUB-SysSec/nyx…. Check it out!


This is what DJI’s Drone-ID packets look like. every drone broadcasts this data all the time. we managed to receive + decode the packets over the air. no encryption. (we saw some confusion around that before) merlinchlosta 1/n





Interested in #fuzzing browser JIT compilers? @bernhl will present our paper on differential fuzzing to find subtle miscomputation bugs in JS JIT compilers tomorrow at 11:30 in track 1E at ACM CCS 2025 2022! Paper: mu00d8.me/paper/bernhard… cc Tobias Scharnowski Tim Blazytko Thorsten Holz

Interested in drones and their security? Nico Schiller just presented our work at #NDSS23 If you missed the talk, paper’s at ndss-symposium.org/wp-content/upl…


Das Team um Nico Schiller und Thorsten Holz hat die Ergebnisse zur #Drohnen-Sicherheit auf dem @ndsssymposium vorgestellt. Gefördert wurden die Arbeiten von DFG public | @[email protected] im Rahmen von CASA - Cluster of Excellence for Cyber Security und @bmbf_bund. Mehr dazu: news.rub.de/wissenschaft/2…


Humbled and grateful that our paper Fuzztruction received a Distinguished Paper Award and was the runner up to the Internet Defense Prize USENIX Security #usesec23 Find the paper at usenix.org/conference/use… Thanks Moritz Schloegel, Tobias Scharnowski, Nico Schiller, Thorsten Holz


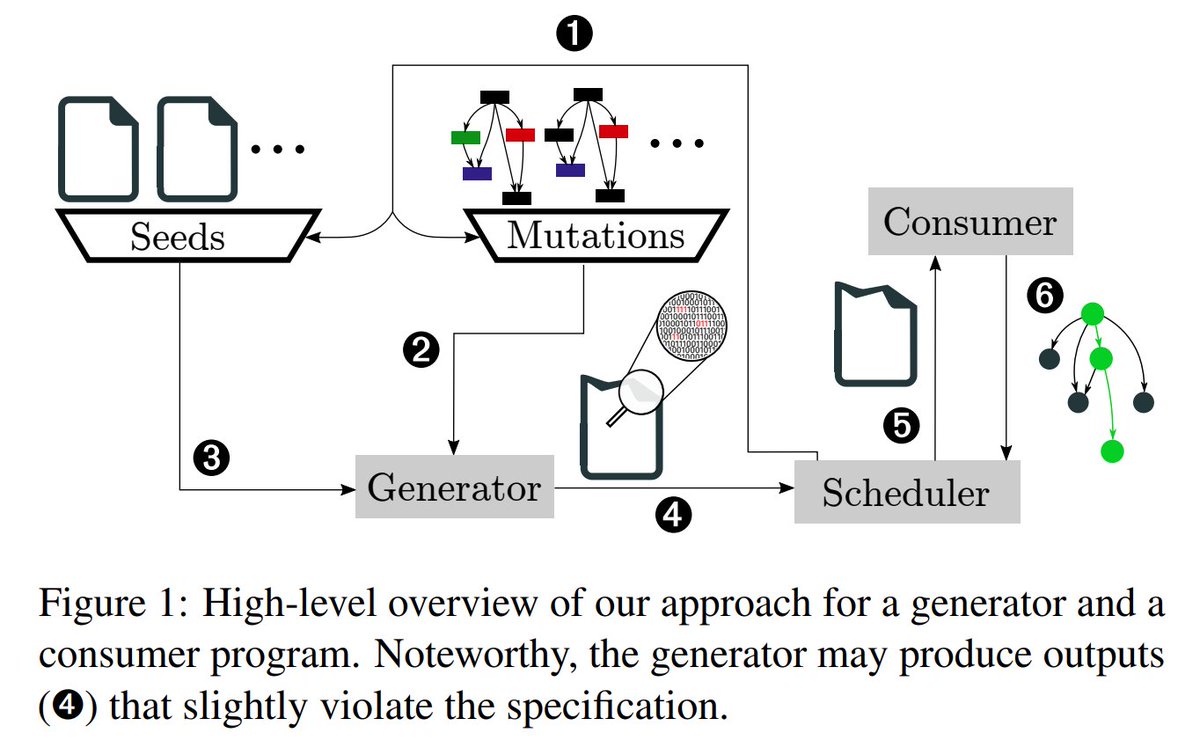
.Moritz Schloegel et al.: No Peer, no Cry. Network Application Fuzzing via Fault Injection mschloegel.me/paper/bars2024… [PDF]
![Enno Rey (@enno_insinuator) on Twitter photo .<a href="/m_u00d8/">Moritz Schloegel</a> et al.:
No Peer, no Cry. Network Application Fuzzing via Fault Injection
mschloegel.me/paper/bars2024… [PDF] .<a href="/m_u00d8/">Moritz Schloegel</a> et al.:
No Peer, no Cry. Network Application Fuzzing via Fault Injection
mschloegel.me/paper/bars2024… [PDF]](https://pbs.twimg.com/media/GWZTjN8WMAEEbOM.png)